Abstract
Quantum key distribution (QKD) is a secure communication scheme for sharing symmetric cryptographic keys based on the laws of quantum physics, and is considered a key player in the realm of cyber-security. A critical challenge for QKD systems comes from the fact that the ever-increasing rates at which digital data are transmitted require more and more performing sources of quantum keys, primarily in terms of secret key generation rate. High-dimensional QKD based on path encoding has been proposed as a candidate approach to address this challenge. However, while proof-of-principle demonstrations based on lab experiments have been reported in the literature, demonstrations in realistic environments are still missing. Here we report the generation of secret keys in a 4-dimensional hybrid time-path-encoded QKD system over a 52-km deployed multicore fiber link forming by looping back two cores of a 26-km 4-core optical fiber. Our results indicate that robust high-dimensional QKD can be implemented in a realistic environment by combining standard telecom equipment with emerging multicore fiber technology.
Subject terms: Quantum physics, Quantum information
High-dimensional QKD would in principle allow for several advantages over its bidimensional counterpart, but in-the-field demonstrations are missing. Here, the authors realise 4- dimensional hybrid time-path-encoded QKD using a 52-km deployed multicore fiber link.
Introduction
Global data transmission is increasing exponentially every year1 and security of communication against new forms of attacks has become a relevant concern for scientific communities and cyber-security experts, as well as for the general public. While computationally secure encryption protocols2,3 are the basic building blocks of today’s communication network, quantum key distribution (QKD) is the only known method that can guarantee information-theoretic secure encryption between two or more parties. In particular, QKD allows to share a symmetric cryptographic key, useful to encrypt data communication without binding the security to any assumption on the attacker’s capabilities. The two most important figures of merit of QKD are the secret-key generation rate, and the overall link distance between users, which are both limited by the loss and noise levels affecting the transmitted quantum signals. Indeed, in the absence of high-performance quantum memory4, which is still challenging today5, the achievable rate and distance for a given error rate affecting the quantum signal reception are limited, with bounds discussed in6.
An alternative approach to addressing the noise limit and the low generation rate relies on the use of high-dimensional (Hi-D) quantum states—qudits—for quantum communication purposes. As shown in7–9, protocols based on qudits are considerably more resilient to noise than protocols based on qubits. These protocols allow the generation of a secure key even at high noise levels and can provide high communication capacity. More in detail, the highest tolerance in two-dimensional systems based on the BB84 protocol using one-way reconciliation, in the case of coherent attacks, corresponds to a quantum bit error rate (QBER) of ~ 11%10, whereas this threshold increases to 18% and 24% for four-dimensional and eight-dimensional systems, respectively7,8.
Proof-of-concept experiments exploiting Hi-D encoding have already been demonstrated using different degrees of freedom such as frequency11, orbital angular momentum (OAM)12–14, path-encoding15,16, OAM-Path hybrid17, OAM-Polarization hybrid18, time-energy and time-bin encoding19–21 and Frequency-time hybrid22. Multicore fibers, whose potential in transmitting classical data at petabit-per-second rates has been recently demonstrated23, are also being considered for quantum applications. The reason is that they allow implementing practical Hi-D QKD systems based on path-encoding protocols, which do not suffer from state fragility seen in other protocols like those based on OAM encoding, and they do not reduce the effective qudit rate—a drawback of protocols based on time-bin encoding. However, all demonstrations of Hi-D path-encoding reported in the literature are in-lab tests15,24,25.
In this work, we report the successful transmission of hybrid time-path Hi-D quantum states with a final secret key rate (SKR) of 51.5 kbps through a 52-km long multicore fiber link exhibiting 22 dB of channel loss, deployed in the city of L’Aquila, Italy26. Our experiment paves the way towards the deployment of future Hi-D QKD systems in real scenarios.
