Abstract
Smart grid (SG) recently acquired considerable attention due to their utilization in sustaining demand response management in power systems. Smart meters (SMs) deployed in SG systems collect and transmit data to the server. Since all communications between SM and the server occur through a public communication channel, the transmitted data are exposed to adversary attacks. Therefore, security and privacy are essential requirements in the SG system for ensuring reliable communication. Additionally, an AuthentiCation (AC) protocol designed for secure communication should be lightweight so it can be applied in a resource-constrained environment. In this article, we devise a lightweight AC protocol for SG named LACP-SG. LACP-SG employs the hash function, “Esch256”, and “authenticated encryption” to accomplish the AC phase. The proposed LACP-SG assures secure data exchange between SM and server by validating the authenticity of SM. For encrypted communication, LACP-SG enables SM and the server to establish a session key (SEK). We use the random oracle model to substantiate the security of the established SEK. Moreover, we ascertain that LACP-SG is guarded against different security vulnerabilities through Scyther-based security validation and informal security analysis. Furthermore, comparing LACP-SG with other related AC protocols demonstrates that LACP-SG is less resource-intensive while rendering better security characteristics.
Keywords: authentication, smart grid, AEAD, privacy, session key, ROM
1. Introduction
The Industrial Internet of Things (IIoTs) promises to elevate many communication paradigm innovations, focusing on industrial applications. Particularly, IIoT-based smart grid (SG) technology is envisioned to be a vital part of the next-generation power grid system. An SG mainly comprises four elements: sensing, control, actuation, and communication systems. The sensing and communication processes are performed by smart meters (SMs), which are the significant components of an SG, while service providers perform actuation and communication (SPs) [1].
The rapid utilization of SMs has recently been witnessed in smart homes under the SG environment to observe energy utilization in real time. To this end, the SMs communicate with SP on public communication channels. The communication between SMs and SP mandates security and privacy, as the channel used for this communication is prone to various security risks. For instance, an adversary can modify, eavesdrop, and disrupt the communication with consequent degradation in the performance of the SG system [2]. These concerns necessitate the designing of a secure, lightweight, and robust authentication (AC) protocol to guarantee information communication among the honest participants in the SG system while preserving the privacy of the entities.
1.1. Security Requirements in SG Systems
An SM transmits electricity usage information periodically to SP via the public internet. Therefore, the following security requirements are imperative for the smooth working of the SG system [3,4].
1.1.1. Security
Firstly, the SG system contains a large number of SMs. Thus, an SP must check the authenticity of the SM before commencing the information exchange process. It is worth noticing that, by authentication, the authenticity of the deployed SMs in the SG system can be verified. Therefore, the authentication protocol should be able to resist various security attacks, such as denial-of-service (DoS), SM capture, ephemeral secret leakage (EPSL), device impersonation (DIMP), man-in-the-middle (MIDM), de-synchronization (DeS), privilege-insider (PrI), replay, and SP impersonation (SPI) attacks [5]. After accomplishing the authentication process, SM and SP need to create a common session key (SEK) to protect the communicated information. Secondly, the authentication protocol needs to guarantee the authenticity of the SM and SP, verify the data’s integrity, and ensure non-repudiation. Thirdly, by capturing an SM by an adversary, the procured sensitive information from the memory of the captured SM should not breach the security of the communication between other SMs and SP [6,7].
1.1.2. Efficiency
In general, an SP has sufficient computational resources and can process a specific volume of information. However, many SMs communicate with SP concurrently in the SG system, requiring significant computational resources. Moreover, SMs are resource-limited devices with limited computational, communication, and energy resources. Thus, it is imperative to devise a resource-efficient authentication protocol that requires the least computational resources of SP and SM during the authentication process [4,8].
2. Related Work
Security and privacy are the critical parameters of concern for the SG systems. Various security schemes have been proposed to cope with the security challenges in the SG system [9,10]. Li et al. [4] proposed an AC mechanism, which is in-efficacious in thwarting replay, MIDM, and EPSL attacks. In addition, the proposed scheme is incapable of rendering MA and anonymity features. Kumar et al. [11] proposed an AC mechanism for the SG environment employing elliptic curve cryptography (ECC) and SHA. However, the scheme of Kumar et al. is incapable of restraining MIDM device impersonation. DIMP and EPSL attacks are unable to ensure mutual authentication (MA) and the security of SEK. An authentication protocol for the SG environment is presented in [12], using PUF and SHA. Similarly, a secure communication protocol for the SG environment is presented in [13], which is unable to withstand DoS and EPSL attacks. An ECC, XOR, and SHA-based lightweight AC protocol for the SG environment is presented in [14], which cannot withstand various security attacks. An authentication and SEK establishment scheme is propounded in [15], utilizing ECC, XOR, and SHA. The authors in [16] propounded a reliable AC protocol using ECC for the SG infrastructure that can hinder different security threats. In this paper, we propose a physical unclonable function (PUF)-based AC mechanism for the SG system. Li et al. [4] devised a pairing-based message AC protocol for the SG environment, unable to withstand the MIDM, DoS, EPSL, and impersonation attacks and incapable of providing security for SEK. Chen et al. [3] propounded a BP-based AC protocol for SG environments, incapable of resisting EPSL and impersonation attacks and incapable of ensuring the security of SEK. The security framework proposed in [17] cannot resist the DeS attack. An AE-based security framework is presented in [18], and its security is proved through the AVISPA. A detailed summary of various AC protocols or schemes propounded for the SG environment is presented in Table 1.
Table 1.
Summary of various AC protocols.
| AC/AKE Protocol | Shortcomings/Security Vulnerabilities |
|---|---|
| Wu et al. [19] | Unable to thwart MIDM and EPSL attacks. Incapable of rendering anonymity and PFS features. |
| Mahmood et al. [20] | In-efficacious in preventing DoS, impersonation, PrI, replay, MIDM, and EPSL attacks. |
| Dariush et al. [21] | In-efficacious in resisting DoS attack. Incapable of rendering SM’s anonymity and SEK security. |
| Banerjee et al. [22] | Unable to render identity protection and traceability. |
| Wazid et al. [23] | Exposed to DeS attack. Incapable of rendering revocability and formal validation. |
| Odelu et al. [24] | In-efficacious in preventing DoS, MIDM, and impersonation attacks. Unable to assure SM’s anonymity. |
| Xie et al. [25] | In-efficacious in resisting replay and impersonation attacks. Incapable of rendering forward secrecy. |
| Li et al. [4] | In-efficacious in thwarting replay, MIDM, EPSL attacks. Incapable of rendering MA and anonymity features. |
| LACP-SG | Specialized hardware is required to accomplish the PUF-based AC process. In the future, we will use the AEAD schemes for designing the blockchain-enabled authentication frameworks. |
Authenticated encryption with associative data (AEAD), lightweight cryptography (LWC), advance encryption standard (AES), mutual authentication (MA), perfect forward secrecy (PFS), exclusive-OR (XOR), bi-linear paring (BP), elliptic curve cryptography (ECC), authentication and key exchange (AKE), physical unclonable function (PUF), secure hash algorithm (SHA).
