Abstract
Many high-profile societal problems involve an individual or group repeatedly attacking another – from child-parent disputes, sexual violence against women, civil unrest, violent conflicts and acts of terror, to current cyber-attacks on national infrastructure and ultrafast cyber-trades attacking stockholders. There is an urgent need to quantify the likely severity and timing of such future acts, shed light on likely perpetrators, and identify intervention strategies. Here we present a combined analysis of multiple datasets across all these domains which account for >100,000 events, and show that a simple mathematical law can benchmark them all. We derive this benchmark and interpret it, using a minimal mechanistic model grounded by state-of-the-art fieldwork. Our findings provide quantitative predictions concerning future attacks; a tool to help detect common perpetrators and abnormal behaviors; insight into the trajectory of a ‘lone wolf'; identification of a critical threshold for spreading a message or idea among perpetrators; an intervention strategy to erode the most lethal clusters; and more broadly, a quantitative starting point for cross-disciplinary theorizing about human aggression at the individual and group level, in both real and online worlds.
Human confrontations1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25 from one-on-one fights3,4,5 through to collective protests6,7,8,9,10, mass violence11,12,13,14,15,16,17,18,19,20,21,22,23 and even online acts of aggression24,25, are of great societal importance. However our understanding of the dynamics at the event-by-event level remains limited (e.g. a child's repeated cry-attacks against a parent3,4,5) where each side (‘Red' and ‘Blue') is engaged in a complex cat-and-mouse game of adaptation and counter-adaptation, and where agility and secrecy (e.g. of Red) can enhance the ability to launch attacks8,9,20,21,22,23 (e.g. against Blue). While ‘big data' approaches to non-confrontational human activities have revealed new patterns26,27,28,29,30,31,32,33, the presence of aggression and danger means that event records for a particular confrontation run the risk of being incomplete or biased15. These considerations motivate us to analyze a broad spectrum of heterogeneous event-level datasets drawn from independent sources across multiple disciplines, not limited to armed conflict16,17,18,19, crossing from local to global geographic scales and in both real and online worlds. Our data sources are listed in the Supplementary Information (SI). We find that in all these systems, the distribution of the severity of events and the trend in the timing of events, are each described by a power-law function of the form “AB−C”.
Results
Each point in Fig. 1 results from the maximum likelihood fitting of the power-law Ms−α to the tail in the distribution of the severity of individual events within a given confrontation, where s is the severity of an individual event which, in the case of violent conflict, is the number killed or injured in an attack. α is the power-law exponent, M is the normalizing factor, and p is the goodness-of-fit16,17,18. Figure 1A inset illustrates this power-law tail distribution, while full details of the statistical fitting procedure are described in the cited references of the Methods section. We can analyze event severities and timings separately since they show no systematic cross-correlation, as illustrated in the SI. Specifically, while the event severity distribution is stationary throughout the confrontation to a good approximation, the timing of individual events is a non-stationary process with periods of initial escalation or de-escalation.
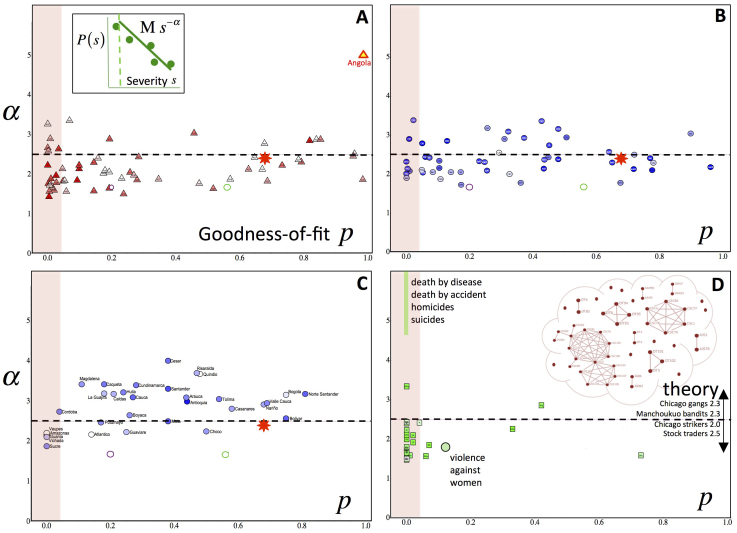
Figure 1. Event-severity benchmark across geographic scales and domains.
