Abstract
The efficient management of diseases, pests, or endangered species is an important global issue faced by agencies constrained by limited resources. The management challenge is even greater when organisms are difficult to detect. We show how to prioritize management and survey effort across time and space for networks of susceptible–infected–susceptible subpopulations. We present simple and robust rules of thumb for protecting desirable, or eradicating undesirable, subpopulations connected in typical network patterns (motifs). We further demonstrate that these rules can be generalized to larger networks when motifs are combined in more complex formations. Results show that the best location to manage or survey a pest or a disease on a network is also the best location to protect or survey an endangered species. The optimal starting point in a network is the fastest motif to manage, where line, star, island, and cluster motifs range from fast to slow. Managing the most connected node at the right time and maintaining the same management direction provide advantages over previously recommended outside–in strategies. When a species or disease is not detected and our belief in persistence decreases, our results recommend shifting resources toward management or surveillance of the most connected nodes. Our analytic approximation provides guidance on how long we should manage or survey networks for hard-to-detect organisms. Our rules take into account management success, dispersal, economic cost, and imperfect detection and offer managers a practical basis for managing networks relevant to many significant environmental, biosecurity, and human health issues.
Keywords: conservation planning, decision theory, metapopulation, optimization, Markov decision process
Infectious diseases, invasive pests, and other threats to species persistence have profound impacts on human health, agriculture, and biodiversity (1–3). Many threatened or invasive species are difficult to detect and their presence in an area can be uncertain due to the imperfect nature of most detection methods (4, 5). Even large charismatic mammals such as the Sumatran tiger (Panthera tigris sumatrae) or the Sumatran rhinoceros (Dicerorrhinus sumatrensis) can be surprisingly hard to detect. It is possible that some areas are being managed while the invasive pests, diseases, or threatened species have already disappeared. It is also likely that managers, in the absence of sighting, might stop managing too early and give up too soon on a species or disease (6, 7). Managers need to know when to stop managing or surveying for species in areas of particular interest.
At present the epidemiology, ecology, and conservation literature provides little guidance on how to approach such a problem. The problem of how to allocate management and surveillance effort has been studied for a single cryptic population (8–10). For example, Regan et al. (8) determined when to stop monitoring an invasive plant with a long-lived seed bank. Chadès et al. (9) determined when to stop managing or surveying cryptic threatened species. However, none of these works have accounted for multiple populations, spatial dispersal, or risk of reinfestation over time. When managing a cryptic invasive plant over time, Regan et al. (11) showed that accounting for imperfect detection but ignoring the risk of reinfestation led to a low probability of eradication, defeating the purpose of an optimal management strategy. Other studies on managing metapopulations have accounted for spatial connectivity but have not included imperfect detection in a systematic manner (12–17).
Metapopulations can be modeled as susceptible–infected–susceptible (SIS) networks (18). In epidemiology and ecology, SIS infections are challenging to manage because a treated node (person or location) can be cured and reinfected (we use the term “infection” to refer to infectious disease incidence, infestation by invasive pests, and colonization by endangered species). SIS network models can represent sexually transmitted diseases (gonorrhea) (19), other infectious diseases (meningitis, plague, malaria, and sleeping sickness) (20), metapopulations of invasive or threatened (21) species, influence in a social network (22, 23), and computer viruses across physical networks (24, 25). Here, we build on lessons from previous empirical studies and theoretical frameworks for optimal decision making (26–28) to develop coherent guidance for allocating resources across time and space between three activities: managing, surveying, and doing nothing for networks of cryptic diseases, pests, and threatened species. In our case managing a disease or a pest means decreasing its presence, whereas managing a threatened species means increasing its presence. We represent the spatial structure of pest invasions, infectious diseases, and threatened metapopulations (29) as “infected” and “susceptible” nodes in networks (18, 30, 31). The pest, disease, or threatened species can spread from an infected node to a susceptible node with which it shares a direct connection (32). We tackle our problem by first assuming a perfect detection process. We frame our optimization problem as a finite Markov decision process (33) and apply the solution to network motifs (34) (lines, islands, and stars) and combinations of motifs. Network motifs are small subgraphs that capture specific patterns of interactions. Studying optimal strategies for network motifs provides important insight into the management of more complex networks. We include imperfect detection into our model and analyze how the management strategy changes as our belief in the presence of the species or disease decreases. Our simple, but robust, rules of thumb for efficient management take into account management success, dispersal, economic cost, and imperfect detection. Contrary to previous high-profile work on large-scale networks (31, 35–37), we find that an “outside–in” control strategy for preventing the spread of infection is inefficient for network motifs. This is a key finding because eradication or effective control is generally possible only where a pest or a disease occupies a small number of nodes (38). Likewise, managing rare or threatened metapopulations is by definition a small network problem.
The first step in solving a resource allocation problem is defining the objective we seek to achieve. When managing pests and diseases, our objective is to minimize the number of infected nodes by taking actions to increase the probability of extinction of an infected node. When managing threatened species, our objective is to maximize the number of infected (occupied) nodes by taking actions that decrease the probability of extinction of an infected node. These equivalent problems have the same solution. The best local population to manage for an infestation is also the best place to manage for a threatened metapopulation.