2.1. Motivation
Most of the AC protocols in the existing literature are devised using standardized symmetric encryption, such as AES, and public-key cryptography, such as ECC. These standardized cryptographic primitives are computationally expensive for resource-limited devices [14,26]. Moreover, most AC protocols are susceptible to various security risks, including DeS, replay, impersonation attacks, etc., as summarized in Section 2. Therefore, it is imperative to devise a secure and lightweight AC protocol for the SG systems.
Various AEAD schemes are devised to enable encryption and decryption services in resource-limited IoT devices. The main features of AEAD schemes are given to clarify why adopting the LWC primitives is essential when devising an AC protocol. This property of AEAD schemes makes them efficacious in reducing the encryption/decryption operations required to perform the AC process. (i) LWC-based AEAD schemes achieve message authenticity, integrity, and confidentiality simultaneously with a single encryption/decryption operation. (ii) AEAD schemes demand less computational and energy resources with reduced message overhead. (iii) The LWC-based hash function (Esch256) demands fewer computational resources than the existing hash functions while proffering the same security level.
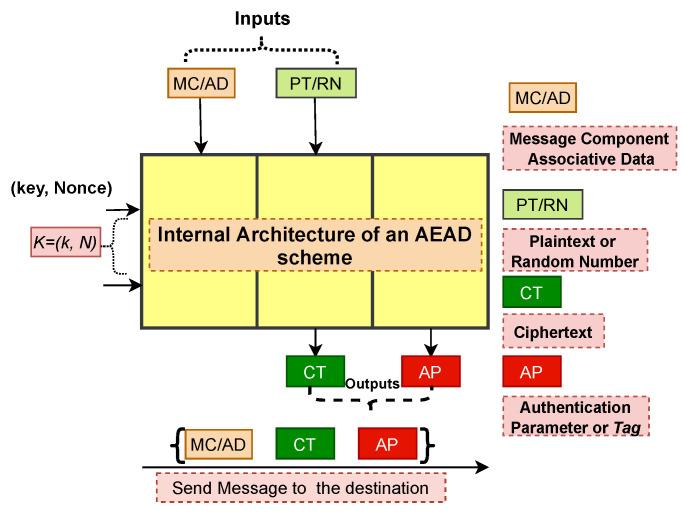
Figure 1 presents the high-level working of an AEAD scheme, which is the base mechanism of the proposed AC protocol. Here, the AEAD scheme at the source node accepts the key along with associative data (), initialization vector/nonce, and plaintext as inputs to return output in the form of ciphertext () and authentication parameters (). Moreover, the source generates a message with credentials and sends this message to the destination to accomplish MA. In the proposed protocol, comprises the temporary identity of the source node, i.e., . SP uses the temporary identity to find the record associated with the source from its memory. is obtained after encrypting the random numbers and other parameters used in the construction of SEK. At the destination, decryption is performed by using the AEAD scheme. The AEAD scheme generates the and after taking the same input parameters as taken at the source node. To authenticate the validity of the obtained message, the destination node checks the condition . If it holds, the received message is valid. We adopt the same methodology to propose a secure and lightweight AC protocol for the SG environment.
Figure 1.
Message generation at source node using AEAD scheme.
2.2. Research Contributions
The paper comprises the subsequent contributions.
This paper proffers a new lightweight AC protocol for SGs, called LACP-SG, which utilizes “Counter Mode Encryption with authentication Tag” (COMET) [27] along with a lightweight hash function “Esch256”. LACP-SG enables SP to check the authenticity of SM installed in the SG system before commencing the information exchange process. In addition, LACP-SG enables both the SM and SP to generate a shared SEK for future indecipherable communications.
The random oracle model (ROM) is utilized to corroborate the security of the established shared SEK. Moreover, security analysis utilizing the Scyther tool is executed to demonstrate that LACP-SG is resilient against MIDM, DeS, and replay attacks. Informal security is performed to illustrate that LACP-SG is resistant to SM capture and impersonation attacks. Moreover, LACP-SG allows the sensitive credentials associated with SM to be stored in ciphertext form in the database of SP, thereby restraining the PrI attack.
The meticulous comparative analysis is conducted to illustrate that LACP-SG renders enhanced security features while requiring low communication, storage, and computational overheads, respectively, than the related eminent AC protocols.
The subsequent paper is formed as follows. The system models, such as the network and attack model for LACP-SG, are illustrated in Section 3. Section 4 explicates the preliminary knowledge used in designing LACP-SG. The propounded LACP-SG is explicated in Section 5. The resiliency of LACP-SG against various attacks is furnished in Section 6. The significance of the LACP-SG is studied in Section 7. The paper concludes with concluding statements in Section 8.
3. System Model
3.1. Network Model
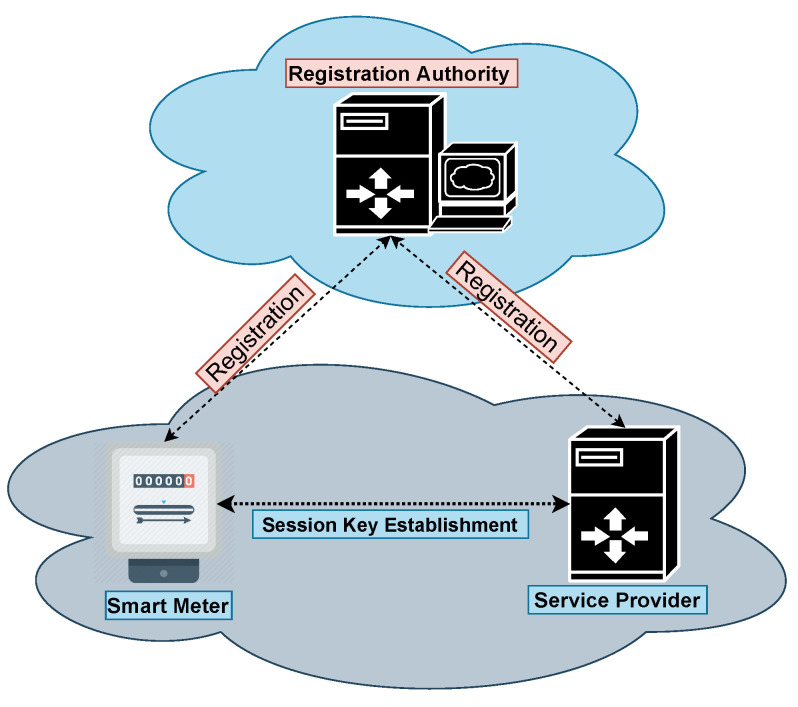
For the authentication process, we contemplate the SG network model as depicted in Figure 2, which constitutes registration authority (RA), smart meter (), where “n” symbolizes the installed SMs and , where “N” symbolizes the number of SPs installed by RA. RA is liable for the registration of . stores the data or information sent by . pre-loads the confidential credentials into memory before its deployment in the SG environment. collects the sensitive information and transmits the accumulated information to via an openly available wireless channel, which is imperiled by different security vulnerabilities. Thus, ensuring the transmitted information’s integrity and confidentiality is inevitable. In the subsequent sections, the propounded secure AC protocol is elaborated, which validates the authenticity of the deployed . For encrypted communications, it sets up a secret key between and .