Each data-point shows (p, α) values for event severity distribution Ms−α (Fig. 1A inset) for confrontations. (A) within a given continent (Africa); (B) across the globe, for different actors and different injury levels; (C) within a given country (departments in Colombia). (D) shows conventional wars and sexual violence against women5. Suicides etc. form a near continuum at p = 0 with α ≫ 2.5. The darker the color of each data-point, the larger the total number of victims (see SI). Red star shows value for global terrorism17, green ring is value for entire Africa database, purple ring is value for all interstate wars from 1860–1980. Dashed horizontal line shows theoretical benchmark α = 2.5 derived from the simple version of our theory, as described in the text; SI shows α = 2.5 result is robust to generalizations. Red shaded area corresponds to goodness-of-fit p < 0.05. Inset in Fig. 1D shows empirically determined Red operational network for PIRA in South Armagh20. Fig. 1D lists other empirically determined α values. Domains are omitted in Figs. 1,2,3 if we lacked the necessary data (see SI).
Our results for the timing of individual events are summarized by Figs. 2 and 3, where each point results from the maximum-likelihood fit of a power-law τ1n−β to the trend in successive inter-event time intervals τn between the n'th and the (n + 1)'th event within a given confrontation, with n = 1, 2, 3 etc. and with τ1 being the intercept on a log-log plot of τn vs. n19. This procedure is illustrated in Fig. 3 upper inset. The residuals in each least-square fit are approximately Gaussian-distributed and i.i.d., as required for the maximum likelihood best-fit (see SI). The event timing results in Figs. 2 and 3 mostly show escalation (β > 0) with some de-escalation (β < 0). We do not address how, why or when each confrontation ends (or begins) but instead focus on the non-stationary behavior leading up to this endgame.
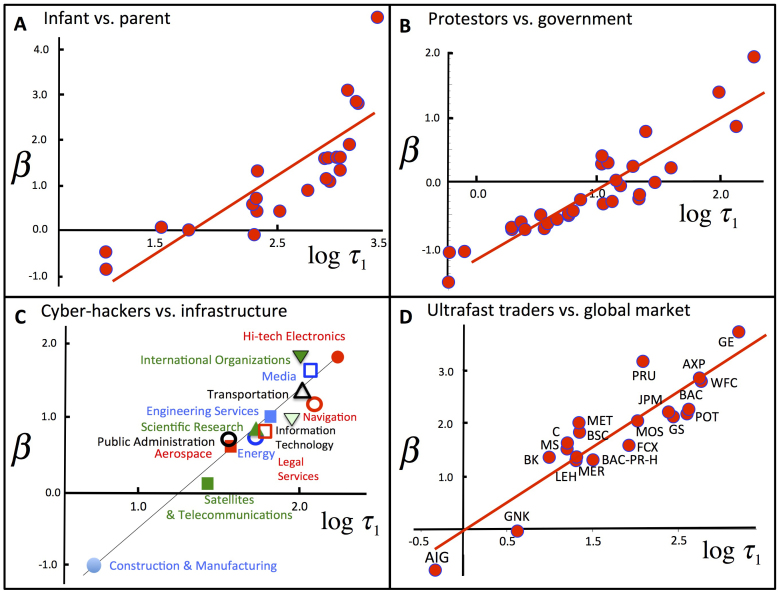
Figure 2. Event-timing benchmark across domains.
