Abstract
The mediated semi-quantum key distribution (MSQKD) protocol is an important research issue that lets two classical participants share secret keys securely between each other with the help of a third party (TP). However, in the existing MSQKD protocols, there are two improvable issues, namely (1) the classical participants must be equipped with expensive detectors to avoid Trojan horse attacks and (2) the trustworthiness level of TP must be honest. To the best of our knowledge, none of the existing MSQKD protocols can resolve both these issues. Therefore, this study takes Bell states as the quantum resource to propose a MSQKD protocol, in which the classical participants do not need a Trojan horse detector and the TP is dishonest. Furthermore, the proposed protocol is shown to be secure against well-known attacks and the classical participants only need two quantum capabilities. Therefore, in comparison to the existing MSQKD protocols, the proposed protocol is better practical.
Subject terms: Quantum physics, Quantum information, Fibre optics and optical communications
Introduction
To establish a secure communication, any two participants must share a secret key. Therefore, the key distribution protocol is a fundamental part in cyber security research. In 1984, Bennet and Brassard1 used the properties of quantum mechanics to propose the first quantum key distribution (QKD) protocol—BB841. Further, some studies2–4 proved that the BB84 protocol is unconditionally secure. In the classical cryptography, only one-time pad can conform to the unconditionally secure ciphers. Following the BB84 protocol, various QKD protocols5–15 have been proposed. However, these QKD protocols assume that the protocol participants have complete quantum capabilities, implying that the participants can generate any type of quanta (single photons or entanglement states), store these qubits in quantum memory, and measure the qubits using any basis, among others. Most of these quantum capabilities are expensive and they are difficult to implement at present. To improve the practicality of the QKD protocol, Boyer et al.16,17 defined the semi-quantum concept and proposed the first semi-quantum key distribution (SQKD) protocol that consists of two types of participants: the quantum participant and the classical participant. The quantum participant has complete quantum capabilities, whereas the classical participant only owns limited quantum capabilities. After the semi-quantum environment was proposed, various kinds of semi-quantum protocols have been proposed for different security issues, some of which are SQKD for different situations18–26, semi-quantum communication27–33, semi-quantum secret sharing34–37, semi-quantum private comparison38,39, and semi-quantum information splitting40, among others41–43. According to the existing semi-quantum protocols16–43, this study summarizes the semi-quantum environments and the quantum capabilities of the classical participants in Table 1. It is worth noting that the unitary operations for a single qubit have been taken as candidates26,41–43 that the classical participants can utilize (i.e., the unitary operation based environment in Table1) except for the four operators proposed by Boyer et al.16,17. This is because the related technology of the unitary operations for a single qubit has developed rapidly and there are many quantum computers (e.g., the IBM Q system, Amazon Braket and so no) that provide mature quantum unitary operations.
Table 1.
Summary of semi-quantum environment.
| Environment | Capabilities of classical user |
|---|---|
| Measure-resend environment |
Generating Z-basis qubits Z-basis measurement Reflecting photons without disturbance |
| Randomization-based environment |
Z-basis measurement Reordering photons using different delay lines Reflecting photons without disturbance |
| Measurement-free environment |
Generating Z-basis qubits Reordering photons using different delay lines Reflecting photons without disturbance |
| Unitary operation based environment |
Z-basis measurement Generating Z-basis qubits Performing unitary operations |
Although SQKD protocols are more practical than the QKD protocol, existing SQKD protocols only focus on allowing two classical participants to share a secret key. However, letting two classical participants distribute secure keys is another interesting research topic. To handle this issue, Krawec21 proposed the first mediated semi-quantum key distribution (MSQKD) protocol. In this protocol, two classical participants can distribute a secret key with the help of a quantum third party (TP). Here, the trustworthiness of a TP can be categorized into the four levels summarized in Table 2, based on44. The trustworthiness of TP in Krawec’s protocol belongs to a dishonest TP.
Table 2.
Trustworthiness levels of TP.
| Trustworthiness level | Definition |
|---|---|
| Honest TP | The TP has to follow the procedure of the protocol honestly and the participants can completely trust it. Therefore, the participants can share their secret information with the TP. However, the assumption of a trustworthy TP may be impractical |
| Semi-honest TP | The TP has to execute the protocol loyally, but it may try to obtain the participants’ secret information passively using the records of all intermediate transmissions and computations by the participants |
| Almost dishonest TP | To extract the participants’ secret information, the TP may perform any possible attacks except collaborating with other participants. This assumption is only suitable for some applications such as a quantum private comparison protocol |
| Untrusted/dishonest TP | The TP may perform any possible attacks |
After Krawec’s MSQKD protocol, Liu et al.24 used the entanglement swapping of Bell states45 to improve the efficiency of the MSQKD protocol. Lin et al.25 used single photons to design the MSQKD protocol to make it even more practical. Recently, Francesco Massa et al.46 proposed an efficient MSQKD protocol, in which the classical participants only have the two capabilities including detecting and reflecting the qubits. In the above-mentioned MSQKD protocol, the TP and classical participants adopt the two-way quantum communication to distribute key information. In comparison to the one-way quantum communication, the two-way quantum communication results in two issues. (1) The classical participants need additional quantum devices (e.g., the photon number splitter or the optical wavelength filter) to screen out the Trojan photons. Equipping these devices may violate the original intention of the semi-quantum environment (i.e., reducing the quantum capabilities of the classical participants). (2) Because the transmission time of qubits is more than doubled, the qubits in the two-way quantum communication exhibit easier decoherence than the one-way communication. Taking IBM Q Melbourne as an example, the average decoherence time for 16 qubits, T1 (for maintaining energy) and T2 (for maintaining phase), are 65.30 and 22.70 µs, respectively. This indicates that if the transmission time is greater than T1 or T2, the original information in the qubits cannot be obtained. Therefore, the TP and the participants must spend more to maintain the qubits in a two-way quantum communication. Tsai et al.26 proposed a lightweight MSQKD protocol without the abovementioned issues; however, the trustworthiness of the TP is assumed to be honest, which may be impractical.