Results
Experimental Implementation
We performed the 4D time-path-encoding QKD field trial experiment in a 52-km multicore fiber deployed in the city of L’Aquila, Italy. The fiber loop was characterized by 22 dB of losses, mostly due to fiber connectors. The implemented protocol is a 4-dimensional generalization of BB84, where weak coherent pulses form the quantum states. In order to detect photon-number splitting attacks, Alice and Bob run a two-decoy-state protocol, using states with unequal mean photon numbers μ1 and μ2, together with the vacuum state27,28. Alice transmits the signal states with probabilities and , whose values result from the optimization of the secure key generation rate. The transmitted states are modulated in the or , the two mutual unbiased bases, with probabilities and , respectively. A detailed description of the protocol is provided in the Methods section.
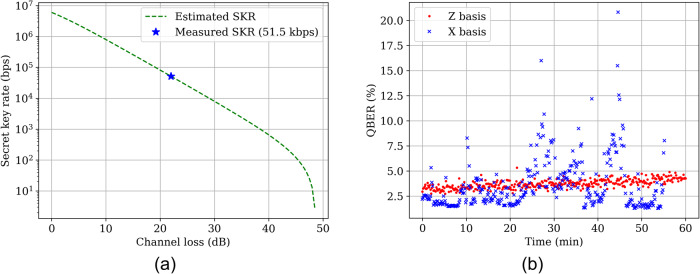
Figure 1 a is a plot of the expected secret key rates versus channel loss in the 4D protocols. The secret key rate is evaluated based on the experimental parameters of Table 129, where and are the quantum bit-error rates measured for the and bases, respectively, and for an average photon number μn (n = 1, 2), and pgate is the probability that a photon falls within the photodetection temporal gate. The values of and , as well as those of and resulted from the maximization of the secret key rate. Note that although the Hi-D protocols provide higher resilience against errors, the final achievable range is shorter, and the SKR drops to zero at lower channel losses. The reason for this behavior must be found in the fact that a higher-dimensional system uses more detectors (or more active time of a detector in hybrid time-bin protocols) than a protocol with a lower dimension, and this results in higher dark count rates and lower signal-to-noise ratio, see Supplementary Note 1. At the channel loss of 22 dB the secret key rate of the 4D protocol was estimated to be 51.5 kbps. The stability of the QKD implementation is illustrated in Fig. 1b, where we plot the QBER measured in the and bases in a time window of 60 minutes. The figure shows greater stability in the basis, which indicates that the relative phase between pulses propagating in the different fiber cores is sufficiently stable to guarantee long-term operation. On the other hand, the relative phase between pulses propagating in the same fiber core is expected to be at least as stable. In fact, the large QBER values observed in the basis are to be ascribed to mechanical vibrations present in the environment and affecting the fiber-based interferometer used for receiving -states. Note that these QBER spikes are absent in controlled laboratory environments30 and can be improved by acting on the receiver setup (improved isolation). On the other hand, the Z-basis phase which corresponds to the full multicore fiber interferometer, was intact as it was only influenced by the natural phase drift in the fiber. We compared the 4D implementation with a 2D path-encoded implementation in the same setup. The results of this comparison are presented in Supplementary Note 1.
Fig. 1. Experimental results.
a Secret key generation rate as a function of the channel loss for the parameters of the implementation. The star represents the achieved generation rate at the field-deployed channel loss. b Long-term stability of the implementation. Each point represents 10 seconds of measurement. While the basis shows great stability over time - an indication of slow phase drift in the fiber—the basis shows moments of high QBER due to vibration at the receiver site.
Table 1.
Experimental parameters
| Parameter | 4D |
|---|---|
| μ1 (μ2) | 0.36 (0.16) |
| () | 0.81 (0.11) |
| 2.15% | |
| 2.43% | |
| 3.54% | |
| 3.88% | |
| pgate | 0.53 |
Measured QBERs, and achieved key rates in both bases, for the transmitted bases in the 4D protocol. The measured channel loss is 22 dB.