Figure 2.
SG network.
3.2. Threat Model
We are considering the broadly utilized Dolev–Yao (DY) model for the proposed LACP-SG for the SG system [16,28]. The adversary is able to alter and remove the content of the captured message. Furthermore, after updating the content of the captured message with malicious code, can generate a malicious message. Network entities such as can be physically compromised by . Moreover, can obtain sensitive data loaded in the memory of . In addition to this, can use the procured information to carry out various attacks. In addition, is contemplated as the trusted entity of the SG system. As in the DY model, in the CK-adversary model, can not only intercept communications in the SG environment, but the secret parameters, such as session keys and state and private keys, can also be compromised by .
4. Preliminaries
4.1. COMET
We use CHAM-based block cipher COMET-128 as the encryption/decryption scheme in the proposed LACP-SG. COMET is an AEAD scheme [27]. We express the encryption and decryption of COMET by (, ) = and (, ) = , respectively, where K, N, , , , and signifies “secret key”, “nonce”, “associative data”, “ciphertext”, “authentication parameter”, and “plaintext”, respectively. COMET decryption process will retrieve the plaintext if the condition holds.
4.2. Esch256
We use the hash function “Esch256” in designing LACP-SG, which is faster than SHA-160/256 and requires fewer computational resources. In addition, Esch256 renders the same functionality as provided by SHA-160/256 with an output size of 256 bits. Moreover, Esch256 renders enhanced security features.
4.3. Physical Unclonable Function
(PUF) is a one-way function. PUF produces a unique output (response) after taking the challenge as the input parameter. The operation of PUF can be represented as .
4.4. Fuzzy Extractor
(FE) comprises two algorithms, namely, Generator and Reproducer . The probabilistic algorithm produces key and Helper Data by taking bio-metric R of user, i.e., . is a deterministic algorithm that reproduce by considering the inputs R and , if the condition holds, where is the hamming distance between R and and is the error tolerance.
5. The Proposed LACP-SG Protocol
The proposed LACP-SG protocol comprises four phases: (1) SM deployment phase; (2) SP Deployment Phase; (3) AC Phase; and (4) New SM Deployment. The subsequent subsections explain the details of the designed LACP-SG protocol. It is assumed that all the participants in the SG environment are time-synchronized to cope with replay attacks. Table 2 lists the notations utilized in devising LACP-SG.
Table 2.
Notations used in LACP-SG.
| Notation | Description |
|---|---|
| , | Smart meter (SM) and Service Provider (SP), respectively |
| , , R | Physically unclonable function, challenge, and response, respectively |
| Common parameter of SP, which is known only to SP | |
| Temporary-Identity of smart meter (SM) | |
| , , | Real-Identity SM, SP, and secret key of SP |
| and | Ciphertext and authentication parameter () |
| and | Plaintext and authentication parameter () |
| , | Timestamps in LACP-SG’s AC phase |
| , | Received and maximum delay time of a message |
| , | designates the associative data |
| , , | Signifies the nonce or initialization vector |
| , | designates COMET based encryption/decryption of message
employing secret |
| , , | Signifies based key production, helper data, and key re-production function, respectively |
| , , | designates the random numbers |
| , ‖, , , | Signifies attacker/adversary, concatenation, hash-function, and XOR, respectively |
| , | “Advantage of and ciphertext integrity” |
| “Online pseudo-random permutation chosen-plaintext attack” |
5.1. SP Deployment Phase
The SP deployment phase is accomplished by RA to deploy . For this, RA picks a unique identity and computes the secret key for the deployed in SG environment as , where is the private key of RA. In addition, RA stores the list of credentials {, } in the temper-resistance database of . RA also stores the credentials {, } in its own database.
5.2. SM Deployment Phase
deployment phase (SDP) is executed by RA. RA stores the secret credentials before deployment in the SG environment by performing the trailing necessary steps.
5.2.1. Step SDP-1
picks a real identity of size 128 bits and a random number of size 128 bits. fabricates a message with parameters {, } and sends it to RA through a secure channel. RA picks a challenge parameter and computes temporary identity = ‖ , where = ‖. In addition to this, RA computes and determines = , where and are derived by splitting U into two same-sized chunks, each with the size of 128 bits. RA sends the credentials {, } to via the secure channel.
5.2.2. Step SDP-2
After receiving the parameters {, } from RA, generates a response by using function as = . In addition, by using computes , = and sends to through a protected channel. Finally, keeps the credentials {, , , } in its own memory.
5.2.3. Step SDP-3
Upon obtaining from , RA computes = (‖) . Finally, RA stores the parameters {, } in the database of .
5.3. AC Phase
In AC phase (ACP), achieves MA with . Moreover, establishes a secret SEK with to achieve encrypted communication. The trailing steps provide a detailed explanation of the AC phase.
5.3.1. Step ACP-1
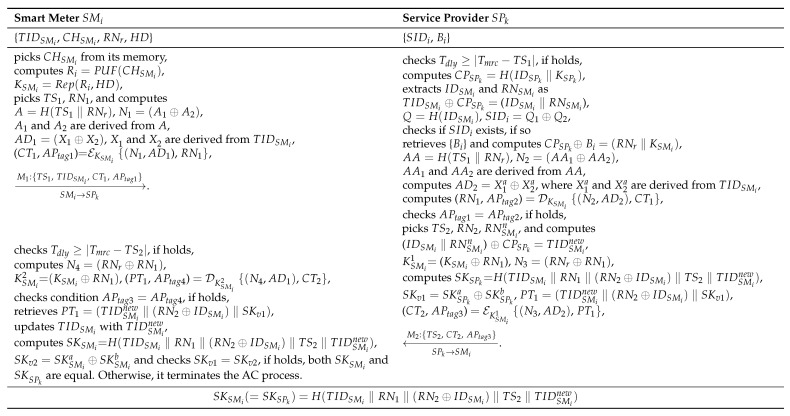
retrieves from its memory, stored in the memory during its deployment phase and computes . regenerates by using as = , where the size of is 128 bits. In addition, selects the current timestamps with size 32 bits, the random number with size 128 bits, and computes and nonce , where and are procured by splitting A into two same-sized chunks, each with the size of 128 bits. In addition, computes the associative data , where and are two equal parts of . The size of and is 128 bits. by using COMET computes () = , , where , , and denote ciphertext, authentication parameter (Tag), and plaintext, respectively. Finally, constructs a message : {, , , } and sends to through a public communication channel.
5.3.2. Step ACP-2
Upon procuring form , checks the condition to validate the freshness, where is the allowed time delay, is the received time, and designates the generation time. If the condition holds, considers as the authentic message and proceeds with the AC process. Otherwise, discards and obstructs the AC process. determines the common parameter as = ‖. Moreover, retrieves and by computing = (‖), where is received with and is computed at . Additionally, picks the retrieved and computes and , where and are two chunks of each of 128 bits. In addition, checks if is located in its database (memory). If is found, retrieves the credential {} corresponding to , stored in the database (memory) of . In addition to this, computes = ‖. Additionally, determines = ‖ and nonce = , where and are procured by splitting into two same-sized chunks, each with the size of 128 bits. Furthermore, computes = , where and are two equal parts of . Finally, by using COMET computes (, ) = , , where , , , , and denote associative data, nonce, ciphertext, authentication parameter (Tag), and plaintext, respectively. To validate the authenticity of , checks the condition . If it holds, considers as the authentic message, which is received from a valid . Otherwise, discards and aborts the AC process.