In this study, we refer the concept of5 to design a mediated semi-quantum key distribution protocol with a dishonest TP. In the proposed protocol, the TP takes Bell states as quantum resources to assist the two classical participants in distributing the secret key but the TP cannot obtain any information about this secret key even if it performs any possible attack. In contrast, the classical participants only need two quantum properties including (1) Z-basis measurement and (2) performing Hadamard operator. The two capabilities have been practiced in quantum computers47 or optical experiment implementation48–53; that is to say, Hadamard operation and Z-basis measurement devices have feasibilities in real implementation. Therefore, the proposed protocol maintains the lightweight property in terms of the quantum capabilities of the classical participant. Moreover, the one-way quantum communication strategy is adopted to design the protocol, and thus the proposed protocol is immune to Trojan horse attacks, implying that the classical participants do not equip any Trojan Horse detector.
The rest of this paper is organized as follows. “Proposed LMSQKD protocol” section introduces the quantum properties used in the proposed protocol and the proposed lightweight mediated semi-quantum key distribution (LMSQKD) protocol. “Security analysis” section presents the security analyses of the proposed LMSQKD protocol and then provides comparisons between the state-of-the-art MSQKD protocols in “Performance comparison” section. Finally, the conclusions are presented in “Conclusions” section.
Proposed LMSQKD protocol
In this section, the assumptions, quantum capability limitations of the classical participants, and the quantum properties used in the proposed protocol are described, and a lightweight mediated semi-quantum key distribution protocol is proposed.
In this study, we assume that two classical participants, Alice and Bob, want to share the secret key with the help of a TP, where the TP is dishonest (i.e., TP may perform any possible attack to compromise the distributed key). There are the one-way quantum channels between the TP and each classical participant (i.e., Alice and Bob). The classical channel between Alice and Bob is assumed to be authenticated. This study assumes that a classical participant has two quantum capabilities including (1) measuring the qubit using Z-basis and (2) performing Hadamard operator H, where H is defined as follows:
| 1 |
However, the TP needs to generate the Bell states , which are defined as follows:
| 2 |
The related assumptions and limitations in this study are summarized in Table 3.
Table 3.
Summary of assumptions and limitations.
| Assumption and limitation | Description |
|---|---|
| Capacities of classical users |
(1). Performing H operation (2). Measuring qubit using Z-basis |
| Capabilities of TP | Generating Bell states |
| Trueness of TP | Dishonest |
| Quantum channel |
(1). TP and Alice have an one-way quantum channel, TP → Alice (2). TP and Bob have an one-way quantum channel, TP → Bob |
| Classical channel |
(1) Alice ↹ Bob is an authenticated classical channel (2). TP ↹ Alice and TP ↹ Bob are the authenticated classical channels |
To enable Alice and Bob to share the secret key with the help of the TP, this study uses a quantum property: the relationship between Bell states and Hadamard operator. Here, Alice and Bob randomly decide to implement the identity operator I (i.e., do nothing) or Hadamard operator H on one of the two qubits (i.e., Alice implements the unitary operator on the first qubit of the Bell states and Bob implements the unitary operator on the second qubit). Then, they measure the qubits using Z-basis. The relationships between their implemented operators and measurement results are summarized in the following table, where and denote Alice’s and Bob’s measurement results, respectively.
According to the above-mentioned relationship, we can determine the two cases as follows.
Case 1 Alice and Bob can use their measurement results as the raw key bits or checking bits when they perform the same operations.
Case 2 When they use different operations, they will discard the measurement results owing to the uncertain measurement results (i.e., Alice cannot use her measurement results to infer Bob’s).
It should be noted that the measurement results are pure-random values in accordance with the property of measurements in Bell states, implying that Alice and Bob will share a one-time pad key (pure-random key) using this quantum property. That is, the participants do not spend the extra cost for generating the pure-random key.
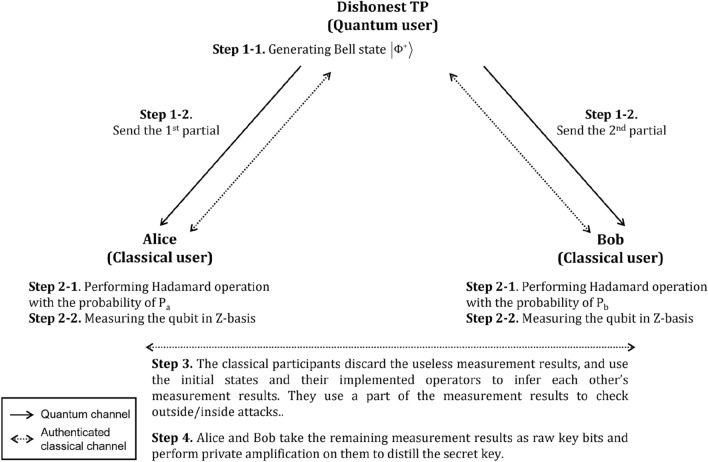
This study assumes that Alice and Bob want to distribute an n-bit secret key. The steps of the proposed LMSQKD protocol are described as follows (also shown in Fig. 1).