(A) Each point denotes a unique infant-parent pair, obtained using analysis in Fig. 3 upper inset. Underlying events are cry-face attacks by infant (Red) against parent (Blue). The experiment is described in Ref. 4. (B) Each point denotes a unique geographic location. Underlying events are street protests by anti-government groups (Red) against Polish government (Blue). (C) Each point denotes a unique sector of national cyber-infrastructure. Underlying events are cyber-attacks by foreign group (Red) against indicated sector's defenses (Blue). (D) Each point denotes a particular U.S. financial institution stock. Underlying events are attacks by ultrafast predatory traders (Red) against the remaining market of slower global investors (Blue). We can reject the null hypothesis that these linear fits emerge by chance, by randomizing event times and then comparing probability distribution of R2 fits to the real value  in order to generate p significance values (Fig. 2A,
in order to generate p significance values (Fig. 2A, 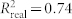 , p = 0.0089; Fig. 2B,
, p = 0.0089; Fig. 2B, 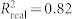 , p = 5.6 × 10−5; Fig. 2C,
, p = 5.6 × 10−5; Fig. 2C, 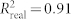 , p = 0.036; Fig. 2D,
, p = 0.036; Fig. 2D, 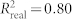 , p = 0.0087). See SI for more details.
, p = 0.0087). See SI for more details.
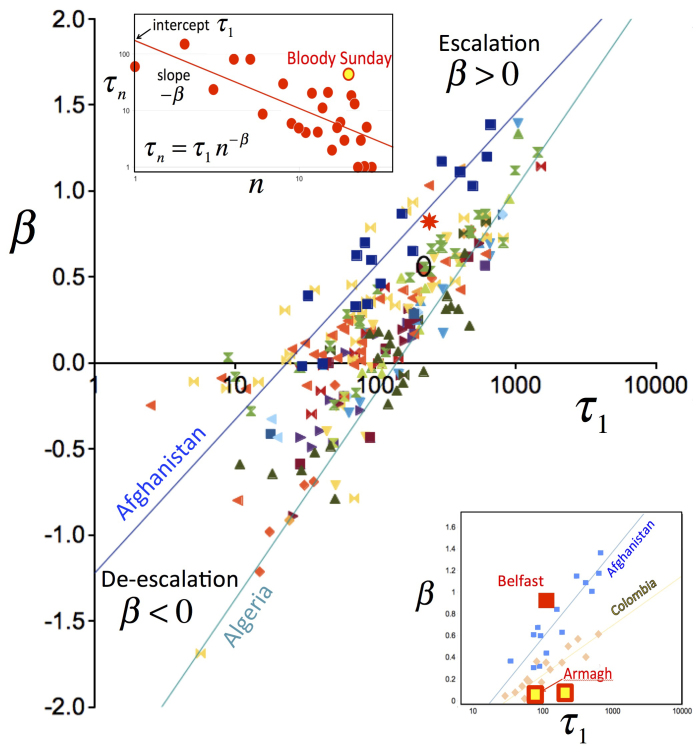
Figure 3. Event-timing benchmark focusing on violent confrontations.
For a given symbol, each data-point shows the (τ1, β) values obtained from fitting trend in inter-event times (upper inset) within a confrontation in a unique region or city within a given country, mostly in Africa but also including Middle East and South America. SI contains key to symbols. Several best-fit lines are shown as a guide. Separate symbols for attacks against government forces, and against civilians. Red star shows result for global terrorism. Upper inset shows escalation of Red attacks in Belfast. Lower inset shows Belfast (solid red square) is abnormal compared to Armagh and Down (red squares with yellow centers).