5.3.3. Step ACP-3
After substantiating the authenticity of , picks timestamp , , , and computes the new temporary identity as (‖) = , where is real identity of and is a new random number. Moreover, computes = ( ), which is used in the encryption process. For encrypted communication in future, computes SEK as = ‖‖ ‖‖ and calculates = . Furthermore, determines , and . In addition to this, by using COMET, computes (, ) = , , where , , , , and denote associative data, nonce, ciphertext, authentication parameter, and plaintext, respectively. Finally, contrives a message : {, , } and dispatches to via an open/wireless channel.
5.3.4. Step ACP-4
After acquiring from , checks the condition to validate the freshness of . If is fresh, determines , = , and by using COMET computes (, )= , , where , , , and denote associative data, nonce, ciphertext, authentication parameter (Tag), and plaintext, respectively. Moreover, checks the condition . If it holds, procures the plaintext from the decryption process. For indecipherable communication, computes the SEK as = ‖‖ ‖‖. In addition to this, calculates = and checks the condition . If it holds, both and are equal. Otherwise, it terminates the AC process. Finally, updates with in its own memory. Figure 3 summarizes the LACP-SG AC phase.
Figure 3.
LACP-SG authentication phase.
5.4. New SM Deployment Phase
RA performs the subsequent steps to deploy a new .
5.4.1. Step SDP-1
picks a real identity and and sends {, } to RA through a protected channel. RA picks a new challenge and computes the new temporary identity = ‖ . Moreover, RA computes and derives , where and are derived by splitting into two same-sized chunks, each with the size 128 bits. RA sends the credentials {, } to via a secure channel.
5.4.2. Step SDP-2
After receiving a challenge from RA, generates a response by using the PUF function as . In addition, by using computes , = and sends to RA via secure channel. Furthermore, stores {, , } in its own memory. Upon receiving from , RA computes. In addition, computes = (‖) . Finally, RA stores the parameters {, } in the database.
6. Security Analysis
6.1. Informal Security Analysis
6.1.1. Anonymity and Untraceability
Assume eavesdrops the communicated messages, such as : {, , , } and : {, , }, which are exchanged during the AC phase of the proposed LACP-SG. cannot determine the real identity of SM of SP, which are and , respectively, from the captured and . by capturing and cannot procure the real identities of SM and SP.
6.1.2. Replay Attack
after expropriating all the messages, such as : {, , , } and : {, , } tries to regenerate the captured messages to obtain helpful information from the participants of the AC phase. However, we assume the system is time-synchronized, and each message bears the newest timestamp and random numbers. cannot frame the replay attack because the entities and verify the newness/oldness of the obtained message by confirming the condition and , respectively. If the obtained transmission is delayed, the entity of the receiving will dump the obtained message. In this way, the proposed LACP-SG detects the replayed messages and discards such received messages. Hence, LACP-SG is protected against replay attacks.
6.1.3. DeS Attack
The proposed LACP-SG renders resistance against DeS attack. For anonymous communication, uses , which is updated by during the accomplishment of every new AC session. constructs by concatenating and a fresh random number , i.e., , where remains constant and is updated to . Suppose drops during the execution of the AC phase. This action of cannot affect the execution of the new AC session because is constant, which is extracted by to compute the . is used to find the record at related to . So, LACP-SG is capable of resisting the DeS attack.
6.1.4. Privilege Insider Attack
To accomplish the authentication phase in the proposed LACP-SG scheme, stores the parameters {, } in the database. Thus, to fabricate a valid messages, such as : {, , , } and : {, , }, it is imperative for to compute = ‖. However, without knowing the secret key of , it is hard for to extract and , which are required to construct and . Hence, LACP-SG can resist the PrI attack.
6.1.5. MIDM Attack
Assume that expropriates all the exchanged messages and between the entities during the AC phase over the wireless/open communication channel. Now, may attempt to reconstruct the seized messages to make the participants of the system believe that the received messages are generated by licit entities. To simulate a licit message on behalf of , requires to have all the confidential/secret credentials of , i.e., {, , }. Similarly, needs to extricate all the secret/confidential parameters of to construct a valid response message on behalf of . However, without having all the confidential credentials of and , it is impractical for to construct a valid message. Therefore, LACP-SG can restrain MIDM attacks.
6.1.6. Impersonation/Modification/Injection Attack
To impersonate as , A has to regenerate the message on behalf of to make believe that the message is licit and obtained from an honest . Now, suppose attempts to generate with valid credentials. However, to generate , requires knowing the confidential credentials of . However, cannot produce a valid message in polynomial time without knowing the secret credentials to emulate as legitimate . Similarly, requires knowing the confidential credentials of . Therefore, LACP-SG is protected against and impersonation attacks.
6.1.7. Key Compromise Impersonation Attack
In this attack, tries to impersonate as a valid by compromising the long-term secret key of . However, to construct a valid message : {, , , }, it is necessary for to obtain the secret parameters, such as and . Thus, without having these confidential parameters, it is hard for to impersonate a valid . Similarly, without having the confidential parameters of , cannot impersonate a licit . In this way, LACP-SG can resist key compromise impersonation attacks.
6.1.8. Known Session-Specific Temporary Information Leakage/EPSL Attack
According to the CK-adversary model, can compromise the secret credentials (Long Term Secrets (LTS), Ephemeral Secrets (ES)), and session states aside from all the actions allowed under the DY model. In LACP-SG, the session key is created using both LTS and ES, i.e., = . Therefore, it is imperative for to guess that both LTS and ES construct the session key.
6.1.9. SM Capture/Memory Modification Attack
According to the DY threat model, can seize some of the SMs from in the SG environment. can extricate the secret credentials by using a power analysis attack kept in the memory of SM. However, the parameters , , and are unlike for all SMs installed in the SG environment. Therefore, by capturing some of the installed SMs, cannot compromise the security of the whole SG environment. Hence, LACP-SG is resilient against SM capture attacks.
6.2. ROM-Based Formal Security Analysis
This section provides a ROM-based analysis of the SEK security between and during the execution of the AC phase of LACP-SG. The subsequent components are described in the ROM model.
Participants: Suppose that , , and represent instances , , and of the participants RA, , and , denoted as oracles.
Accepted state: When an instance acquires the last message, it will be in the accepted state. The session identification (Sid) of for the current session prescribes the ordered sequence of all exchanged messages (i.e., messages sent/received by ).
Partnering: Two instances and are partners only if both are in an acceptable state and share similar session keys.
Freshness: is unable to obtain the SEK established between and by running the query presented in Table 3.
Table 3.