Figure 1.
Processes of the proposed LMSQKD protocol.
Step 1 TP generates the Bell state and then, sends the first and second qubits of the Bell state to Alice and Bob, respectively.
Step 2 After receiving the qubit, Alice (Bob) performs H or I operation on the qubit with the probabilities of () or (), respectively. And then, they measure the qubits using Z-basis to obtain the measurement results and , where i indicates the i-th time measurement result.
TP, Alice, and Bob repeat Step 1 and Step 2 4n times.
Step 3 According to Table 4, Alice and Bob discard the useless measurement results and choose the enough remaining measurement results as the checking bits (e.g., using 50% measurement results) to perform Public Discussion1 to detect outsider or insider attackers using the authenticated classical channel. If the error rate is more than the pre-defined threshold (the threshold will be evaluated in the “Key rate bound evaluation” section), they will terminate the protocol and restart from the beginning; otherwise, they will continue the protocol.
Table 4.
Relationship between Bell states and Hadamard operations.
| Initial state | Alice’s operation | Bob’s operation | Qubit state | Relationship of measurement result |
|---|---|---|---|---|
| I | I | |||
| I | H | Uncertain | ||
| H | I | Uncertain | ||
| H | H |
Step 4 Alice and Bob use the remaining measurement results in Step 3 and the relationship shown in Table 4 to obtain the raw key bits, and then perform privacy amplification54,55 on the raw key bits to obtain the distributed secret key. Generally, Alice and Bob will obtain -bit secret key if and in Step 2, and they use the half corresponding measurement results as the checking bits in Step 3.
Security analysis
In this section, we analyze the security of the proposed LMSQKD protocol. In terms of security analysis, the collective attack is a very important class of attacks, and the assumption of attacker’s power in the collective attack is more powerful than the individual attack (e.g., the intercept-and-resend attack)56,57. Thus, in this section, a complete collective attack analysis is given first, followed by the analysis of TP’s fake photons attack and, the Trojan horse attack.
Collective attack
For the collective attack, there are two types of analyses. In the first type of analysis, we need to prove that the attacker will disturb the original quantum system if the attacker wants to obtain useful information (i.e., robustness defined by16,17). In the second type of analysis, the amount of information that the attacker can obtain is analyzed. In this study, we want to use the first type of analysis to prove that the collective attack will occur the rise in quantum bit error rate (QBER) and the participants abort the protocol when QBER is more than a preset threshold t, and then the information-theoretic security method is adopted to evaluate the proposed protocol’s the key rate bound which will be used to formulate the pre-defined threshold t.
Robustness analysis
For robustness analysis, we prove that an attacker cannot perform a collective attack to obtain any information regarding the raw key without being detected by the participants in the proposed MSQKD protocol. It should be noted that a dishonest TP has more advantages than an outside attacker. Therefore, we consider the TP as an attacker to discuss the security of the proposed protocol.
Before analyzing this attack, we first define the collective attack as follows:
TP can insert its ancillary qubits in each quantum system transmitted on the quantum channel and then measure the ancillary qubits to obtain Alice’s or Bob’s secret key bit.
Each quantum system sent between the users is attacked by the TP independently using the same strategy.
The TP can keep the ancillary qubits until any later time, implying that it can measure the ancillary qubits after obtaining some information originating from this attack.
Therefore, a dishonest TP will perform a unitary operation to entangle the initial quantum system with its prepared ancillary qubits and measure them later to obtain useful information from the proposed protocol by performing the collective attack. must comply with the theorems of quantum mechanics, and thus it is defined as follows.
| 3 |
where denotes the initial state of TP’s ancillary qubit;, , , and are four states that can be distinguished by the TP (i.e., the four states are orthogonal to each other); and . Because Alice and Bob discard the measurement results when they implement different operators, we only consider the following two situations: (1) Alice and Bob both implement the I operator and (2) they both implement the H operator.
For the first situation, the quantum system can be given as follows.
| 4 |
Because , , , and are the four states that can be distinguished by TP, it can infer Alice’s and Bob’s measurement results using the ancillary qubits. By linearity, the quantum system of the second situation can be shown as follows.
| 5 |
Here TP can also distinguish the four states , , , and because these states are still orthogonal to each other, implying that TP can also obtain Alice’s and Bob’s measurement results in the second situation.
In the proposed protocol, Alice and Bob take the public discussion to check their measurement result in Step 3. Thus, TP must adjust to avoid the participants’ check. If TP adjusts for the first situation, it will set and as 0 to avoid the classical participants’ public discussion. However, according to this setting, the quantum system of the second situation will be given as follows.
| 6 |
To pass through the classical participants’ public discussion, TP also must set , which signifies , implying that TP cannot obtain any information about Alice’s and Bob’s measurement results in both situations. In contrast, if TP adjusts for the second situation, it will set , which signifies . Then, TP sets and as 0 for the first situation. After the abovementioned setting, the quantum systems can be given as follows:
| 7 |
| 8 |
According to the analyses above, although the TP can determine a collective attack path , and Alice and Bob cannot detect the attack, the TP cannot obtain any information regarding the raw key because . In contrast, if the TP wishes to obtain useful information regarding the classical participants’ raw key, the TP cannot use to execute a collective attack, so the TP’s attack will induce a detectable disturbance that increases the QBER. This gives Alice and Bob a nonzero probability of detecting the TP’s attack.