Discussion
High-dimensional QKD protocols are introduced and designed for their higher capacity and resilience against noise. This, in turn, yields a higher secure-key generation rate compared to standard 2D counterparts for approximately similar QBER values7,8. However, depending on the physical properties that are used to encode information, the practical implementation of a Hi-D QKD system may result in fragile quantum states and poor performance (e.g. in terms of QBER). For instance, qudits based on the orbital angular momentum (OAM) of light suffer from crosstalk in optical fiber and turbulence in free space. In this work, through a field trial in a realistic urban environment, we demonstrate that path-encoding based on the use of multicore fibers is a robust scheme, standing out as a promising candidate for future Hi-D QKD systems. The robustness of this scheme is a consequence of the slow phase drift in deployed multicore fibers, which can be effectively tracked with the PLL developed for the field trial.
It is important to stress that, while in this work 4D states were formed in a time-path Hilbert space, in principle it is possible to generate Hi-D states with path-encoding alone. The advantage of avoiding time-bin encoding is an increase in quantum-state-generation rate, however, this approach requires stabilizing the phase of a larger number of spatial paths. Photonic integrated circuits (PICs) are an effective platform for the implementation of path-encoded Hi-D state sources and receivers31,32, and are intrinsically scalable to large dimensions. For comparison, we listed multiple Hi-D studies indicating relevant parameters and the final SKR in Supplementary Note 2. Additionally, we added to the comparison some of the recent works in Supplementary Note 3 with normalized SKR per source repetition rate and the number of detectors with their efficiencies. This aims to provide a fair comparison taking into account only the protocol, its implementation, and the receiver’s efficiency.
To summarize, we have demonstrated a Hi-D QKD system based on path-and-time-bin-encoding in a 52-km-long multicore fiber link field-deployed in the historical downtown area of the city of L’Aquila, Italy. Our results show higher noise tolerance of the proposed Hi-D scheme, compared to a reference 2D scheme, see Supplementary Note 1, as well as an enhanced secret key generation rate. This work paves the way toward the practical implementation of future Hi-D QKD systems.
Methods
A complete description of the experimental setup is presented in supplementary note 4.
Source
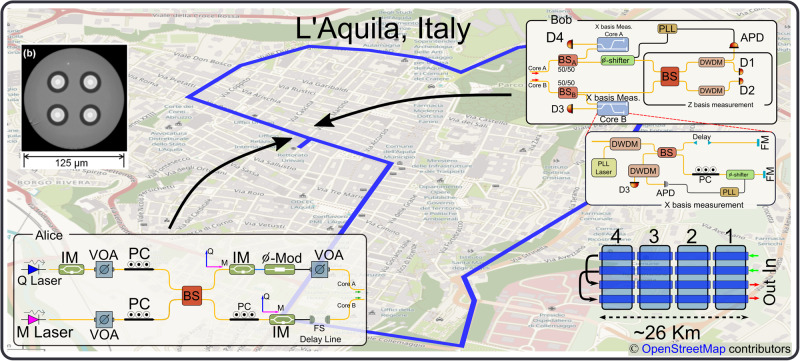
A detailed representation of the source structure is given in Fig. 2 -Alice box. A continuous wave laser, labeled as Q, is carved to form a train of 120 ps-long time-bin pulses with two cascaded intensity modulators, shown as one in the diagram, for a high extinction ratio. The state’s repetition rate is 487 MHz with the two pulses of a time-bin state being separated in time by 800 ps. The carving follows a pseudo-random binary sequence of length l = 212−1, which is used to emulate random quantum state generation. Carving the pulses out of a CW laser increases the chance of phase correlation between consecutive qudits. It is necessary to devise a phase randomization stage to close the loophole and prevent attacks33–35. A second continuous wave laser, labeled as M, is attenuated and multiplexed with the quantum signal through a beam-splitter, and it serves as a monitor laser for the dual-band phase locking scheme. The two outputs of the beam-splitter impinge upon two electro-optical modulators (EOMs) that encode information into four-dimensional quantum states. To optimize the effect of the EOMs on the quantum signal and prevent undesired modulation in the monitor laser, the polarization of the quantum signal is aligned with the EOM ordinary axis and that of the monitor laser with the extraordinary axis. The polarization alignment is achieved by means of the three polarization controllers shown in the figure. Insertion loss in the two spatial paths is equalized with the use of a variable optical attenuator, while a free-space delay line is used to equalize the corresponding propagation delays and maximize visibility in the reception of -states.