ROM-based queries.
| Query | Purpose |
|---|---|
| Perpetration of this query enables to seize all the transmitted messages between and . |
|
| Perpetration of this query enables to yield an active attack by dispatching a message to and also respond to accordingly. |
|
| Perpetration of this query enables to get the shared SEK, utilized to guarantee the secure transmission between and its interrelated entity. |
|
| Perpetration of this query helps to acquire the secret/private parameters loaded in the storage of by operating PA attack. |
|
| Perpetration of this query enables to ascertain whether the guessed SEK is licit or random output, just like the outcome of a flipped coin, say C. |
Adversary: can fully control and seize all the messages and alter, falsify, and infiltrate messages by employing the queries expressed in Table 3. can execute the hash function , referred to as random oracle .
Definition 1.
Online chosen ciphertext attack (OCCA3) advantage of , which is executing against an AEAD scheme in polynomial-time , can be defined as follows.
(1)
Theorem 1.
Let run against LACP-SG in to derive the established SEK between and during the AC phase. Let signify Esch256 queries, designates the range space of Esch256 output, represents PUF quires, designates the range space of PUF output, and is the advantage in compromising the security of an online AEAD scheme (COMET) (Definition 1). The maximum advantage of for compromising the security of SEK, established between and , can be described as follows:
(2)
Proof.
The succeeding five games are executed to prove Theorem 1. We heed the identical means to establish the proof of Theorem 1 as followed in [29,30,31,32,33]. In addition to this, we characterize the advantage in compromising the security of SEK by = , where indicates the possibility of a circumstance where can achieve/win the game. LACP-SG is defended if is insignificant.
: In this game, performs an active attack against LACP-SG under ROM. at the commencement of guesses the bit randomly. Then, trailing can be achieved
(3) : In , makes the query to effectuate the eavesdrop attack. By effectuating eavesdrop attack during the execution of AC phase, can intercept all the exchanged messages, such as : {, , , } and : {, , }. effectuates at the end of this game and validates whether the outcome of the query is a random number or a real session key, i.e., = , where . The session key is produced in the proposed LACP-SG using the LTS and ES. Therefore, to reveal the session key established between and , it is imperative for to guess both the ES and LTS simultaneously. However, it is impractical for to procure all the secret parameters by capturing and . So, the winning chance of this game for will not increase by effectuating the eavesdrop attack:
(4) : In this game, the aim of is to deceive an entity to receive a mutated message. is authorized to make various queries to check the presence of the hash collisions. All the exchanged messages, such as : {, , , } and : {, , } during the AC phase indirectly include the associative data and nonce, and temporary identities, which are protected by the collision-resistant Esch256 hash function. Therefore, there will be no collision when performs queries. The consequences of the birthday paradox confer
(5) : This game is considered a continuation of that simulates PUF queries. According to , it follows that
(6) : In this game, attempts to construct the session key by capturing and , which are protected by AEAD scheme. In LACP-SG the session key in constructed as = . Therefore, has to procure and , which are encrypted using AEAD scheme (COMET). Moreover, the associative data and the initialization vector used in the encryption process are random. In addition, secret keys are required to decrypt and . It is computationally impractical to perform the decryption process in polynomial time. Due to OCCA3 property (Definition 1), it then follows that
(7) As all the queries are performed, executes the queries to presume bit for winning the game. Thus, we obtain
(8)
(9) From (9), we obtain
(10) By using (8) and (10), we obtain
(11) Through triangular inequality, we obtain
(12) By utilizing (5), (6), (7) and (12), we obtain
(13) □
6.3. Scyther Based Formal Security Verification
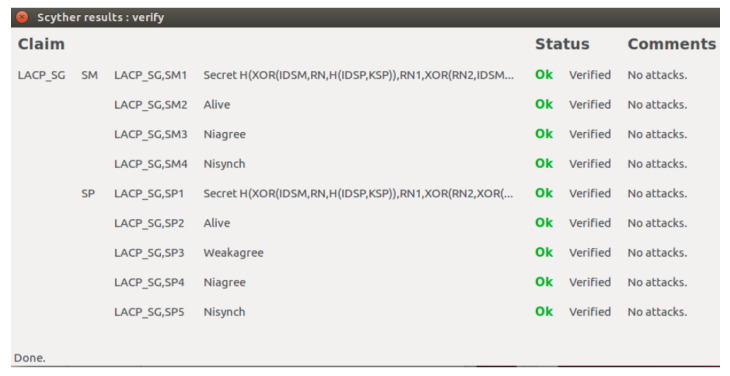
We investigated the formal security of LACP-SG by utilizing the widely adopted validation tools, i.e., Scyther. Scyther is a Python-based software designed to formally analyze the security of the authentication schemes, their security claims, and potential vulnerabilities. Scyther employs the Security Protocol Description Language (SPDL) for describing a devised security scheme and is also utilized to determine the weaknesses of a security scheme by demonstrating any potential threats or risks. In the proposed LACP-SG, two roles are defined, such as and . There are two manually specified claims, such as and , which are validated by Scyther, as shown in Figure 4. In addition, Scyther also generates the claims, such as , , and , which are validated as demonstrated in Figure 4.
Figure 4.
Security analysis of LACP-SG using Scyther.
7. Performance Evaluation
LACP-SG is contrasted with other protocols, such as in Bera et al. [29], Chaudhry et al. [30], Bera et al. [34], Kumar et al. [11], Chaudhry et al. [35], and Mehmood et al. [20]. We use the Python-based library “PyCrypto” along with COMET code to acquire the time complexity of cryptographic primitives and COMET. Table 4 depicts the time complexities of different cryptographic operations.
Table 4.
Time complexity of different cryptographic operations.
| Notations | Operation | Time on R-Pi3 | Time on |
|---|---|---|---|
| ECC-based point multiplication | 2.70 ms | 0.705 ms | |
| Symmetric key encryption | 0.41 ms | 0.015 ms | |
| ECC-based point addition | 0.134 ms | 0.007 ms | |
| One-way hash function (16 bytes) | 0.345 ms | 0.039 ms | |
| Esch256 one-way hash function (32 bytes) | 0.330 ms | 0.032 ms | |
| Physical-unclonable-function | 0.49 s | - | |
| COMET | 0.349 ms | 0.041 ms | |
| Bio-metric key generation and reproduction | 2.70 ms | 0.705 ms |
Time complexities are computed on Quad-core Raspberry Pi-3 (R-Pi3) with CPU @1.2 GHz, and 1GB of RAM″ and “Core(TM) i7-6700 system with CPU @3.40 GHz, and RAM 8 GB” to simulate , respectively.
7.1. Security Comparison
A comparison of the security properties of LACP-SG and other related AC schemes is demonstrated in Table 5. That of Bera et al. [29] cannot restrain the DeS attack, that of Bera et al. [34] is unprotected against the DeS attack, and that of Mehmood et al. [20] is insecure against the DoS, MIDM, PrI, EPSL, RA attacks and does not provide the SEK security. The scheme of Kumar et al. [11] is against DIMP, MIDM, and EPSL attacks and does not provide SEK security. In addition to this, the scheme of Chaudhry et al. [35] is incapable of resisting EPSL, SIMP, DIMP, device capture, and SEK disclosure attacks. Moreover, Chaudhry et al. [30] provide insecure certificate computation, which causes various attacks, such as device capture and DIMP attacks. However, the proposed LACP-SG is secure and protected against various pernicious attacks, such as MIDM and DeS attacks.