For the analysis of event severities in Figs. 1A–1C, the α exponent values for the power-law severity distribution are broadly bunched around 2.5 with statistically significant goodness-of-fit, i.e. p > 0.05. (See the cited references in Methods for details on how to determine and interpret these p values). For the analysis of the trend in the timing of events (Figs. 2–3) the β parameter governing the trend from the outset of the confrontation, shows an approximate linear dependence on logτ1, implying that within each domain the confrontations in which initial events are frequent tend to slow down over time (β negative when τ1 is small) whereas they accelerate if events started slowly (β large positive when τ1 is large). In Fig. 2A for infant attacks, this is particularly remarkable since each point corresponds to a different infant (and parent), and the experiment underlying each point is performed at separate times. A random process in which individuals become victims independently with a constant probability, would have yielded p = 0 with an arbitrary α value in Fig. 1, thereby explaining the values in Fig. 1D for suicides, homicides, and death by accident and disease, while for timings the β values would have been evenly scattered around β = 0 with no strong linear dependence. (See SI for empirical confirmation of these statements). Our results benefit from out-of-sample testing: Ref. 34 provides a public, time-stamped record of our 2005 pilot study of two wars that hinted at a severity distribution Ms−α with α ≈ 2.5, while Ref. 16 adds seven more and terrorism. Likewise Ref. 19 records our 2011 pilot study of two wars suggesting τ1n−β for event timings with β linearly dependent on log τ1. Here we move beyond wars and terrorism with Figs. 1,2,3 providing blind test results for every dataset made available to us in the interim years.
Discussion
The confrontations that follow the benchmark behavior generally feature an actor (Red, e.g. cyber-hackers, insurgents, terrorists, protestors, ultrafast traders, infant) who is in principle weaker than its Blue opposition (respectively, the national infrastructure, incumbent army, security forces, ruling government, global stock holders, parent), yet who manages to inflict a series of attacks that typically escalates (β > 0 in Figs. 2–3). We develop our explanatory model by referring to the most recent and detailed fieldwork available of such a Red group20: PIRA (the Provisional IRA) who inflicted an escalating number of attacks against the stronger British government forces (Blue) in Northern Ireland from 1969 onwards20. PIRA's operational network shown in Fig. 1D inset, has a decentralized structure consistent with jihadist operational networks9,21,23 and with other clandestine and illicit groups, e.g. online gold farmers35. Its resources – which in Fig. 1D inset are people but for more general Red may include technology, predatory algorithms (Figs. 2C–D) or even abstract cognitive processes for the case of infant (Fig. 2A)3,4 – are partitioned into clusters (‘cells' or ‘units') where a cluster's components do not have to be spatially close, just coordinated in some way (e.g. by phone). In short, network connections indicate empirical evidence of some coordinated activity, not spatial proximity.
Clusters can begin to coordinate together over time (i.e. clusters coalesce)9,20,21,22,29 but can also lose internal coordination (cluster fragments) under conditions of external or internal stress9,20,21,22,29, just as a cluster of animals disperses if in danger or a start-up company dissolves if it loses common purpose36. Adding the empirical finding that larger social clusters show more churn than smaller ones29, yields the simplest form of our dynamical cluster theory whose exact solution (see SI) is a Red cluster-size distribution of the form Ms−α with α = 2.5, consistent with Fig. 1D inset, with gang sizes in Asia and Chicago (α = 2.3)12 and with cyber-crowds of traders through the proxy of trade size (α = 2.5)31. Following recent empirical findings linking size to lethality14,18, we take a cluster's size as proportional to the severity of an event in which it participates, hence reproducing the severity distribution Ms−α with α = 2.5. We explored many generalizations of this theory but find that Ms−α with α ≈ 2.5 is remarkably robust (see SI). Changing the rigidity of larger Red clusters successively from more rigid to less rigid, moves the α values from below 2 to above 3, hence providing an interpretation for individual confrontations in Figs. 1A–C. Restricting connectivity between Red clusters to physical contact on a two-dimensional grid like an urban street setting or battlefield, pushes α toward 1.9 with a weaker power-law (p → 0) hence explaining most of the conventional wars in Fig. 1D and the α = 2.0 value for Chicago strikes10.