Fig. 2. Illustration of the setup.
Schematic of transmitter (Alice), receiver (Bob) both located at the University of L'Aquila headquarters, and multicore fiber channel. Transmitter. Q (M) Laser Quantum (Monitor) Laser, IM Intensity modulator, VOA Variable Optical Attenuator, PC Polarization Controller, ϕ-Mod Phase Modulator, BS Beam-splitter, FS Free-Space. Receiver. PLL Phase-Locked Loop, ϕ-shifter Piezo Phase Shifter, DWDM Dense Wavelength Division Multiplexer, APD Avalanche Photo-Diode, FM Faraday Mirror. Channel. Channel is formed by concatenating four multicore fibers with four uncoupled cores, each of approximately 6.5-km length. At the endpoint, two cores are connected back into the others, resulting in a 52-km-long two-core fiber link. The multicore fibers are deployed in an underground tunnel in the historical downtown area of the city of L'Aquila, Italy. The map depicting the city of L'Aquila and the span of the multicore fiber is roughly drawn based on the exact map presented in ref. 26. b The cross-section of the MCF. The four cores and the trench design are visible in the photo26.
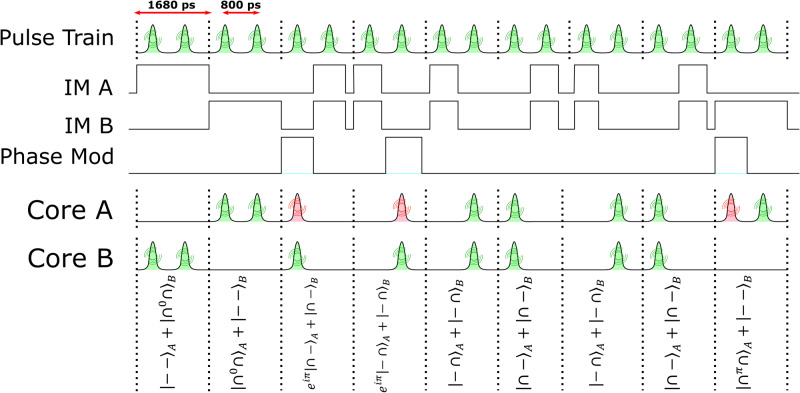
The state encoding process is illustrated in Fig. 3. The train of pulse pairs, with each pulse forming a time-bin state, is intensity-modulated at the output of the beam-splitter so that either a -state or an -state is generated in each time slot. For the former, one pulse of a pair of subsequent pulses is suppressed in each spatial path, whereas for the latter, both pulses of a pair of subsequent pulses are suppressed in one of the two spatial paths. A phase modulator then applies a phase ϕ ∈ {0, π} to generate .
Fig. 3. High dimensional state generation.
Two replicas of a periodic train of pulse pairs are intensity-modulated at the output of a beam-splitter, prior to transmission in fiber cores A and B, while only the replica in the path to core A is also phase-modulated, so as to generate states in the and bases. An RF signal is used to synchronize modulation in the two spatial paths, where the modulation signals are produced by a field-programmable gate array. Examples of the signals transmitted in two fiber cores are shown in the lower part of the figure, along with the corresponding quantum states.
All the EOM modulators are driven by a field-programmable gate array that also provides a down-sampled clock signal for synchronization to both the transmitter and receiver.