At each time step, we assume the infection state of each node i (si = {susceptible, infected}) is observed. Once managed, a node can remain infected with probability (1 − pm) and infect susceptible nodes to which it is connected with a probability pd. When management occurs, the node may become susceptible and can be reinfected with probability 1 − (1 − pd)δ, where δ is the number of infected nodes directly connected to the susceptible node. We assume that each infected node has a probability of becoming susceptible without management (pe), to account for the natural, stochastic decline of the infection. We assign an economic cost, c, every year that results from a node being infected. Managing a node incurs a cost cm. We consider that only one node can be managed at a time. This method is the simplest way to prioritize the order in which nodes are managed so that our objective is achieved in the most efficient way. We also demonstrate that our management rules are robust when several nodes can be managed at a time (Results and Methods). We assume uniform dispersal, management success, benefit, and cost across all nodes (Methods and Table S1). However, our method can accommodate changes and nonuniform assumptions in any of the following parameters: the probability of a node being infected if one neighbor is infected (pd), the probability of a node becoming susceptible if infected and not managed (pe), the probability of a node becoming susceptible if it has been managed (pm), the cost of a node being infected (c), and the cost of managing one node (cm).
Results
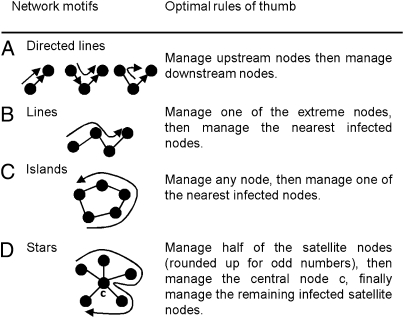
When two infected nodes have the same probability of infecting each other, the optimal strategy is to manage either one. When several nodes are linked by a directed probability of dispersal, it is optimal to manage the upstream node before managing the downstream nodes (Fig. 1A). In the case of a line network with bidirectional infection risk, the nodes at the extremity of the infection process have a lower probability of being reinfected than nodes with two neighbors. The optimal strategy is to start from either extremity of the network and then manage the nearest infected nodes sequentially (Fig. 1B). In the case of an island network, all nodes have an equal probability of being reinfected once managed; therefore, any node can be the starting point (Fig. 1C). Star networks are composed of a central node connected to satellite nodes. Infected satellite nodes are managed until the number of susceptible satellites is equal to or larger than the remaining number of infected satellites; it is then optimal to manage the central node before managing the remaining infected satellites (Fig. 1D). When managing star networks with lines of nodes of different lengths connected to a central node, the optimal strategy has three phases: (i) manage the longest lines from an outside–in direction until just over half of the nodes connected to the central node remain infected, (ii) manage the shortest infected line and the central node following an outside–in direction, and (iii) manage the remaining infected lines starting with the shortest lines following an inside–out direction.
Fig. 1.
(A–D) Optimal rules of thumb to manage network motifs of a disease or an invasive or threatened species.
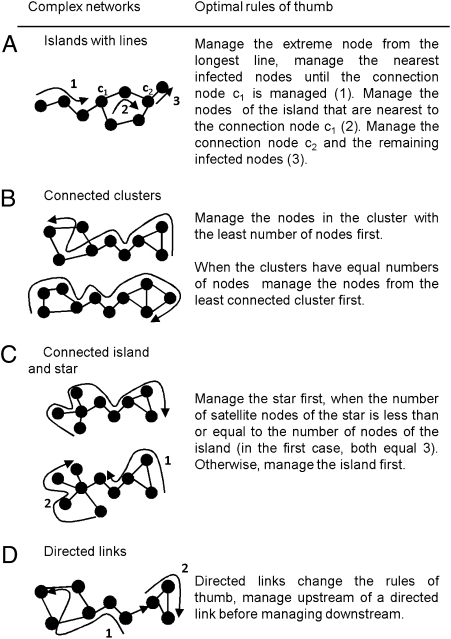
Fig. 2 shows simple rules of thumb for more complex networks made up of multiple motifs. When an island is connected to a line, the risk of reinfection is minimized by starting management at the extreme node of the line and continuing to the connecting node, before managing the island. Once the connecting node is susceptible, it is optimal to manage the infected nodes closest to the connecting node. A more complex configuration is an island connected to two lines (Fig. 2A). Maintaining the same management direction reduces the risk of reinfection and is therefore more efficient than managing the “outside” nodes first.
Fig. 2.
(A–D) Optimal rules of thumb to manage small complex networks of a disease or an invasive or threatened species.