Key rate bound evaluation
To analyze the bound of secret-key rate in the semi-quantum key distribution protocol, Krawec58,59 have proposed the applicable key-rate proof manner for two-way quantum communication. However, because the qubit transmission is one-way in the proposed protocol, we only use the security analysis method proposed in60 to evaluate the lower bound of the secret-key rates, in which the lower bound of the secret-key rate is proposed as followed:
| 9 |
In this formula, , denotes the von Neumann entropy of U (i.e., raw key bits of Alice) conditioned on an attacker’s probe system (here, we assume TP as the attacker). is Shannon entropy of U conditioned on Bob’s measurement results B. In the proposed protocol, Alice and Bob have the two measurement modes, that is, (1) Model 1: measuring the qubit by Z-basis immediately, (2) Mode2: performing Hadamard operator on the qubit and then measuring it by Z-basis (note that this measurement is equivalent to X-basis measurement). Therefore, the key rate bound evaluation method of the propose protocol is similar to BB84’s evaluation method proposed in57. After TP’s collective attack, we set the quantum sates as
| 10 |
where denote the four Bell states in Alice and Bob’s joint system and are some mutually orthogonal states in TP’s probe system. Assuming the quantum bit error rate (QBER) is Q, we can get (with respect to Mode 1) and (with respect to Mode 2). Normalizing , and , we get , and . Because the evaluation methods and results are the same in the two measurement modes, we only describe the analysis processes of the first measurement mode (measuring the qubit by Z-basis) in this section. Let denotes the state of TP’s probe system, where a and b denote Alice’s and Bob’s measurement results, respectively. could be the four kind of states (with respect to Mode 1) shown as followed:
| 11 |
According to Eq. (11), we can get the density operator of the TP probe system as followed:
| 12 |
where is a plus if and a minus if . Therefore, according to Eqs. (9) and (12), we can get
| 13 |
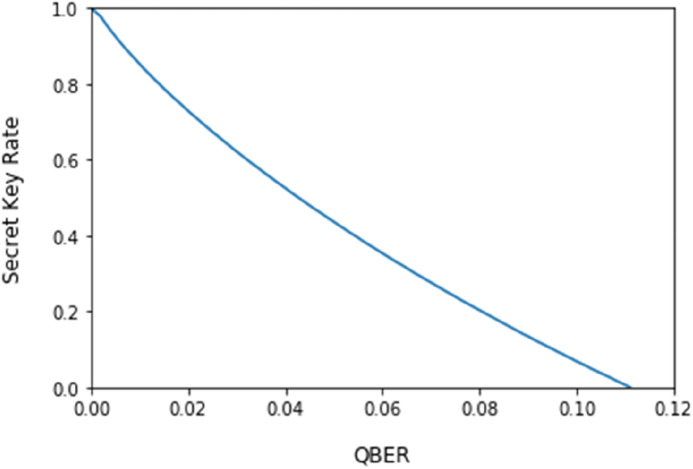
with , , and , where is the binary entropy function. We use the Eq. (13) to evaluate the secret key rate of the proposed protocol and obtain that the secret key rate is a positive rate if . Figure 2 shows the secret key rates under the different QBER values.
Figure 2.
The secret key rate under the different QBER values.
TP’s fake photon attack
In the proposed protocol, Alice and Bob use the measurement results of Z-basis to be the secret keys. Therefore, in addition to inserting the ancillary qubits in each quantum system transmitted on the quantum channel, TP can also use the other quantum system instead of the Bell state to manipulate the classical participants’ measurement results for stealing their secret keys.
The TP can take a single photon pair using Z-basis instead of Bell states, where the states of a single photon pair are generated depending on the original Bell state . For example, TP will generate the photon pair with the same state (e.g., or ), and then TP sends the first and second qubits of the single photon pair to Alice and Bob in Step 1 of the proposed protocol, respectively. Because the photon pairs are generated by TP, it can determine the classical participants’ measurement results to manipulate the raw key bits. Unfortunately, TP’s attack can be detected by Alice and Bob in Step 3 because TP has no information about the operators implemented by Alice and Bob in Step 2. This implies that when both Alice and Bob implement the H operator on the single photon pair, their measurement results may violate the relationship shown in Table 4 with the probability of . Taking an example to explain this situation, TP generates instead of Bell state and then, the classical participants both implement the H operator. Here, their measurement results may be one of the four possibilities , , , and . If the measurement result is or , Alice and Bob can detect TP’s attack by Public Discussion. Although TP generates single photon pairs using X-basis (, ) to avoid the abovementioned detection, its attack can still be determined by Alice and Bob when they both implement the I operator in Step 2. The detection probability for the fake photon attack is , where m denotes Alice and Bob using m measurement results to do Public Discussion. It implies that if m is large enough, the detection probability will approach 1, that is, the proposed protocol is robust against fake photon attack.