Phase stabilization
We employed the dual-band phase stabilization technique to compensate for relative phase drifts between the two fiber cores. The monitor signal, launched at a frequency 400 GHz lower than that of the quantum signal, is co-propagated with the quantum signal and experiences similar phase changes. At the receiver (for any basis choice), two cascaded dense wavelength division multiplexers (DWDMs), each with 25–30 dB isolation, are used to demultiplex the quantum and monitor/PLL signals, and to effectively suppress out-of-band noise impairing the quantum signal. The avalanche photodiodes produce suitable signals for the PLL circuits with a monitor-signal power of approximately - 45 dBm, which is the value targeted with the monitor signal launch power used in the experiment. The PLL features an ADuC7020 micro-controller unit (MCU) from Analog Devices with four 12-bit analog to digital converters (ADCs) and 41.78 MHz clock rate. It produces a feedback signal that is used to control a phase shifter, as can be seen in Fig. 2. Details on the PLL design can be found in ref. 36.
Receiver
The receiver (Bob) is composed of two 2 × 2 beam-splitters, BSA and BSB, placed in each core to passively select the basis of measurement. One output of each beam-splitter is used for -basis measurements, while the other two outputs are used for -basis measurements. The -basis receiver scheme is implemented in the form of a fiber-based unbalanced Michelson interferometer, with 800 ps temporal delay in one arm.
One output of each beam-splitter enters an unbalanced Michelson interferometer that implements the -basis measurements, while the other two outputs are used for -basis measurements.
The unbalanced Michelson interferometer is fiber-based, with 800 ps temporal delay in one arm. A PLL with an additional laser source at the same frequency of the monitor laser is used to compensate for unavoidable phase drifts. The monitor laser signal transmitted with the quantum signal is too weak to be used in the PLL and does not interfere with the locally added laser signal. (PLL laser in Fig. 2). Two DWDMs are used to multiplex and demultiplex the PLL laser and the -signal state to be received. Other parts of the interferometer are two Faraday mirrors used to compensate for polarization rotations due to fiber propagation, and a free-space delay element, needed to compensate for differential propagation delays in the two arms. the overall loss of the interferometer is around 4 dB.
The -basis measurement is performed by interfering signals in the two cores on a beam-splitter, and the quantum signal is extracted by means of two DWDMs prior to detection. The combined DWDMs for isolation add 1.5 dB of loss. The monitor signal from one of the two DWDMs feeds an APD to provide feedback to the PLL circuit.
All the detectors used for the quantum signals are superconducting nanowire single-photon detectors.
Protocol
Here, we describe the protocol that allows Alice and Bob to establish a common secure key using 4D time-path encoding.
Alice prepares the states described in the “section Source” and sends them through the quantum channel. The bases are chosen randomly with probabilities and , and the states are prepared also randomly with no memory. As a countermeasure against photon-number splitting attacks, a decoy-state protocol is implemented, where the mean-photon number of each quantum state is adjusted to two pre-selected values with probabilities and .
Bob randomly selects a basis and performs the measurement. In our implementation, a beam-splitter passively chooses the basis of measurement.
After a round of transmission and measurement, Alice and Bob communicate the basis of state preparation and measurement. At this stage, they discard all the instances in which the preparation and measurement bases mismatch.
Out of the remaining instances of exchanged qudits, Alice and Bob publicly reveal part of the prepared states and measurement outcomes to estimate the quantum bit error rate.
The remaining qudits yield two bits of information per detection instance, on which error reconciliation and privacy amplification are applied, ending with the establishment of a shared secure key.
Quantum channel
The protocol implemented in this work expands the Hilbert space dimension of a 2D time-bin protocol into a 4D space by adding the path dimension. The protocol requires two optical paths or channels to encode information in the relative phase of the two paths. In our implementation, the spatial paths are the cores of four 6.5-km long uncoupled-core four-core optical fibers deployed in the city of L’Aquila, Italy. The characteristics of the individual cores are similar to those of standard single-mode fibers, with negligible crosstalk between cores (below—40 dB/km)26,37. Each fiber is terminated by a spliced SC MCF connector on both ends. This allows to concatenate all the available fibers and form a 26-km fiber link. The resulting quantum channel length is 52 km, since only two cores are used for the path encoding, allowing to connect and loop back two cores into the other two. The overall fiber loss is measured to be 22 dB, of which 12 dB are to be ascribed to the SC MCF connectors and the fan-in/fan-out connectors.