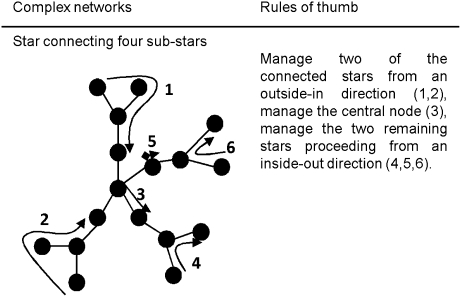
We define a cluster as an island with interconnected nodes. When managing connected clusters (Fig. 2B), it is optimal to start from the smallest cluster or, for the same number of nodes, the least connected cluster. For a connected island and star (Fig. 2C), the star is faster to manage when the number of satellites is equal to or smaller than the number of nodes of the island. In contrast, when the number of star satellites is greater than the number of island nodes, managing the island first reduces the chance of reinfection. In both cases, the rules of thumb derived from individual motifs can be applied. For a star connecting four substars (Fig. 3), the optimal rule of thumb for managing single star motifs holds.
Fig. 3.
Optimal management of a complex star network of a disease or an invasive or threatened species.
We compared our rules of thumb to an outside–in control strategy by simulating the management of 1, 2, and 5 nodes at a time on large star networks of 101 nodes (Figs. S1–S3). Our optimal strategy outperforms the outside–in strategy, reducing the time to eradication and the management required by 31.2% (90.7 treatments, managing 1 node), 10.7% (20.4 treatments, managing 2 nodes), and 3.3% (5.6 treatments, managing 5 nodes). Our rules are also robust to nonuniform dispersal probabilities (pd) and management success (pm) and consistently outperform the traditional outside–in strategy (Table S2 and SI Methods). We found that the relative benefits of our rules of thumb are greater when fewer patches are managed in each time step. Our rules of thumb outperform the outside–in strategy because reinfections are less likely to occur using our priority management order. The longer the time it takes to eradicate the infection, the more opportunity there is for reinfections to take place, and the greater the benefit of our rules of thumb over the outside–in strategy. By managing multiple patches in a time step, the time to eradication is reduced, making the performance of the two strategies more similar.
For all of the complex networks we examined, management starts with the fastest motif to manage, following the priority order line, star, island, and cluster. Management of the most connected node at the right time and maintaining the same management direction minimize the reinfection risk, providing potentially important practical advantages over outside–in strategies, particularly in the case of limited management resources. To determine the management starting point more easily we asked if a network centrality measure could substitute for our rules of thumb. Centrality measures are able to rank nodes in a network according to the topological features that they account for (see refs. 39–41 for more details). We calculated centrality measures for nine small networks (Table S3). We found that the closeness centrality measure correctly predicted the most appropriate node to start from for seven cases of nine but predicted incorrect starting nodes for the two networks characterized by connected clusters. Betweenness centrality, eigenvector centrality, and subgraph centrality (42) performed inadequately. Although closeness centrality often predicted the correct starting node, it did not predict an optimal priority management order, highlighting the continuing need for our optimization framework.
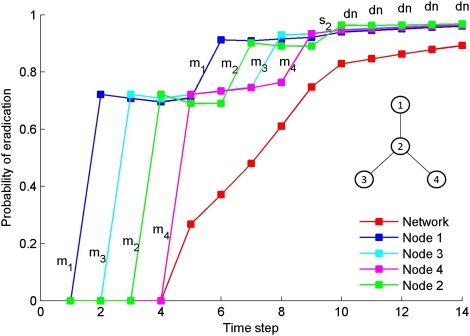
Most pests, diseases, and threatened species cannot be detected perfectly (9). Apparently susceptible nodes may, in fact, be infected. We extend our framework to take into account our inability to detect subpopulations perfectly, using the partially observable Markov decision process (POMDP) (Methods). In this case, we consider three possible management actions: Manage a node, survey for the infection, or do nothing. We include in our optimization model the probability of imperfectly detecting infected nodes, dn, when doing nothing or managing. Probability of detection increases when we survey a node, ds > dn. The cost of survey, cs, is set to half the cost of management. Using a star network of four nodes, we illustrate the importance of accounting for imperfect detection where we assume the infection is not observed after each action (see the parameters used in Table S1).
When all of the nodes in a star are initially infected (Fig. 4), the order of management follows the rules of thumb we described under perfect detection. After this first round of management, if the infection is not detected in any node, a stochastic dynamic programming solution recommends doing nothing; however, when accounting for imperfect detection, our results recommend managing all of the nodes a second time for this star network. The number of times a node must be managed depends on the POMDP parameters used. As our belief in eradication increases, our solution shifts to surveying the most connected node. Finally, when our belief that the infection has been eradicated from the network has reached a threshold (0.82 in the case of Fig. 4), and in the absence of observing an infection, “do nothing” becomes the optimal action. When we observe an infection to be present in a node(s), the belief of eradication falls to zero and “manage” is recommended.
Fig. 4.
Resource allocation recommended over time for the management of a hypothetical invasive species when infection may be undetected on a star network (Inset). mi, manage node i; si, survey node i; and dn, do nothing. The red line represents the probability (belief) of eradication of the infection from the network. The other lines represent the belief in eradication of the individual nodes. The probability of eradication starts at zero for each node because initially, the network is assumed to be infected.