Trojan horse attack
Regarding implementation-dependent attacks, Trojan horse attacks61,62 are common. This paper discusses two types of Trojan horse attacks. The first is a delayed photon Trojan horse attack. In this attack, an attacker intercepts a qubit transmitted to a participant and then inserts a probing photon in the qubit with a delay time that is shorter than the time window. In this method, a participant cannot detect the fake photon because it does not register on their detector. After a participant performs the corresponding operation and returns the qubit, the attacker intercepts the qubit again and separates the probing photon. In this case, the attacker can obtain full information regarding a participant’s operation by measuring the probing photon. The second attack is an invisible photon Trojan horse attack. The main strategy of this attack is to insert an invisible photon in each qubit sent to the participant. Because the participant’s detector cannot detect this photon and performs a unitary operation on the qubit (the invisible photon also performs the same operation simultaneously), the attacker can steal information regarding the participant’s operations in a manner similar to the delay photon Trojan horse attack.
In the attack methods mentioned above, the attacker can only extract information regarding participant operations when they retrieve the Trojan horse photons. A two-way communication protocol gives the attacker a chance to retrieve Trojan horse photons. Therefore, a protocol is only vulnerable to Trojan horse attacks if it adopts two-way communication. In contrast, in a one-way communication protocol, the attacker has no chance to retrieve the Trojan horse photons because no qubit is returned by the participant. In other words, the protocol will be robust to Trojan horse attacks if it is a one-way communication protocol.
In the proposed MSQKD protocol, the qubit quantum transmission strategy only operates in one direction, meaning qubits are only sent from the TP to the classical participants. Although the attacker can insert probing photons into the original qubits, they cannot extract any information regarding the participants’ secret keys because the probing photons cannot be retrieved. Therefore, the proposed protocol is immune to Trojan horse attacks. Therefore, the classical participants do not need to be equipped with expensive devices (such as photon number splitters and optical wavelength filter devices) to mitigate Trojan horse attacks.
Performance comparison
This section presents a comparison between the existing state-of-the-art MSQKD including Krawec’s21, Liu et al.’s24, Lin et al.’s25, and Tsai et al.’s26 protocols. The comparison includes the semi-quantum environment, classical participant’s quantum capabilities, quantum resources, trustworthiness level of TP, quantum efficiency, time of maintaining qubit to avoid decoherence, and whether a classical participant needs to be equipped with Trojan Horse detectors.
In terms of the semi-quantum environment and classical participant’s quantum capabilities, both Krawec’s and Lin et al.’s protocols use the measure-resend environment to ensure that the classical participants do not store the qubits. Although the classical participants do not need the quantum measurement devices, they must store the qubits for a period time to reorder them. The protocols proposed by Tsai et al. and this study only let the classical users be equipped with two quantum devices to ensure that this environment is more lightweight than the unitary operation-based environment. This type of environment is called lightweight unitary operation-based environment. For quantum resources, besides the protocols proposed by Lin et al. and Tsai et al., the TP needs to use the Bell states as quantum resources to assist Alice and Bob in distributing the secret keys. It should be noted that the TPs in these protocols are dishonest, except for Tsai et al.’s protocol.
Furthermore, we compared the proposed MSQKD to other protocols in terms of qubit efficiency, which is defined by the following equation63–65.
| 14 |
where denotes the number of bits of the shared session key and denotes the number of total qubits used in the protocol. In our protocol, TP generates n Bell states to let Alice and Bob share -bit secret key if they set and in Step 2, and use the half corresponding measurement results as the checking bits in Step 4. Therefore, the qubit efficiency of our protocol is , which is better than the others besides Liu et al.’s protocol.
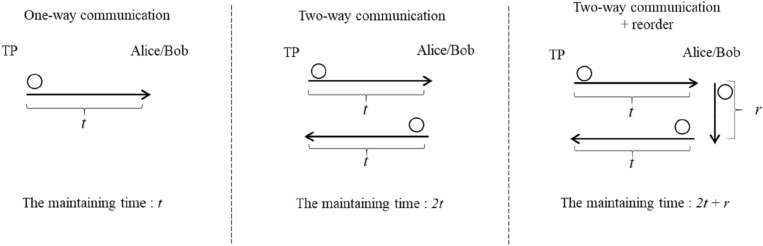
This study assumes the time taken by the TP to transmit a qubit to each classical participant to be t. It should be noted that the qubits reflected by each participant to the TP are the same. Because the protocols proposed by Krawec, Lin et al., and Liu et al. use the two-way quantum communication, TP and the participants spent at least 2t time to maintain the qubits to avoid decoherence. However, Liu et al.’s protocol requires the qubits to be reordered. Therefore, the time taken to maintain the qubits increases to r, to reorder the qubits, and thus the maintain time should increase r which is the time of reordering the qubit sequence. In contrast, the protocols proposed by Tsai et al. and this study only spend time t to maintain the qubits because they adopted the one-way quantum communication. Figure 3 shows the time taken to maintain the qubits for two-way and one-way quantum communications. Excluding the protocols proposed by Tsai et al. and this study, the classical participants need to be equipped with Trojan horse attack detectors.
Figure 3.
Time of maintaining qubits.
All comparisons are summarized in Table 5. According to the above-mentioned comparison issues, our protocol is better than other MSQKD protocols in terms of practical implementation.