Parameter optimization
In order to maximize the gain in this implementation, we optimized the 4D final secret key rate, Eq. (1) where the parameters are given in Table 1.
The secret key length ℓ4D is estimated in a finite-block-size regime with secrecy parameter , correctness parameter ϵcorr, and post-processing block size n in 4D with38
| 1 |
where and are the lower bounds of vacuum and single-photon events in the Z basis, is the Shannon entropy for 4D variables, ϕZ is the phase error rate upper bound, and λEC is the number of bits that are publicly disclosed during error correction38. The term bounds the information that Eve has about the key, while corresponds to the bit disclosed during error verification; ϵsec = ϵcorr = 10−12 have been set. We chose a block size of nZ = 108 for finite key analysis for 4D protocol, and we estimated for the 4D states an error reconciliation efficiency ferr,4D = λEC/(nZ H4D(ϕZ)) = 1.06, which is in line with the most recent results reported in the literature for the measured QBER values adopting the original cascade error correction protocol39.
Parameters such as mean photon numbers for signal and decoy state, μ1 and μ2 respectively, probabilities of transmitting signal and decoy, and , and probabilities of basis choice, and , are chosen to maximize the secret key rate. In the optimization, security parameters, channel loss, detector efficiencies, and dark counts are also taken into account.
Supplementary information
Acknowledgements
C.A. and A.M. are funded by QUID (Quantum Italy Deployment) funded by the European Commission in the Digital Europe Programme under the grant agreement No 101091408., L.O. received funding from the Center of Excellence SPOC (ref DNRF123), A.Z. received funding from the Project QuONTENT under the Progetti di Ricerca, CNR program funded by the Consiglio Nazionale delle Ricerche (CNR) and by the European Union—PON Ricerca e Innovazione 2014-2020 FESR—Project ARS01/00734 QUANCOM. D.B received funding from the IFD DK project Fire-Q (No. 9090-00031B), by EQUO (European Quantum Ecosystem) funded by the European Commission in the Digital Europe Programme under the grant agreement No 101091561 and by the European Union ERC project QOMUNE (101077917). The authors acknowledge OpenStreetMap40 for providing the map of L’Aquila City, Italy.
Author contributions
D.B., A.Z., and M.Z. conceived the research idea and designed the experiment. M.Z., D.R., A.Z., and D.B. performed the measurements; M.Z., D.R., C.D.L., I.V., N.B., R.M. performed the data analysis, M.Z., D.R., C.A., A.M., and D.B. wrote the manuscript. L.K.O., T.O., M.G., D.C. provided critical feedback together with all authors. T.H., C.A., A.M., and D.C. facilitate access to the fiber infrastructure.
Peer review
Peer review information
Nature Communications thanks Dong-Dong Li and the other, anonymous, reviewer(s) for their contribution to the peer review of this work. A peer review file is available.
Data availability
The data that support the findings of this study are available from the corresponding authors upon request.
Competing interests
The authors declare no competing interests.
Footnotes
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
The online version contains supplementary material available at 10.1038/s41467-024-45876-x.
References
- 1.Cisco: Cisco Annual Internet Report - white paper. https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-internet-report/white-paper-c11-741490.pdf (2018).