When we do not have any prior information about the infection of the network, every infection state in every node is equally probable (Fig. S4). In this case, our solution recommends first managing all of the nodes at least once and more than once if the node is highly connected (e.g., node 2, Fig. S4). The action of surveillance then becomes optimal. In the absence of detection of the infection under surveillance, our belief that the infection is eradicated reaches a high value (e.g., probability of eradication in the network >0.82). It is then recommended to do nothing.
Under imperfect detection, as our belief in eradication increases, our control strategy evolves through three phases: Manage, survey, and do nothing. As demonstrated in Chadès et al. (9), the problem of when to stop managing and surveying a single population of cryptic species is dependent on the relative cost of survey and management, the cost of the infection, the benefits of eradication, and the efficiency of management and surveillance determine the switching points (9). To avoid rerunning the POMDP algorithms for every network studied, we build on this work and derive an analytic approximation by transforming our network POMDP problem into a single POMDP. To make the transformation, we assume the dispersal probability between nodes is a less important factor than the number of subpopulations (Methods). Although this assumption may not always hold, this approximation is the best indicator of how long we can afford to manage derived thus far and forms the basis for future theoretical work. We find that, in the absence of sighting, as the number of subpopulations increases, the time we should spend managing increases substantially irrespective of the economic costs (Fig. S5).
Discussion
We identify simple rules for the management of small networks under perfect and imperfect detection of susceptible–infected–susceptible network invasions, infections, and threatened metapopulations. Our findings provide guidance for managers in determining (i) where to prioritize management over time and space to achieve the most efficient control strategy and (ii) when the species or the disease is difficult to detect, how long they should invest in active management or in surveying and when it is reasonable to stop investing limited resources. Our simulation results demonstrate the improvement in performance when following our rules of thumb over traditional outside–in management approaches on large motif networks. Our rules are also robust to nonuniform distribution of dispersal and management efficiency. When deciding where we should prioritize management, a key finding is to start with the fastest motifs to manage and keep the same management direction through the network. Centrality measures are not good proxies for determining the priority order of management of nodes. Finally we derived an analytic approximation providing guidance on the time we should spend managing and surveying across a network in the absence of detection.
Details of the number of nodes, the costs and benefits of managing nodes, and the dispersal probability drive the optimal management strategies. In ecology and economics, evaluating the loss of a species or the impact of a pest or disease is a challenging and often highly subjective undertaking (43). We find that for a pest or disease with high management costs combined with a high dispersal probability a do nothing strategy can be optimal when control becomes unachievable under budget constraints. In contrast, high economic value of a threatened species and low detection probability result in management and surveying for longer periods of time being optimal (ref. 9 and Fig. S5).
To derive our rules of thumb we have assumed uniform dispersal across all nodes; however, infection/colonization processes can be driven by directed factors such as transport vectors (wind, water, or road dispersal). In this case, directed dispersal changes the management rules (Fig. 2D). Although our optimization tool can accommodate differences in parameters across a network, such information is often not available. In the absence of explicit information, expert elicitation can be used and these qualitative values can be incorporated into our framework (44).
We were able to derive management strategies for many different kinds of small networks (<25 nodes). Deriving a priority order of which nodes to manage is useful only for networks that exhibit a clear structure. Highly connected networks will not benefit from our approach as the amount of resources invested to manage the threat will be more important than the order of nodes managed. In other words networks need to be sparsely connected to benefit from our approach. If a structured network is found but the number of nodes is too large to be solved following our approach, we recommend using an abstraction process or decomposition methods to extract small subnetworks (45–47). An alternative approach is to use a model that does not include network structure at all, such as a diffusion process (48).
Managers of diseases might find our rules counterintuitive as we do not recommend managing the most connected nodes first. There are several plausible explanations for this. First, our rules provide a priority order of management from the initial condition of all nodes being infected. This order might not correspond to the starting management point of some diseases, e.g., when only a few nodes in a wider known network are infected. Although our optimal strategy defines an optimal action for any infection stage, it is impossible to derive a unique priority order that applies to every infection stage. Second, although common, the assumption that a node can represent the state of a subpopulation might not reflect epidemic dynamics; however, we can consider a node as a representation of an individual and our rules continue to apply to a network of infected individuals. Third, we assume the structure of the network is known. Therefore, the infection cannot spread to unknown connected nodes and managing the most connected node does not bring any additional advantage. Finally, the susceptible–infected–susceptible network model might not capture the complexity of some diseases where vaccinated or recovered and immune states are possible; other models such as susceptible–infected–recovered (SIR) might be more appropriate.
We present general solutions for the management of connected subpopulations of pests, diseases, and threatened species arranged in a SIS network. The efficient management of diseases, pests, or threatened species is a globally important issue, especially in agencies constrained by limited resources. The challenge of managing new incursions is even greater when the species or disease is cryptic and impossible to detect perfectly. To date, most of the literature in network theory has focused on making predictions about large complex systems such as food webs, epidemics, and gene regulation (49, 50). We provide general rules of thumb for setting management priorities in small networks, where our chances of eradication or recovery of a species are maximized (51). Our results provide a practical basis to manage SIS networks relevant to many significant biosecurity, human health, and environmental issues.