Table 5.
Comparison to the existing MSQKD protocols.
| Krawec’s21 | Liu et al.’s24 | Lin et al.’s25 | Tsai et al.’s26 | Our protocol | |
|---|---|---|---|---|---|
| Semi-quantum environment | Measure-resend | Measurement-free | Measure-resend | Lightweight unitary operation | Lightweight unitary operation |
| Quantum capability of classical participant |
(1) Generation (2) Measurement (3) Reflection |
(1) Generation (2) Reflection (3) Reorder |
(1) Generation (2) Measurement (3) Reflection |
(1) Measurement (2) Operation |
(1) Measurement (2) Operation |
| Quantum resources |
(1) Single photon (2) Bell state |
(1) Single photon (2) Bell state |
Single photon | Single photon | Bell state |
| Trustworthiness level of TP | Dishonest | Dishonest | Dishonest | Honest | Dishonest |
| Qubit efficiency | 1/24 | 1/8 | 1/24 | 1/32 | 1/8 |
| Time for maintaining qubits | 2t | 2t + r | 2t | t | t |
| Equipping with detectors or not | Yes | Yes | Yes | No | No |
Conclusions
To make the mediated key distribution protocol more practical, this study referred the concept of5 to propose a lightweight mediated semi-quantum key distribution protocol to enable the sharing of secret keys between two classical participants with the help of a dishonest TP, in which the classical participants only need to be equipped with two quantum devices. The proposed protocol adopts one-way quantum communication to reduce the time of preventing the qubits from decoherence and avoid the use of Trojan horse detectors. The security analysis and performance comparison are presented to demonstrate that the proposed protocol is secure and efficient. The proposed protocol only let two classical participants to share secret keys, and thus how to let multiple participants can share the group keys is our future research.
Acknowledgements
We would like to thank the anonymous reviewers and the editor for their very valuable comments, which greatly enhanced the clarity of this paper. This research was partially supported by the Ministry of Science and Technology, Taiwan, R.O.C. (Grant Nos. MOST 110-2221-E-039-004, MOST 110-2221-E-143-003, MOST 110-2221-E-259-001, and MOST 110-2221-E-143-004), and China Medical University, Taiwan (Grant No. CMU110-MF-121).
Author contributions
Conceptualization, C.-W. Tsai and C.-W. Yang; methodology, C.-W. Tsai and C.-W. Yang; investigation, C.-W. Tsai and C.-W. Yang; formal analysis, C.-W. Tsai; writing—original draft, C.-W. Tsai and C.-W. Yang; writing—review & editing, C.-W. Yang; project Administration, C.-W. Yang. All authors have read and agreed to the published version of the manuscript.
Competing interests
The authors declare no competing interests.
Footnotes
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Bennett, C. H., Brassard, G., Quantum cryptography: Public key distribution and coin tossing. In IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, 175–179 (1984).
- 2.Shor PW, Preskill J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 2000;85(2):441–444. doi: 10.1103/PhysRevLett.85.441. [DOI] [PubMed] [Google Scholar]
- 3.Gottesman D, Hoi-Kwong L. Proof of security of quantum key distribution with two-way classical communications. IEEE Trans. Inf. Theory. 2003;49(2):457–475. [Google Scholar]
- 4.Tsurumaru T, Tamaki K. Security proof for quantum-key-distribution systems with threshold detectors. Phys. Rev. A. 2008;78(3):032302. [Google Scholar]
- 5.Bennett CH, Brassard G, Mermin ND. Quantum cryptography without Bell’s theorem. Phys. Rev. Lett. 1992;68(5):557–559. doi: 10.1103/PhysRevLett.68.557. [DOI] [PubMed] [Google Scholar]
- 6.Cerf NJ, Bourennane M, Karlsson A, Gisin N. Security of quantum key distribution using d-level systems. Phys. Rev. Lett. 2002;88(12):127902. doi: 10.1103/PhysRevLett.88.127902. [DOI] [PubMed] [Google Scholar]
- 7.Long G, Liu X. Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. A. 2002;65(3):032302. [Google Scholar]
- 8.Grosshans F, Van Assche G, Wenger J, Brouri R, Cerf NJ, Grangier P. Quantum key distribution using gaussian-modulated coherent states. Nature. 2003;421:238. doi: 10.1038/nature01289. [DOI] [PubMed] [Google Scholar]
- 9.Hwang W-Y. Quantum key distribution with high loss: Toward global secure communication. Phys. Rev. Lett. 2003;91(5):057901. doi: 10.1103/PhysRevLett.91.057901. [DOI] [PubMed] [Google Scholar]
- 10.Lo HK, Ma XF, Chen K. Decoy state quantum key distribution. Phys. Rev. Lett. 2005;94(23):4. doi: 10.1103/PhysRevLett.94.230504. [DOI] [PubMed] [Google Scholar]