The notion that Red's self-organized, decentralized cluster structure (Fig. 1D inset) helps it adapt faster and/or better than Blue, is consistent with recent findings that organic structures are more conducive to innovation than bureaucratic ones36. Indeed, ultrafast traders (Red, Fig. 2D) carry out their attacks in under a second. We introduce x(n) to represent Red's relative advantage over Blue following the last (n'th) attack, where x(n) follows a general stochastic process. For simplicity, we set the instantaneous rate of Red attacks as proportional to x(n) when x(n) > 0 (i.e. when Red has a relative advantage) and zero when x(n) < 0 (i.e. when Blue has a relative advantage) though this can be generalized. The rate of Red attacks in a confrontation that is generally escalating, then scales as x(n)|rms ∝ nβ′ (see SI) where β′ characterizes the correlations in x(n) (β′ = 0.5 for an uncorrelated process). The time between attacks, which is approximately the inverse rate, is therefore proportional to n−β′ enabling us to identify β′ = β. This explains why τ1n−β describes the attack timings and implies that if β > 0.5, Red's lead over Blue follows a positively correlated process, while it follows a negatively correlated one if 0 < β < 0.5. Confrontations that de-escalate (i.e. β < 0) can be treated similarly. Our theory then reproduces the linear dependence between β and log τ1 if we introduce coupling between the underlying x(n) processes. Such coupling could arise if the same Red entity underlies attacks in different places, e.g. in Fig. 2B the same social movement underlies protests in different locations.
Figures 1,2,3 reveal surprising dynamical equivalences between confrontations and hence offer novel data proxies and cross-domain insights: The escalation of events in Magdalena, Colombia (black oval ring) is representative of all confrontations in Fig. 3; the relative position of General Electric (GE) in Fig. 2D makes predatory trade attacks on it akin to cyber-attacks on the Hi-tech Electronics sector (Fig. 2C) which in turn mimic specific infant-parent dyads (Fig. 2A) and protest locations (Fig. 2B); and the conflict in Sierra Leone, Africa, has the same (p, α) in Fig. 1 as the narco-guerilla war in Antioquia, Colombia. Deviations from the benchmark behavior act as a novel alert mechanism for abnormalities in Red and/or Blue behavior, e.g. Angola in Fig. 1A, which serves to warn researchers against using such a confrontation as representative. The time-interval abnormality in Fig. 3 (upper inset) turns out to straddle the ‘Bloody Sunday' attack by Blue on civilians on 30 January 1972, implying that neighboring points offer insight into the build-up to, and consequences of, an extreme Blue intervention. Interestingly Bloody Sunday appears as the culmination of escalating PIRA attacks, not their trigger, hence raising new questions about its strategic importance. The fact that Belfast's (τ1, β) values in Fig. 3 (lower inset) destroy any linear dependence, is consistent with the recent fieldwork finding20 that Belfast's PIRA network is quite distinct to Fig. 1D inset. The fact that sexual attacks against women do not appear as an outlier in Fig. 1, hints at some hidden clustering (like Fig. 1D inset) of attackers or attacks.
We have shown that both the severities and the timings of events in a wide range of systems, follow a power-law functional form. There are various practical prediction tools and policies that follow from our work, as we now discuss. Suppose some sporadic attacks have been observed in a given location or sector in the real or online world. If the trend in successive time-intervals between attacks is found to follow τ1n−β, this suggests a single Red-Blue process (x(n)) underlies them. Assuming Red dominates the Red-Blue dynamic x(n) (i.e. Blue has not yet counter-adapted), this points to a single attacking Red individual or group. If attacks then emerge in different locations or sectors, detecting an approximate linear relationship in β vs. log τ1 points to this same Red operating in these different places. Figure 2C hence supports media speculation that current cyber-attacks against different sectors of US infrastructure come from a single Red entity24. Likewise, Fig. 2D suggests that a common set of predatory algorithms and/or trading firms (Red) may underlie recent ‘flash' instabilities in different stocks25. For Fig. 2A, the independence of the participants suggests that this linear pattern is revealing a new innate feature of how infants and parents interact.