Methods
When there is perfect detection, finding the optimal management strategy for an infected network can be solved using Markov decision process (MDP) and stochastic dynamic programming (SDP) (33). In our case MDP is inconvenient for two reasons: The computational complexity grows exponentially with the number of nodes and SDP methods mostly provide a single optimal solution. Determining alternative optimal solutions is essential when deriving rules of thumb. We overcome these disadvantages by modeling our SIS network management problem as a factored Markov decision process (FMDP) (26), taking advantage of the structure of our problem and fast optimization methods from artificial intelligence.
A factored MDP is a MDP that explicitly represents the independent relationships between variables of the system (conditional independence). A factored MDP is defined by four elements: a factored set of states (S), a finite set of actions (A), a transition probability function (P), and a reward function (R). Let s in S be the state of the network at any given time t and s represent the nodes infected or the susceptible state: s = (s1, s2, … , sn), where the state variable si ∈ Si = {infected, susceptible} represents the state of the node i. The system has 2n possible states. Let a in A be the decision the manager can make at any given time t and a represent the nodes managed by the decision makers: a = (a1, a2, … , an), where the components ai ∈ Ai = {manage, do nothing}, the set of decisions available in node i. Because we are interested in the prioritization of management, we assume only one node can be managed at each time step. Our simulation results have shown that when we increase the number of nodes we can manage at a time, our rules continuously outperform the outside–in strategy (Results and SI Methods). As currently defined, our model and approach will still hold when more resources are available, allowing the management of several nodes at a time. However, the computational complexity is dependent on the number of actions we consider. If we were to consider managing k nodes among n at a time, the size of the action set grows with k, |A| = n!/(n − k)!, limiting the use of our methods to very small networks.
The dynamics of the system are captured by a matrix P that contains the transition probabilities of moving from any state to any other state of the system under different actions following the SIS process (Introduction and Fig. S6). In classical MDP solution methods, all transition probabilities must be represented and stored using |A| matrices of |S| by |S| dimensions. Each element of these matrices represents a transition probability: 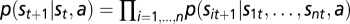 .
.
A factored MDP takes into account the independence between state variables explicitly, using a dynamic Bayesian network implemented as algebraic decision diagrams (ADD) (Fig. S6). For example, let us consider a line network with three nodes. The classic MDP needs to store the probabilities of transition for every state given all possible states of nodes 1, 2, and 3, even though node 1 does not affect the state of node 3 and vice versa. In this way the classic algorithms are inefficient because they store information that is not needed to find the optimal solution. A better way is to use the structure of the network to store information for the nodes that directly affect the state of nodes 3 and 1; e.g., p(s3t+1 | s3t, s2t, s1t, a) = p(s3t+1 | s3t, s2t, a) and p(s1t+1 | s3t, s2t, s1t, a) = p(s1t+1 | s2t, s1t, a)—this simplification is factored MDP. If an optimization problem has many independent variables, we can solve larger-size MDPs using factored MDP because we have fewer state interactions to consider and store. In our case, as the network studied becomes larger, the savings gained by representing the network dynamic increase exponentially.
When solving the corresponding optimization problem, we seek to determine an optimal strategy π : S → A that minimizes the expected number of nodes infected over an infinite time horizon. The optimal strategy matches an optimal action to each possible state of the system. For any network thus specified, we first determine the conditional dependence/independence between nodes over one time step. We automatically generate the corresponding FMDP model and solve the optimization process using the fast algorithm stochastic planning using decision diagrams (SPUDD) (27). We then analyze the solutions and derive clear management rules.
In reality many pests, diseases, and threatened species cannot be detected perfectly. A factored partially observable Markov decision process (FPOMDP) model is an augmented FMDP with a factored set of observations (Z) and an observation function (O). Similar to a factored MDP, a factored POMDP is a POMDP that explicitly represents the independent relationships between variables of the system. In our case the FPOMDP tackles the problem of deciding the most appropriate management action given the difficulty of detecting an infected node. We define the finite set of local observations for each node at time t, zi = {Absent, Present} and their corresponding observation function oi that maps to each state–action pair a probability distribution over zi. In other words, the probability of detection of the infection given that the node is infected and that the previous decision is to do nothing is defined by oi(Present | Infected, Do nothing). Let z in Z be an observation of the whole system z = {z1, … , zn}. We define the observation function of the system as the joint probability of the local observation function: O(z | s, a) = o1(z1 | s1, a1)x … x on(zn | sn, an).
As it is neither practical nor tractable to use the history of the action–observation trajectory to compute or represent an optimal solution, belief states are preferred to summarize and overcome the difficulties of incomplete detection. Indeed, Astrom (52) has shown that belief states are sufficient statistical tools to summarize all of the observable history of a POMDP without loss of optimality. A POMDP can be cast into a framework of a fully observable Markov decision process where belief states represent the continuous but fully observable state space. Here, a belief state b is defined as a distribution probability over states in S. In our case, solving a FPOMDP is finding a strategy 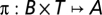 , mapping an allocation of resource a ∈ A given a current belief state b ∈ B and a time step t ∈ T. An optimal strategy minimizes the expected sum of costs or rewards (R) over a finite time horizon, T. This expected summation is also referred to as the value function (53). A value function essentially ranks strategies by assigning a real value to each b.