Table 5.
Security comparison.
| Features | Chaudhry et al. [30] | Bera et al. [29] | Bera et al. [34] | Mehmood et al. [20] | Kumar et al. [11] | Chaudhry et al. [35] | LACP-SG |
|---|---|---|---|---|---|---|---|
| PrI | ✓ | ✓ | ✓ | × | ✓ | ✓ | ✓ |
| DIMP | × | ✓ | ✓ | ✓ | × | × | ✓ |
| SPI | ✓ | ✓ | ✓ | ✓ | ✓ | × | ✓ |
| DCA | × | ✓ | ✓ | ✓ | ✓ | × | ✓ |
| MIDM | ✓ | ✓ | ✓ | × | × | ✓ | ✓ |
| DeS | ✓ | × | × | ✓ | ✓ | ✓ | ✓ |
| DoS | ✓ | ✓ | ✓ | × | ✓ | ✓ | ✓ |
| RA | ✓ | ✓ | ✓ | × | ✓ | ✓ | ✓ |
| SEKS | ✓ | ✓ | ✓ | × | × | × | ✓ |
| EPSL | ✓ | ✓ | × | × | × | ✓ | ✓ |
| ROM | ✓ | ✓ | ✓ | × | ✓ | ✓ | ✓ |
| MA | ✓ | ✓ | ✓ | ✓ | × | ✓ | ✓ |
| SCER | × | ✓ | ✓ | ✓ | ✓ | × | - |
SCER: secure certificate computation; DCA: device capture attack; ✓: indicates the supported functionality; ×: represents the functionality is not available.
7.2. Communication Overhead Comparison
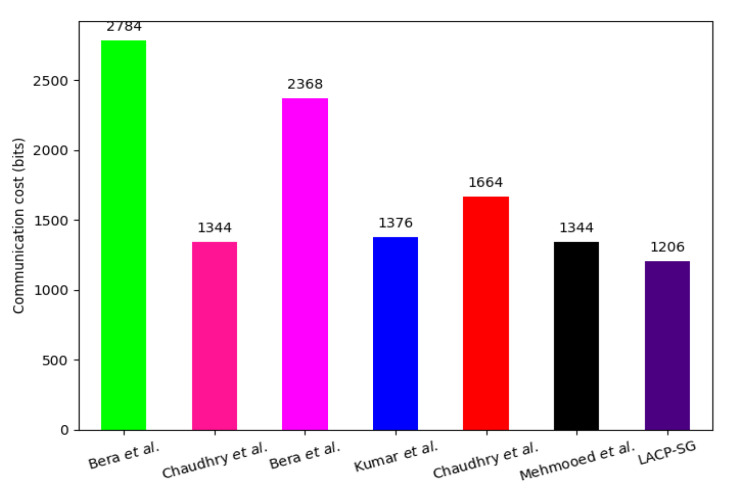
For analyzing the communication overhead that occurred during the AC phase, we suppose that the length of the ECC point, identity, hash function output, initialization vector/random number/nonce, and timestamp are 320, 128, 256, 128, and 32 bits, respectively. There are two messages required to accomplish the AC phase of LACP-SG, i.e., : {, , , }, : {, , }. The sizes of and are {32 + 256 + 128 + 128} = 544 bits and {32 + 512 + 128} = 662 bits. Hence, the communication cost of LACP-SG is {662 + 544} = 1206 bits, which is 56.68%, 10.27%, 49.07%, 12.35%, 27.52%, and 10.27% lesser than the scheme of Bera et al. [29], Chaudhry et al. [30], Bera et al. [34], Kumar et al. [11], Chaudhry et al. [35], and Mehmood et al. [20], respectively. The comparison between LACP-SG and the related AC protocol communication overhead is given in Table 6 and Figure 5.
Table 6.
Communication overhead comparison.
Figure 5.
Communication cost needed to perform the AC phase (single ) [11,20,29,30,34,35].
7.3. Computational Overhead Comparison
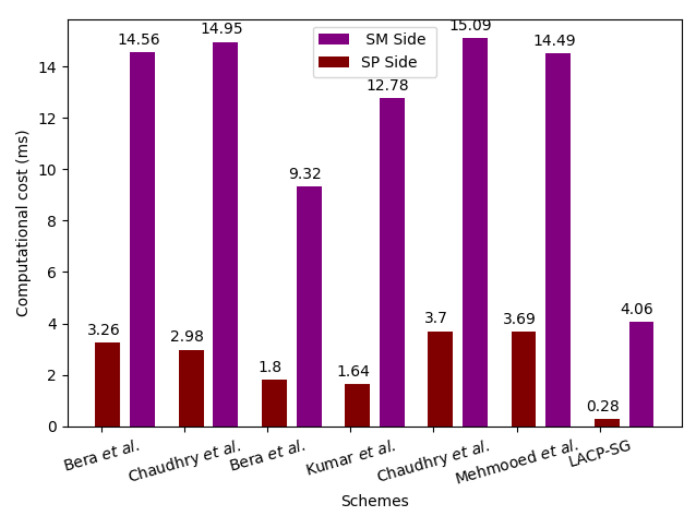
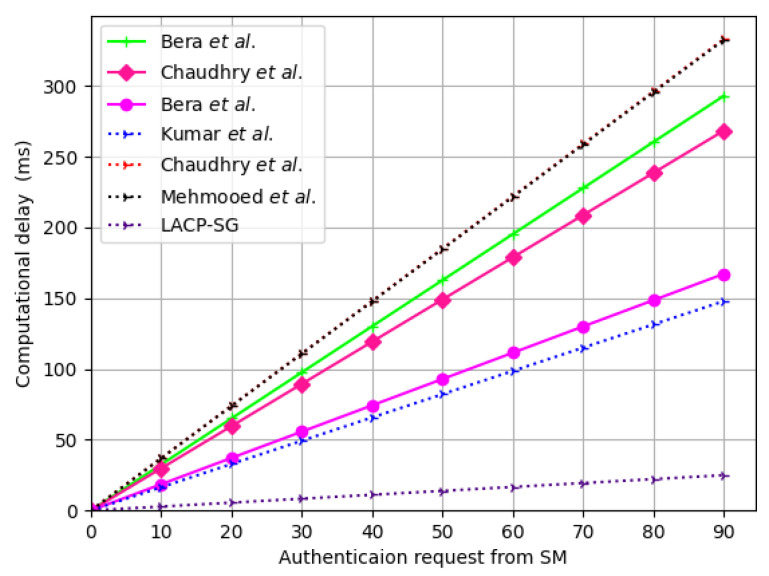
We employ the time complexity of different cryptographic operations, shown in Table 4, to estimate the computational overhead of LACP-SG and relevant AC protocol. LACP-SG requires the computational overhead of ms in the AC phase. The schemes of Bera et al. [29], Chaudhry et al. [30], Bera et al. [34], Mehmood et al. [20], Kumar et al. [11], and Chaudhry et al. [35] require ms, ms, ms, ms, ms, and ms, respectively, which are 75.14%, 75.29%, 60.16%, 69.28%, 76.42%, and 75.63% higher than the proposed LACP-SG, respectively, as shown in Table 7. Moreover, the computational cost needed at the and side is shown in Figure 6, where it is obvious that LACP-SG incurs lesser computational cost than the related AC protocols. Furthermore, Figure 7 illustrates the comparison of the computational cost at with increasing the authentication requests, which are generated by in the SG environment.