Now imagine the scenario in which two attacks occur in a new location that was previously quiet, and that this same Red is suspected. An estimate for β in this new location can be read off from the existing β vs. log τ1 plot by inputting this single inter-event time as an estimate for τ1. Future attack times can then be estimated using τ1n−β (see SI for examples).
Next consider the severities of events as they begin to emerge in a given sector. Suppose a crude Ms−α distribution is found with α ≈ 2.5 and p > 0.05. This points to Red having a similar delocalized cluster structure to our model. Indeed, even without any observed events and hence without any event severities from which to estimate the distribution, the weight of evidence in Fig. 1 suggests that any future confrontation involving a similarly structured Red will produce a severity distribution Ms−α with α ≈ 2.5 and p > 0.05. The expected number of victims in a future attack is therefore approximately [(α − 1)/(α − 2)]smin where smin is the cut-off in the maximum-likelihood fit37. Taking α ≈ 2.5 as in Fig. 1 and smin ≈ 1, this expected number is 3, which happens to coincide with the recent Boston marathon attack. The probability the next attack will be twice as lethal, is (s/smin)1−α ≈ (s/smin)−1.5 with s = 6, giving 0.07 (i.e. 7%). The severity of the most fatal attack will grow as the number of attacks n grows, following n1/(α−1) ≈ n0.67. Dividing attacks equally into less violent and more violent, the fraction of victims falling in the most violent half is given by 2−(α−2)/(α−1) = 0.8 meaning that a few attacks will produce the majority of the victims. Another relevant consequence of our clustering theory is that the ongoing coalescence-fragmentation process means that a ‘lone wolf' actor is only truly alone for short periods of time, which is again consistent with recent field studies22, and provides an estimate for how long ago contact was made with other Red clusters.
The stability of α in Fig. 1 throughout a given confrontation (see SI) suggests that the corresponding Red group self-organizes rapidly after its inception, as confirmed by our model's dynamics, and hence latent Red groups that have not yet launched any attacks may already have a structure resembling Fig. 1D inset. More generally, although the overall command structure of a present or future Red might be hierarchical, or publicly portrayed as so, our theory aligns with recent empirical findings9,20,21,23 in predicting that operationally Red will self-organize into a far flatter, clustered structure similar to Fig. 1D inset. As a corollary, our clustering theory also identifies a novel ‘Achilles Heel' for such a Red: The self-organized nature of the clustering means that Blue can avoid having to find and destroy the largest (i.e. most lethal) Red clusters, by instead regularly breaking up smaller (i.e. less powerful) ones. The mathematics specifies conditions required to keep formation of large (lethal) clusters below a desired rate, and so reduce the threat level of large future attacks. It also warns that if Blue is insufficiently active in counter-measures, and hence the overall rate at which it fragments Red clusters becomes too small (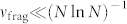 where N is an estimate of Red's size38) then Red will grow exponentially fast into one super-cluster of maximum possible lethality. Finally, our clustering theory predicts a necessary condition39
νfragp/νcoalq > 1 that must be met before a covert message or doctrine can spread within Red, where νcoal is the cluster coalescence rate, p is the transmission rate of the message between two people in a Red cluster, and q is the rate at which this message gets forgotten or corrupted.
where N is an estimate of Red's size38) then Red will grow exponentially fast into one super-cluster of maximum possible lethality. Finally, our clustering theory predicts a necessary condition39
νfragp/νcoalq > 1 that must be met before a covert message or doctrine can spread within Red, where νcoal is the cluster coalescence rate, p is the transmission rate of the message between two people in a Red cluster, and q is the rate at which this message gets forgotten or corrupted.