, mapping an allocation of resource a ∈ A given a current belief state b ∈ B and a time step t ∈ T. An optimal strategy minimizes the expected sum of costs or rewards (R) over a finite time horizon, T. This expected summation is also referred to as the value function (53). A value function essentially ranks strategies by assigning a real value to each b.
Whereas various algorithms from the operations research and artificial intelligence literature have been developed over the past years, the computational complexity of exact algorithms remains intractable for most problems: Finite horizon POMDPs are PSPACE-complete (54) and infinite-horizon POMDPs are undecidable (55). In the last few years, approximate methods have been developed to solve POMDPs (28, 56–59). Among these approaches we chose symbolic perseus, a point-based approach for factored POMDP. Point-based approaches approximate the value function by updating it only for some selected belief states. The point-based methods sample belief states by simulating some random interactions in the environment and then update the value function and its gradient over those sampled belief states. The symbolic perseus method (28) benefits from both the factored representations of FPOMDP using ADD and a fast point-based method using Perseus (58).
In summary, being able to model our optimization problems as a factored MDP (under perfect detection) or factored POMDP (under imperfect detection) is innovative and constitutes a key point of our work. Factored MDP and POMDP allow us to (i) compactly represent the optimization problems using trees and dynamic Bayesian networks, (ii) implement efficient computation using algebraic decision diagrams, and (iii) identify management rules by using decision trees to represent all of the optimal solutions in a structured way.
We derived an analytic solution for a population of invasive species following previous work by Chadès et al. (9) (SI Methods). We also derived an analytic approximation for n independent populations by transforming an n-population POMDP into a single POMDP (SI Methods and Fig. S5). Due to the high level of complexity of an n-population POMDP, we were unable to include interactions between populations. In most cases, interactions between populations are likely to increase the local persistence of each population. As a consequence, our approximation provides a lower time limit for which it is beneficial to manage or survey. This approximation constitutes a first step toward further theoretical development.
Supplementary Material
Acknowledgments
We thank J. Firn, R. McVinish, P. Pollett, A. Franc, A. Sheppard, and R. McAllister for discussions. We are grateful to P. Poupart and J. Hoey for making available their toolbox. This work was supported by the Australian Centre of Excellence for Risk Analysis (I.C. and M.A.B.), the Applied Environmental Decision Analysis (I.C., H.P.P., and S.N.), the Centre of Excellence for Mathematics and Statistics of Complex Systems (I.C.), Australian Research Council Australian Research Fellowships (to Y.M.B. and H.P.P.), a Julius Career award (to T.G.M.), and a Commonwealth Scientific and Industrial Research Organisation (CSIRO) Office of the Chief Executive postdoctoral fellowship (to I.C.).
Footnotes
The authors declare no conflict of interest.
This article is a PNAS Direct Submission.
This article contains supporting information online at www.pnas.org/lookup/suppl/doi:10.1073/pnas.1016846108/-/DCSupplemental.
References
- 1.Jones KE, et al. Global trends in emerging infectious diseases. Nature. 2008;451:990–993. doi: 10.1038/nature06536. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Pimentel D. Biological Invasions: Economic and Environmental Cost of Alien Plant, Animal, and Microbe Species. Boca Raton, FL: CRC; 2002. p. 384. [Google Scholar]
- 3.Chapin FS, 3rd, et al. Consequences of changing biodiversity. Nature. 2000;405:234–242. doi: 10.1038/35012241. [DOI] [PubMed] [Google Scholar]
- 4.MacKenzie DI, Kendall WL. How should detection probability be incorporated into estimates of relative abundance? Ecology. 2002;83:2387–2393. [Google Scholar]
- 5.MacKenzie DI, et al. Estimating site occupancy rates when detection probabilities are less than one. Ecology. 2002;83:2248–2255. [Google Scholar]
- 6.Stokstad E. Endangered species. U.S. announces recovery plan for a ghost bird. Science. 2007;317:1158. doi: 10.1126/science.317.5842.1158b. [DOI] [PubMed] [Google Scholar]