- 2.Rivest RL, Shamir A, Adleman L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM. 1978;21:120–126. doi: 10.1145/359340.359342. [DOI] [Google Scholar]
- 3.Bernstein DJ, Lange T. Post-quantum cryptography. Nature. 2017;549:188–194. doi: 10.1038/nature23461. [DOI] [PubMed] [Google Scholar]
- 4.Huttner B, et al. Long-range qkd without trusted nodes is not possible with current technology. npj Quantum Inf. 2022;8:108. doi: 10.1038/s41534-022-00613-4. [DOI] [Google Scholar]
- 5.Stas P-J, et al. Robust multi-qubit quantum network node with integrated error detection. Science. 2022;378:557–560. doi: 10.1126/science.add9771. [DOI] [PubMed] [Google Scholar]
- 6.Pirandola S, Laurenza R, Ottaviani C, Banchi L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 2017;8:15043. doi: 10.1038/ncomms15043. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7.Sheridan L, Scarani V. Security proof for quantum key distribution using qudit systems. Phys. Rev. A. 2010;82:030301. doi: 10.1103/PhysRevA.82.030301. [DOI] [Google Scholar]
- 8.Cerf NJ, Bourennane M, Karlsson A, Gisin N. Security of quantum key distribution using d-level systems. Phys. Rev. Lett. 2002;88:127902. doi: 10.1103/PhysRevLett.88.127902. [DOI] [PubMed] [Google Scholar]
- 9.Bechmann-Pasquinucci H, Tittel W. Quantum cryptography using larger alphabets. Phys. Rev. A. 2000;61:062308. doi: 10.1103/PhysRevA.61.062308. [DOI] [Google Scholar]
- 10.Shor PW, Preskill J. Simple proof of security of the bb84 quantum key distribution protocol. Phys. Rev. Lett. 2000;85:441–444. doi: 10.1103/PhysRevLett.85.441. [DOI] [PubMed] [Google Scholar]
- 11.Kues M, et al. On-chip generation of high-dimensional entangled quantum states and their coherent control. Nature. 2017;546:622–626. doi: 10.1038/nature22986. [DOI] [PubMed] [Google Scholar]
- 12.Mirhosseini M, et al. High-dimensional quantum cryptography with twisted light. N. J. Phys. 2015;17:033033. doi: 10.1088/1367-2630/17/3/033033. [DOI] [Google Scholar]
- 13.Cozzolino D, et al. Orbital angular momentum states enabling fiber-based high-dimensional quantum communication. Phys. Rev. Appl. 2019;11:064058. doi: 10.1103/PhysRevApplied.11.064058. [DOI] [Google Scholar]
- 14.Cozzolino D, et al. Air-core fiber distribution of hybrid vector vortex-polarization entangled states. Adv. Photonics. 2019;1:046005. doi: 10.1117/1.AP.1.4.046005. [DOI] [Google Scholar]
- 15.Cañas G, et al. High-dimensional decoy-state quantum key distribution over multicore telecommunication fibers. Phys. Rev. A. 2017;96:022317. doi: 10.1103/PhysRevA.96.022317. [DOI] [Google Scholar]
- 16.Da Lio B, et al. Stable transmission of high-dimensional quantum states over a 2-km multicore fiber. IEEE J. Sel. Top. Quantum Electron. 2020;26:1–8. doi: 10.1109/JSTQE.2019.2960937. [DOI] [Google Scholar]
- 17.Jo Y, Park HS, Lee S-W, Son W. Efficient high-dimensional quantum key distribution with hybrid encoding. Entropy. 2019;21:80. doi: 10.3390/e21010080. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 18.Wang F-X, et al. Characterizing high-quality high-dimensional quantum key distribution by state mapping between different degrees of freedom. Phys. Rev. Appl. 2019;11:024070. doi: 10.1103/PhysRevApplied.11.024070. [DOI] [Google Scholar]
- 19.Islam NT, Lim CCW, Cahall C, Kim J, Gauthier DJ. Provably secure and high-rate quantum key distribution with time-bin qudits. Sci. Adv. 2017;3:1701491. doi: 10.1126/sciadv.1701491. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 20.Steinlechner F, et al. Distribution of high-dimensional entanglement via an intra-city free-space link. Nat. Commun. 2017;8:15971. doi: 10.1038/ncomms15971. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 21.Martin A, et al. Quantifying photonic high-dimensional entanglement. Phys. Rev. Lett. 2017;118:110501. doi: 10.1103/PhysRevLett.118.110501. [DOI] [PubMed] [Google Scholar]
- 22.Cheng, X. et al. Secure high dimensional quantum key distribution based on wavelength-multiplexed time-bin encoding. In: Conference on Lasers and Electro-Optics, pp. 1–3. Optica Publishing Group, STh1D.3. 10.1364/CLEO_SI.2021.STh1D.3 (2021).