Table 7.
Computational overhead comparison.
Figure 6.
Figure 7.
The computational cost increases with the number of authentication requests [11,20,29,30,34,35].
7.4. Storage Overhead Comparison
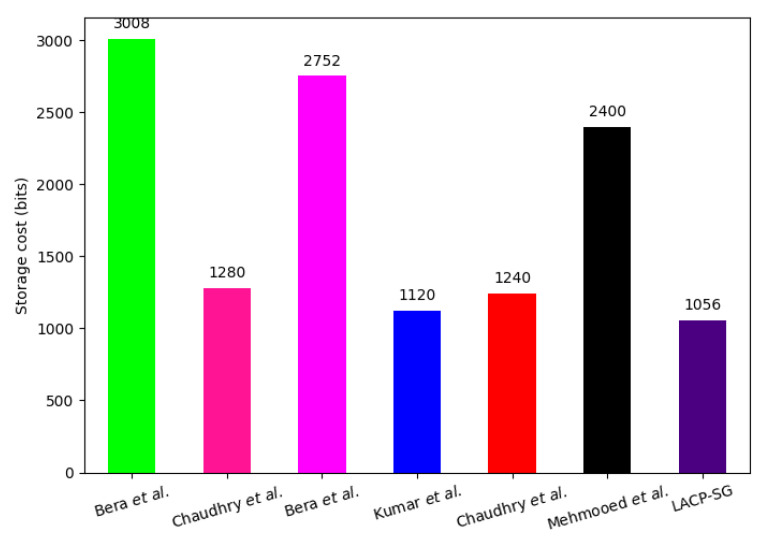
In LACP-SG, the smart meter and requires storing {, , , } and {, , } size of { 256 + 256 + 160} = 672 bits and {128 + 256 } = 384 bits. To execute the AC phase, the aggregated storage overhead of LACP-SG is {672 + 384} = 1056 bits. The schemes of Bera et al. [29], Chaudhry et al. [30], Bera et al. [34], Mehmood et al. [20], Kumar et al. [11], and Chaudhry et al. [35] require storing 3008 bits, 1280 bits, 2752 bits, 1120 bits, 1240 bits, and 2400 bits, respectively, which are 64.89%, 17.5%, 61.63%, 5.71%, 14.84%, 56%, 37.26% higher than the proposed LACP-SG, respectively. The comparison of LACP-SG and the related AC protocols’ storage overhead is given in Figure 8.
Figure 8.
8. Conclusions
This paper presents an AC protocol called LACP-SG, which enables secure communication in the resource-constrained SG environment. To this end, LACP-SG validates the authenticity of the deployed SM and establishes a SEK between the SM and server to accomplish secure communications. The security of the established SEK is validated through ROM-based analysis. Moreover, through Scyther-based analysis, LACP-SG is found to be secure against MIDM and replay attacks. Informal security analysis reveals that the protocol is protected against de-synchronization and SM capture attacks. Finally, a rigorous comparative analysis shows that LACP-SG renders superior security and requires lower computational, storage, and communication cost than the related AC protocols, thereby advocating the feasibility of LACP-SG for SG applications.
Author Contributions
Both authors contributed equally to preparing the article. All authors have read and agreed to the published version of the manuscript.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Funding Statement
The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through Large Groups Project under grant number RGP.2/201/43.
Footnotes
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
References
- 1.Salem F.M., Ibrahim E., Elghandour O. A Lightweight Authenticated Key Establishment Scheme for Secure Smart Grid Communications. Int. J. Saf. Secur. Eng. 2020;10:549–558. doi: 10.18280/ijsse.100415. [DOI] [Google Scholar]
- 2.Kumar P., Lin Y., Bai G., Paverd A., Dong J.S., Martin A. Smart Grid Metering Networks: A Survey on Security, Privacy and Open Research Issues. IEEE Commun. Surv. Tutor. 2019;21:2886–2927. doi: 10.1109/COMST.2019.2899354. [DOI] [Google Scholar]
- 3.Chen Y., Martínez J.F., Castillejo P., López L. A bilinear map pairing based authentication scheme for smart grid communications: Pauth. IEEE Access. 2019;7:22633–22643. doi: 10.1109/ACCESS.2019.2898376. [DOI] [Google Scholar]
- 4.Li X., Wu F., Kumari S., Xu L., Sangaiah A.K., Choo K.K.R. A provably secure and anonymous message authentication scheme for smart grids. J. Parallel Distrib. Comput. 2019;132:242–249. doi: 10.1016/j.jpdc.2017.11.008. [DOI] [Google Scholar]
- 5.Huseinović A., Mrdović S., Bicakci K., Uludag S. A Survey of Denial-of-Service Attacks and Solutions in the Smart Grid. IEEE Access. 2020;8:177447–177470. doi: 10.1109/ACCESS.2020.3026923. [DOI] [Google Scholar]
- 6.Gope P., Sikdar B. Privacy-aware authenticated key agreement scheme for secure smart grid communication. IEEE Trans. Smart Grid. 2018;10:3953–3962. doi: 10.1109/TSG.2018.2844403. [DOI] [Google Scholar]
- 7.Tanveer M., Ahmad M., Khalifa H.S., Alkhayyat A., Abd El-Latif A.A. A new anonymous authentication framework for secure smart grids applications. J. Inf. Secur. Appl. 2022;71:103336. doi: 10.1016/j.jisa.2022.103336. [DOI] [Google Scholar]
- 8.Tanveer M., Abbas G., Abbas Z.H., Bilal M., Mukherjee A., Kwak K.S. LAKE-6SH: Lightweight User Authenticated Key Exchange for 6LoWPAN-Based Smart Homes. IEEE Internet Things J. 2021;9:2578–2591. doi: 10.1109/JIOT.2021.3085595. [DOI] [Google Scholar]
- 9.Tanveer M., Khan A.U., Shah H., Alkhayyat A., Chaudhry S.A., Ahmad M. ARAP-SG: Anonymous and Reliable Authentication Protocol for Smart Grids. IEEE Access. 2021;9:143366–143377. doi: 10.1109/ACCESS.2021.3121291. [DOI] [Google Scholar]
- 10.Tanveer M., Khan A.U., Kumar N., Naushad A., Chaudhry S.A. A Robust Access Control Protocol for the Smart Grid Systems. IEEE Internet Things J. 2021;9:6855–6865. doi: 10.1109/JIOT.2021.3113469. [DOI] [Google Scholar]
- 11.Kumar N., Aujla G.S., Das A.K., Conti M. ECCAuth: A Secure Authentication Protocol for Demand Response Management in a Smart Grid System. IEEE Trans. Ind. Inform. 2019;15:6572–6582. doi: 10.1109/TII.2019.2922697. [DOI] [Google Scholar]
- 12.Kaveh M., Mosavi M.R. A lightweight mutual authentication for smart grid neighborhood area network communications based on physically unclonable function. IEEE Syst. J. 2020;14:4535–4544. doi: 10.1109/JSYST.2019.2963235. [DOI] [Google Scholar]
- 13.Kim S., Kwon E.Y., Kim M., Cheon J.H., Ju S.H., Lim Y.H., Choi M.S. A secure smart-metering protocol over power-line communication. IEEE Trans. Power Deliv. 2011;26:2370–2379. doi: 10.1109/TPWRD.2011.2158671. [DOI] [Google Scholar]