- 11.Hwang T, Lee KC, Li CM. Provably secure three-party authenticated quantum key distribution protocols. IEEE T Depend Sec. 2007;4(1):71–80. [Google Scholar]
- 12.Li XH, Deng FG, Zhou HY. Efficient quantum key distribution over a collective noise channel. Phys. Rev. A. 2008;78(2):022321. [Google Scholar]
- 13.Hwang T, Hwang CC, Tsai CW. Quantum key distribution protocol using dense coding of three-qubit W state. Eur. Phys. J. D Atomic Mol. Opt. Plasma Phys. 2011;61(3):785–790. [Google Scholar]
- 14.Lo H-K, Curty M, Qi B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012;108(13):130503. doi: 10.1103/PhysRevLett.108.130503. [DOI] [PubMed] [Google Scholar]
- 15.Yang C-W. New probabilistic quantum key distribution protocol. Int. J. Theor. Phys. 2018;57(12):3651–3657. [Google Scholar]
- 16.Boyer M, Kenigsberg D, Mor T. Quantum key distribution with classical bob. Phys. Rev. Lett. 2007;99(14):140501. doi: 10.1103/PhysRevLett.99.140501. [DOI] [PubMed] [Google Scholar]
- 17.Boyer M, Gelles R, Kenigsberg D, Mor T. Semiquantum key distribution. Phys. Rev. A. 2009;79(3):032341. [Google Scholar]
- 18.Zou X, Qiu D, Li L, Wu L, Li L. Semiquantum-key distribution using less than four quantum states. Phys. Rev. A. 2009;79(5):052312. [Google Scholar]
- 19.Wang J, Zhang S, Zhang Q, Tang CJ. Semiquantum key distribution using Entangled States. Chin. Phys. Lett. 2011;28(10):100301. [Google Scholar]
- 20.Yu K-F, Yang C-W, Liao C-H, Hwang T. Authenticated semi-quantum key distribution protocol using Bell states. Quantum Inf. Process. 2014;13(6):1457–1465. [Google Scholar]
- 21.Krawec WO. Mediated semiquantum key distribution. Phys. Rev. A. 2015;91(3):032323. [Google Scholar]
- 22.Zou X, Qiu D, Zhang S, Mateus P. Semiquantum key distribution without invoking the classical party’s measurement capability. Quantum Inf. Process. 2015;14(8):2981–2996. [Google Scholar]
- 23.Li Q, Chan WH, Zhang S. Semiquantum key distribution with secure delegated quantum computation. Sci. Rep. 2016;6:19898. doi: 10.1038/srep19898. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 24.Liu Z-R, Hwang T. Mediated semi-quantum key distribution without invoking quantum measurement. Ann. Phys. 2018;530(4):1700206. [Google Scholar]
- 25.Lin P-H, Tsai C-W, Hwang T. Mediated semi-quantum key distribution using single photons. Ann. Phys. 2019;531(8):1800347. [Google Scholar]
- 26.Tsai C-W, Yang C-W, Lee N-Y. Lightweight mediated semi-quantum key distribution protocol. Mod. Phys. Lett. A. 2019;34(34):1950281. [Google Scholar]
- 27.Zou X, Qiu D. Three-step semiquantum secure direct communication protocol. Sci. China Phys. Mech. 2014;57(9):1696–1702. [Google Scholar]
- 28.Luo Y-P, Hwang T. Authenticated semi-quantum direct communication protocols using Bell states. Quantum Inf. Process. 2016;15(2):947–958. [Google Scholar]
- 29.Zhang M-H, Li H-F, Xia Z-Q, Feng X-Y, Peng J-Y. Semiquantum secure direct communication using EPR pairs. Quantum Inf. Process. 2017;16(5):117. [Google Scholar]
- 30.Xie C, Li L, Situ H, He J. Semi-quantum secure direct communication scheme based on Bell states. Int. J. Theor. Phys. 2018;57(6):1881–1887. [Google Scholar]
- 31.Yan L, Sun Y, Chang Y, Zhang S, Wan G, Sheng Z. Semi-quantum protocol for deterministic secure quantum communication using Bell states. Quantum Inf. Process. 2018;17(11):315. [Google Scholar]
- 32.Sun Y, Yan L, Chang Y, Zhang S, Shao T, Zhang Y. Two semi-quantum secure direct communication protocols based on Bell states. Mod. Phys. Lett. A. 2019;34(01):1950004. [Google Scholar]
- 33.Yang C-W. Efficient and secure semi-quantum secure direct communication protocol against double CNOT attack. Quantum Inf. Process. 2020;19(2):50. [Google Scholar]
- 34.Li Q, Chan WH, Long DY. Semiquantum secret sharing using entangled states. Phys. Rev. A. 2010;82(2):022303. [Google Scholar]
- 35.Yang C-W, Hwang T. Efficient key construction on semi-quantum secret sharing protocols. Int. J. Quant. Infor. 2013;11(05):1350052. [Google Scholar]
- 36.Yu K-F, Gu J, Hwang T, Gope P. Multi-party semi-quantum key distribution-convertible multi-party semi-quantum secret sharing. Quantum Inf. Process. 2017;16(8):194. [Google Scholar]
- 37.Tsai C-W, Yang C-W, Lee N-Y. Semi-quantum secret sharing protocol using W-state. Mod. Phys. Lett. A. 2019;34(27):1950213. [Google Scholar]
- 38.Thapliyal K, Sharma RD, Pathak A. Orthogonal-state-based and semi-quantum protocols for quantum private comparison in noisy environment. Int. J. Quant. Infor. 2018;16(05):1850047. [Google Scholar]