- 7.Fisher DO, Blomberg SP. Correlates of rediscovery and the detectability of extinction in mammals. Proc R Soc Biol Sci Ser B. 2011 doi: 10.1098/rspb.2010.1579. 10.1098/rspb.2010.1579. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 8.Regan TJ, McCarthy MA, Baxter PWJ, Dane Panetta F, Possingham HP. Optimal eradication: When to stop looking for an invasive plant. Ecol Lett. 2006;9:759–766. doi: 10.1111/j.1461-0248.2006.00920.x. [DOI] [PubMed] [Google Scholar]
- 9.Chadès I, et al. When to stop managing or surveying cryptic threatened species. Proc Natl Acad Sci USA. 2008;105:13936–13940. doi: 10.1073/pnas.0805265105. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.Hauser CE, McCarthy MA. Streamlining ‘search and destroy’: Cost-effective surveillance for invasive species management. Ecol Lett. 2009;12:683–692. doi: 10.1111/j.1461-0248.2009.01323.x. [DOI] [PubMed] [Google Scholar]
- 11.Regan TJ, Chadès I, Possingham HP. Optimal strategies for managing invasive plants in partially observable systems. J Appl Ecol. 2011;48:76–85. [Google Scholar]
- 12.Day JR, Possingham HP. A stochastic metapopulation model with variability in patch size and position. Theor Popul Biol. 1995;48:333–360. [Google Scholar]
- 13.Shea K, Possingham HP. Optimal release strategies for biological control agents: An application of stochastic dynamic programming to population management. J Appl Ecol. 2000;37:77–86. [Google Scholar]
- 14.Hastings A, et al. The spatial spread of invasions: New developments in theory and evidence. Ecol Lett. 2005;8:91–101. [Google Scholar]
- 15.Tilman D, Kareiva PM. Spatial Ecology: The Role of Space in Population Dynamics and Interspecific Interactions. Princeton, NJ: Princeton Univ Press; 1997. [Google Scholar]
- 16.Blackwood J, Hastings A, Costello C. Cost-effective management of invasive species using linear-quadratic control. Ecol Econ. 2010;69:519–527. [Google Scholar]
- 17.Moody ME, Mack RN. Controlling the spread of plant invasions: The importance of nascent foci. J Appl Ecol. 1988;25:1009–1021. [Google Scholar]
- 18.May RM. Network structure and the biology of populations. Trends Ecol Evol. 2006;21:394–399. doi: 10.1016/j.tree.2006.03.013. [DOI] [PubMed] [Google Scholar]
- 19.Hethcote HW, Yorke JA. Gonorrhea transmission dynamics and control. Lect Notes Biomath. 1984;56:1–110. [Google Scholar]
- 20.Allen LJS. Some discrete-time SI, SIR, and SIS epidemic models. Math Biosci. 1994;124:83–105. doi: 10.1016/0025-5564(94)90025-6. [DOI] [PubMed] [Google Scholar]
- 21.Hanski I. Metapopulation dynamics. Nature. 1998;396:41–49. [Google Scholar]
- 22.Wasserman S, Faust K. Social Network Analysis: Methods and Applications. Cambridge, UK: Cambridge Univ Press; 1994. [Google Scholar]
- 23.Saito K, Kimura M, Motoda H. Discovering influential nodes for SIS models in social networks. Lect Notes Comput Sci. 2009;5808:302–316. [Google Scholar]
- 24.Pastor-Satorras R, Vespignani A. Epidemic spreading in scale-free networks. Phys Rev Lett. 2001;86:3200–3203. doi: 10.1103/PhysRevLett.86.3200. [DOI] [PubMed] [Google Scholar]
- 25.Kephart JO, White SR, Chess DM. Computers and epidemiology. Spectrum IEEE. 2002;30(5):20–26. [Google Scholar]
- 26.Boutilier C, Dean T, Hanks S. Decision theoretic planning: Structural assumptions and computational leverage. J Artif Intell Res. 1999;11:1–94. [Google Scholar]
- 27.Hoey J, St-Aubin R, Hu A, Boutilier C. SPUDD: Stochastic planning using decision diagrams. In: Laskey K, Prade H, editors. Fifteenth Conference on Uncertainty in Artificial Intelligence. Sweden: Morgan Kaufmann, Stockholm; 1999. pp. 279–288. [Google Scholar]
- 28.Poupart P. Toronto: Univ of Toronto; 2005. Exploiting structure to efficiently solve large scale partially observable Markov decision processes. PhD thesis. [Google Scholar]
- 29.Levins R. Some demographic and genetic consequences of environmental heterogeneity for biological control. Bull ESA. 1969;15:237–240. [Google Scholar]
- 30.May RM, Nowak MA. Superinfection, metapopulation dynamics, and the evolution of diversity. J Theor Biol. 1994;170:95–114. doi: 10.1006/jtbi.1994.1171. [DOI] [PubMed] [Google Scholar]
- 31.Proulx SR, Promislow DEL, Phillips PC. Network thinking in ecology and evolution. Trends Ecol Evol. 2005;20:345–353. doi: 10.1016/j.tree.2005.04.004. [DOI] [PubMed] [Google Scholar]
- 32.Harris TE. Contact interactions on a lattice. Ann Probab. 1974;2:969–988. [Google Scholar]
- 33.Puterman ML. Markov Decision Processes: Discrete Stochastic Dynamic Programming. New York: Wiley; 1994. [Google Scholar]
- 34.Milo R, et al. Network motifs: Simple building blocks of complex networks. Science. 2002;298:824–827. doi: 10.1126/science.298.5594.824. [DOI] [PubMed] [Google Scholar]