- 14.Abbasinezhad-Mood D., Nikooghadam M. Design and hardware implementation of a security-enhanced elliptic curve cryptography based lightweight authentication scheme for smart grid communications. Future Gener. Comput. Syst. 2018;84:47–57. doi: 10.1016/j.future.2018.02.034. [DOI] [Google Scholar]
- 15.Ostad-Sharif A., Abbasinezhad-Mood D., Nikooghadam M. A robust and efficient ECC-based mutual authentication and session key generation scheme for healthcare applications. J. Med. Syst. 2019;43:10. doi: 10.1007/s10916-018-1120-5. [DOI] [PubMed] [Google Scholar]
- 16.Chaudhry S.A., Nebhen J., Yahya K., Al-Turjman F. A Privacy Enhanced Authentication Scheme for Securing Smart Grid Infrastructure. IEEE Trans. Ind. Inform. 2021;18:5000–5006. doi: 10.1109/TII.2021.3119685. [DOI] [Google Scholar]
- 17.Far H.A.N., Bayat M., Das A.K., Fotouhi M., Pournaghi S.M., Doostari M. LAPTAS: Lightweight anonymous privacy-preserving three-factor authentication scheme for WSN-based IIoT. Wirel. Netw. 2021;27:1389–1412. [Google Scholar]
- 18.Tanveer M., Abbas G., Abbas Z.H., Waqas M., Muhammad F., Kim S. S6AE: Securing 6LoWPAN using authenticated encryption scheme. Sensors. 2020;20:2707. doi: 10.3390/s20092707. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 19.Wu D., Zhou C. Fault-tolerant and scalable key management for smart grid. IEEE Trans. Smart Grid. 2011;2:375–381. doi: 10.1109/TSG.2011.2120634. [DOI] [Google Scholar]
- 20.Mahmood K., Chaudhry S.A., Naqvi H., Kumari S., Li X., Sangaiah A.K. An elliptic curve cryptography based lightweight authentication scheme for smart grid communication. Future Gener. Comput. Syst. 2018;81:557–565. doi: 10.1016/j.future.2017.05.002. [DOI] [Google Scholar]
- 21.Abbasinezhad-Mood D., Nikooghadam M. An anonymous ECC-based self-certified key distribution scheme for the smart grid. IEEE Trans. Ind. Electron. 2018;65:7996–8004. doi: 10.1109/TIE.2018.2807383. [DOI] [Google Scholar]
- 22.Banerjee S., Odelu V., Das A.K., Chattopadhyay S., Park Y. An Efficient, Anonymous and Robust Authentication Scheme for Smart Home Environments. Sensors. 2020;20:1215. doi: 10.3390/s20041215. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 23.Wazid M., Das A.K., Kumar N., Alazab M. Designing Authenticated Key Management Scheme in 6G-enabled Network in a Box Deployed for Industrial Applications. IEEE Trans. Ind. Inform. 2020;17:7174–7184. doi: 10.1109/TII.2020.3020303. [DOI] [Google Scholar]
- 24.Odelu V., Das A.K., Wazid M., Conti M. Provably secure authenticated key agreement scheme for smart grid. IEEE Trans. Smart Grid. 2016;9:1900–1910. doi: 10.1109/TSG.2016.2602282. [DOI] [Google Scholar]
- 25.Xie S., Zhang F., Lin H., Tian Y. A New Secure and Anonymous Metering Scheme for Smart Grid Communications. Energies. 2019;12:4751. doi: 10.3390/en12244751. [DOI] [Google Scholar]
- 26.Abbasinezhad-Mood D., Nikooghadam M. An ultra-lightweight and secure scheme for communications of smart meters and neighborhood gateways by utilization of an ARM Cortex-M microcontroller. IEEE Trans. Smart Grid. 2017;9:6194–6205. doi: 10.1109/TSG.2017.2705763. [DOI] [Google Scholar]
- 27.Gueron S., Jha A., Nandi M. COMET: COunter Mode Encryption with authentication Tag. Second Round Candidate of the NIST LWC Competition, 2019. [(accessed on 16 February 2023)]; Available online: https://csrc.nist.gov/CSRC/media/Projects/Lightweight-Cryptography/documents/round-1/spec-doc/comet-spec.pdf.
- 28.Nicanfar H., Jokar P., Beznosov K., Leung V.C. Efficient authentication and key management mechanisms for smart grid communications. IEEE Syst. J. 2013;8:629–640. doi: 10.1109/JSYST.2013.2260942. [DOI] [Google Scholar]
- 29.Bera B., Saha S., Das A.K., Vasilakos A.V. Designing Blockchain-Based Access Control Protocol in IoT-Enabled Smart-Grid System. IEEE Internet Things J. 2020;8:5744–5761. doi: 10.1109/JIOT.2020.3030308. [DOI] [Google Scholar]
- 30.Chaudhry S.A., Alhakami H., Baz A., Al-Turjman F. Securing demand response management: A certificate-based access control in smart grid edge computing infrastructure. IEEE Access. 2020;8:101235–101243. doi: 10.1109/ACCESS.2020.2996093. [DOI] [Google Scholar]
- 31.Tanveer M., Ahmad M., Nguyen T.N., Abd El-Latif A.A. Resource-Efficient Authenticated Data Sharing Mechanism for Smart Wearable Systems. IEEE Trans. Netw. Sci. Eng. 2022 doi: 10.1109/TNSE.2022.3203927. [DOI] [Google Scholar]
- 32.Srinivas J., Das A.K., Li X., Khan M.K., Jo M. Designing anonymous signature-based authenticated key exchange scheme for Internet of Things-enabled smart grid systems. IEEE Trans. Ind. Inform. 2020;17:4425–4436. doi: 10.1109/TII.2020.3011849. [DOI] [Google Scholar]
- 33.Irshad A., Chaudhry S.A., Alazab M., Kanwal A., Zia M.S., Zikria Y.B. A secure demand response management authentication scheme for smart grid. Sustain. Energy Technol. Assess. 2021;48:101571. doi: 10.1016/j.seta.2021.101571. [DOI] [Google Scholar]
- 34.Bera B., Das A.K., Sutrala A.K. Private blockchain-based access control mechanism for unauthorized UAV detection and mitigation in Internet of Drones environment. Comput. Commun. 2020;166:91–109. doi: 10.1016/j.comcom.2020.12.005. [DOI] [Google Scholar]
- 35.Chaudhry S.A., Yahya K., Karuppiah M., Kharel R., Bashir A.K., Zikria Y.B. GCACS-IoD: A certificate based generic access control scheme for Internet of Drones. Comput. Netw. 2021;191:107999. doi: 10.1016/j.comnet.2021.107999. [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Not applicable.