- 39.Lin P-H, Hwang T, Tsai C-W. Efficient semi-quantum private comparison using single photons. Quantum Inf. Process. 2019;18(7):207. [Google Scholar]
- 40.Nie YY, Li YH, Wang ZS. Semi-quantum information splitting using GHZ-type states. Quantum Inf. Process. 2013;12(1):437–448. [Google Scholar]
- 41.Liu W-J, Chen Z-Y, Ji S, Wang H-B, Zhang J. Multi-party semi-quantum key agreement with delegating quantum computation. Int. J. Theor. Phys. 2017;56(10):3164–3174. [Google Scholar]
- 42.Li H-H, Gong L-H, Zhou N-R. New semi-quantum key agreement protocol based on high-dimensional single-particle states. Chin. Phys. B. 2020;29(11):110304. [Google Scholar]
- 43.Tsai C-W, Yang C-W. Lightweight authenticated semi-quantum key distribution protocol without trojan horse attack. Laser Phys. Lett. 2020;17(7):075202. [Google Scholar]
- 44.Zhang W-W, Zhang K-J. Cryptanalysis and improvement of the quantum private comparison protocol with semi-honest third party. Quantum Inf. Process. 2013;12(5):1981–1990. [Google Scholar]
- 45.Zukowski M, Zeilinger A, Horne MA, Ekert AK. Event-ready-detectors Bell experiment via entanglement swapping. Phys. Rev. Lett. 1993;71(26):4287–4290. doi: 10.1103/PhysRevLett.71.4287. [DOI] [PubMed] [Google Scholar]
- 46.Massa, F., Yadav, P., Moqanaki, A., Krawec, W. O., Mateus, P., Paunković, N., Souto, A., Walther, P. Experimental quantum cryptography with classical users. https://arxiv.org/abs/1908.01780 (2019).
- 47.IBM q experience. (accessed: 22 Apr 2020); https://quantumexperience.ng.bluemix.net/qx/devices.
- 48.Dik B, Jian-Wei P, Klaus M, Manfred E, Harald W, Anton Z. Experimental quantum teleportation. Nature. 1997;390:575–579. [Google Scholar]
- 49.Ji-Gang R, et al. Ground-to-satellite quantum teleportation. Nature. 2017;549:70–73. doi: 10.1038/nature23675. [DOI] [PubMed] [Google Scholar]
- 50.Young, R. C., Birch, P. M., & Chatwin, C. R. Coherent optical implementations of the fast Fourier transform and their comparison to the optical implementation of the quantum Fourier transform. In Proceedings of SPIE 8748, Optical Pattern Recognition XXIV, 874806 (2013).
- 51.Anders T, et al. Experimental demonstration of a Hadamard gate for coherent state qubits. Phys. Rev. A. 2011;84:050301. [Google Scholar]
- 52.Cerf NJ, Adami C, Kwiat PG. Optical simulation of quantum logic. Phys. Rev. A. 1998;57(3):R1477. [Google Scholar]
- 53.O'Brien JL. Optical quantum computing. Science. 2007;318(5856):1567–1570. doi: 10.1126/science.1142892. [DOI] [PubMed] [Google Scholar]
- 54.Bennett CH, Brassard G, Robert JM. Privacy amplification by public discussion. SIAM J. Comput. 1988;17(2):210–229. [Google Scholar]
- 55.Bennett CH, Brassard G, Crepeau C, Maurer UM. Generalized privacy amplification. IEEE Trans. Inf. Theory. 1995;41(6):1915–1923. [Google Scholar]
- 56.Biham E, et al. Security of quantum key distribution against all collective attacks. Algorithmica. 2002;34(4):372–388. [Google Scholar]
- 57.Scarani V, Bechmann-Pasquinucci H, Cerf NJ, Dušek M, Lütkenhaus N, Peev M. The security of practical quantum key distribution. Rev. Mod. Phys. 2009;81(3):1301–1350. [Google Scholar]
- 58.Krawec, W. O. Security proof of a semi-quantum key distribution protocol. In 2015 IEEE International Symposium on Information Theory (ISIT), 686–690 (2015).
- 59.Krawec WO. Quantum key distribution with mismatched measurements over arbitrary channels. Quantum Inf. Comput. 2017;17(3–4):209–241. [Google Scholar]
- 60.Renner R, Gisin N, Kraus B. Information-theoretic security proof for quantum-key-distribution protocols. Phys. Rev. A. 2005;72(1):012332. doi: 10.1103/PhysRevLett.95.080501. [DOI] [PubMed] [Google Scholar]
- 61.Deng FG, Li XH, Zhou HY, Zhang ZJ. Improving the security of multiparty quantum secret sharing against Trojan horse attack. Phys. Rev. A. 2005;72(4):044302. [Google Scholar]
- 62.Cai QY. Eavesdropping on the two-way quantum communication protocols with invisible photons. Phys. Lett. A. 2006;351(1–2):23–25. [Google Scholar]
- 63.Yang C-W, Hwang T. Improved QSDC protocol over a collective-dephasing noise channel. Int. J. Theor. Phys. 2012;51(12):3941–3950. [Google Scholar]
- 64.Yang C-W, Hwang T. Quantum dialogue protocols immune to collective noise. Quantum Inf. Process. 2013;12(6):2131–2142. [Google Scholar]
- 65.Yang C-W, Hwang T, Luo Y-P. Enhancement on quantum blind signature based on two-state vector formalism. Quantum Inf. Process. 2013;12(1):109–117. [Google Scholar]