- 35.Ferguson NM, et al. Strategies for containing an emerging influenza pandemic in Southeast Asia. Nature. 2005;437:209–214. doi: 10.1038/nature04017. [DOI] [PubMed] [Google Scholar]
- 36.Keeling MJ, Woolhouse MEJ, May RM, Davies G, Grenfell BT. Modelling vaccination strategies against foot-and-mouth disease. Nature. 2003;421:136–142. doi: 10.1038/nature01343. [DOI] [PubMed] [Google Scholar]
- 37.Ferguson NM, et al. Strategies for mitigating an influenza pandemic. Nature. 2006;442:448–452. doi: 10.1038/nature04795. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 38.Simberloff D. How much information on population biology is needed to manage introduced species? Conserv Biol. 2003;17:83–92. [Google Scholar]
- 39.Freeman LC. A set of measures of centrality based on betweenness. Sociometry. 1977;40:35–41. [Google Scholar]
- 40.Newman MEJ. Scientific collaboration networks. II. Shortest paths, weighted networks, and centrality. Phys Rev E Stat Nonlin Soft Matter Phys. 2001;64:016132. doi: 10.1103/PhysRevE.64.016132. [DOI] [PubMed] [Google Scholar]
- 41.Newman MEJ. The structure and function of complex networks. SIAM Rev. 2003;45:167–256. [Google Scholar]
- 42.Estrada E, Rodríguez-Velázquez JA. Subgraph centrality in complex networks. Phys Rev E Stat Nonlin Soft Matter Phys. 2005;71:056103. doi: 10.1103/PhysRevE.71.056103. [DOI] [PubMed] [Google Scholar]
- 43.Pearce DW, Moran D. The Economic Value of Biodiversity. London, UK: Earthscan; 1994. [Google Scholar]
- 44.Kuhnert PM, Martin TG, Griffiths SP. A guide to eliciting and using expert knowledge in Bayesian ecological models. Ecol Lett. 2010;13:900–914. doi: 10.1111/j.1461-0248.2010.01477.x. [DOI] [PubMed] [Google Scholar]
- 45.Palomar DP. A tutorial on decomposition methods for network utility maximization. IEEE J Sel Areas Comm. 2006;24:1439–1451. [Google Scholar]
- 46.Fortunato S, Barthélemy M. Resolution limit in community detection. Proc Natl Acad Sci USA. 2007;104:36–41. doi: 10.1073/pnas.0605965104. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 47.Reichardt J, Bornholdt S. Statistical mechanics of community detection. Phys Rev E Stat Nonlin Soft Matter Phys. 2006;74:016110. doi: 10.1103/PhysRevE.74.016110. [DOI] [PubMed] [Google Scholar]
- 48.Mollison D. Spatial contact models for ecological and epidemic spread. J R Stat Soc B. 1977;39:283–326. [Google Scholar]
- 49.Montoya JM, Pimm SL, Solé RV. Ecological networks and their fragility. Nature. 2006;442:259–264. doi: 10.1038/nature04927. [DOI] [PubMed] [Google Scholar]
- 50.Hufnagel L, Brockmann D, Geisel T. Forecast and control of epidemics in a globalized world. Proc Natl Acad Sci USA. 2004;101:15124–15129. doi: 10.1073/pnas.0308344101. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 51.Epanchin-Niell RS, Hastings A. Controlling established invaders: Integrating economics and spread dynamics to determine optimal management. Ecol Lett. 2010;13:528–541. doi: 10.1111/j.1461-0248.2010.01440.x. [DOI] [PubMed] [Google Scholar]
- 52.Astrom KJ. Optimal control of Markov decision processes with incomplete state estimation. J Math Anal Appl. 1965;10:174–205. [Google Scholar]
- 53.Cassandra AR, Kaelbling LP, Littman ML. National Conference on Artificial Intelligence. Seattle, WA: American Association for Artificial Intelligence; 1994. Acting optimally in partially observable stochastic domains; pp. 1023–1028. [Google Scholar]
- 54.Papadimitriou CH, Tsitsiklis JN. The complexity of Markov decision processes. Math Oper Res. 1987;12:441–450. [Google Scholar]
- 55.Madani O, Hanks S, Condon A. On the undecidability of probabilistic planning and related stochastic optimization problems. Artif Intell. 2003;147:5–34. [Google Scholar]
- 56.Hauskrecht M. Value-function approximations for partially observable Markov decision processes. J Artif Intell Res. 2000;13:33–94. doi: 10.1016/s0933-3657(99)00042-1. [DOI] [PubMed] [Google Scholar]
- 57.Pineau J, Gordon G, Thrun S. International Joint Conference on Artificial Intelligence. Acapulco, Mexico: Lawrence Erlbaum; 2003. Point-based value iteration: An anytime algorithm for POMDPs; pp. 1025–1032. [Google Scholar]
- 58.Spaan MTJ, Vlassis N. Perseus: Randomized point-based value iteration for POMDPs. J Artif Intell Res. 2005;24:195–220. [Google Scholar]
- 59.Smith T, Simmons R. Uncertainty in Artificial Intelligence. Arlington, VA: AUAI; 2004. Heuristic search value iteration for POMDPs; pp. 520–527. [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.