- 23.Jørgensen AA, et al. Petabit-per-second data transmission using a chip-scale microcomb ring resonator source. Nat. Photon. 2022;16:798–802. doi: 10.1038/s41566-022-01082-z. [DOI] [Google Scholar]
- 24.Ding Y, et al. High-dimensional quantum key distribution based on multicore fiber using silicon photonic integrated circuits. npj Quantum Inf. 2017;3:25. doi: 10.1038/s41534-017-0026-2. [DOI] [Google Scholar]
- 25.Da Lio B, et al. Path-encoded high-dimensional quantum communication over a 2-km multicore fiber. npj Quantum Inf. 2021;7:63. doi: 10.1038/s41534-021-00398-y. [DOI] [Google Scholar]
- 26.Hayashi, T. et al. Field-deployed multi-core fiber Testbed 10.23919/PS.2019.8818058 (2019).
- 27.Hwang W-Y. Quantum key distribution with high loss: toward global secure communication. Phys. Rev. Lett. 2003;91:057901. doi: 10.1103/PhysRevLett.91.057901. [DOI] [PubMed] [Google Scholar]
- 28.Lo H-K, Ma X, Chen K. Decoy state quantum key distribution. Phys. Rev. Lett. 2005;94:230504. doi: 10.1103/PhysRevLett.94.230504. [DOI] [PubMed] [Google Scholar]
- 29.Islam NT, Lim CCW, Cahall C, Kim J, Gauthier DJ. Securing quantum key distribution systems using fewer states. Phys. Rev. A. 2018;97:042347. doi: 10.1103/PhysRevA.97.042347. [DOI] [Google Scholar]
- 30.Ribezzo D, et al. Deploying an inter-european quantum network. Adv. Quantum Technol. 2023;6:2200061. doi: 10.1002/qute.202200061. [DOI] [Google Scholar]
- 31.Bacco D, Ding Y, Dalgaard K, Rottwitt K, Oxenløwe LK. Space division multiplexing chip-to-chip quantum key distribution. Sci. Rep. 2017;7:12459. doi: 10.1038/s41598-017-12309-3. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 32.Wang J, et al. Multidimensional quantum entanglement with large-scale integrated optics. Science. 2018;360:285–291. doi: 10.1126/science.aar7053. [DOI] [PubMed] [Google Scholar]
- 33.Gottesman, D., Lo, H.-K., Lutkenhaus, N. & Preskill, J. Security of quantum key distribution with imperfect devices. In: International Symposium onInformation Theory, 2004. ISIT 2004. Proceedings 136 (2004).
- 34.Tang Y-L, et al. Source attack of decoy-state quantum key distribution using phase information. Phys. Rev. A. 2013;88:022308. doi: 10.1103/PhysRevA.88.022308. [DOI] [Google Scholar]
- 35.Sun S, Huang A. A review of security evaluation of practical quantum key distribution system. Entropy. 2022;24:260. doi: 10.3390/e24020260. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 36.Bacco D, et al. Characterization and stability measurement of deployed multicore fibers for quantum applications. Photon. Res. 2021;9:1992–1997. doi: 10.1364/PRJ.425890. [DOI] [Google Scholar]
- 37.Luis, R.S. et al. Evaluation of dynamic skew on spooled and deployed multicore fibers using o-band signals. In: 2020 Optical Fiber Communications Conference and Exhibition (OFC) 1–3 (2020). https://ieeexplore.ieee.org/document/9083203.
- 38.Vagniluca I, et al. Efficient time-bin encoding for practical high-dimensional quantum key distribution. Phys. Rev. Appl. 2020;14:014051. doi: 10.1103/PhysRevApplied.14.014051. [DOI] [Google Scholar]
- 39.Mueller, R. et al. Efficient Information Reconciliation for High-Dimensional Quantum Key Distribution. arXiv 2307.02225 (2023).
- 40.OpenStreetMap. https://www.openstreetmap.org/copyright Accessed 2023-09-30.
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
Data Availability Statement
The data that support the findings of this study are available from the corresponding authors upon request.