Methods
The power-law analysis that we use to obtain our results in Fig. 1 for the tail in the distribution of the severity of individual events, follows exactly the state-of-the-art testing procedure described in Refs. 16,17,18 and firmly established in Ref. 40. Our analysis of the trend in the timings of individual events follows exactly the method presented in Ref. 19. Our proposed model of cluster coalescence-fragmentation for Red, which reproduces the 2.5 power-law result for the severity distribution, comprises a population of objects (agents) that self-organize into clusters according to the stated rules of cluster coalescence and fragmentation. The mathematical derivation of the 2.5 result is given in the SI. We have also investigated many variants of this coalescence-fragmentation cluster model and found (see SI) that most retain a power-law with exponent near 2.5. For the trend in the timings of attacks, a null model comparison showing the statistical significance of our benchmark result is given in the SI, together with the derivation of our stochastic model for Red's relative advantage over Blue which reproduces this timings benchmark.
Author Contributions
N.F.J., P.M., G.Z., D.S.M., J.H., P.G., J.C.B., W.M., D.G., H.Q., P.M., N.V., A.M., E.R., N.J., M.S., R.Z. worked on the data and data analysis, and were involved in discussions concerning the model. N.F.J. wrote the paper but all authors participated in associated discussions.
Supplementary Material
Supplementary Information
Acknowledgments
N.F.J. acknowledges support from the Office of Naval Research (ONR) under grant N000141110451 and from the Intelligence Advanced Research Projects Activity (IARPA) via Department of Interior National Business Center (DoI/NBC) contract number D12PC00285. The U.S. Government is authorized to reproduce and distribute reprints for Governmental purposes notwithstanding any copyright annotation thereon. The views and conclusions contained herein are those of the authors and should not be interpreted as necessarily representing the official policies or endorsements, either expressed or implied, of ONR, IARPA, DoI/NBE or the U.S. Government. P.M. (Medina) and J.C.B. acknowledge support from COLCIENCIAS through their doctoral funding program. DSM acknowledges support from the National Institute of General Medical Sciences (1R01GM105004), the National Institute of Child Health and Human Development (R01 HD047417) and the National Science Foundation (1052736). NFJ thanks O. Antony for help with compiling the SOM data files.
References
- Lazer D. et al. Computational Social Science. Science 323, 721–723 (2009). [DOI] [PMC free article] [PubMed] [Google Scholar]
- Vespignani A. Predicting the behavior of techno-social systems. Science 325, 425–428 (2009). [DOI] [PubMed] [Google Scholar]
- Cohn J. F. & Tronick E. Z. Mother–infant face-to-face interaction: Influence is bidirectional and unrelated to periodic cycles in either partner's behavior. Dev. Psychol. 24, 386–392 (1988). [Google Scholar]
- Ekas N., Haltigan J. D. & Messinger D. S. The Dynamic Still-Face Effect: Do Infants Decrease Bidding Over Time When Parents are Not Responsive? Dev. Psychol. 49, 1027–35 (2013). [DOI] [PMC free article] [PubMed] [Google Scholar]
- Kappler K. E. & Kaltenbrunner A. The Power Laws of Violence against Women: Rescaling Research and Policies. PLoS ONE 7, e40289 (2012). [DOI] [PMC free article] [PubMed] [Google Scholar]
- Spirling A. Scale invariance in political science: http://www.people.fas.harvard.edu/~spirling/documents/powerlawSend.pdf (Date of access: 03-24-2013).
- Lichbach M. I. Nobody cites nobody else: mathematical models of domestic political conflict. Defence Econ. 3, 341–357 (1992). [Google Scholar]
- Francisco R. A. Dynamics of Conflict (Springer, New York., 2009). [Google Scholar]
- Kenney M. From Pablo to Osama: Trafficking and Terrorist Networks, Government Bureaucracies, and Competitive Adaptation (University of Pennsylvania Press, Philadelphia, 2007). [Google Scholar]
- Biggs M. Strikes as forest fires: Chicago and Paris in the late nineteenth century. Am. J. of Sociol., 110, 1684–1714 (2005). [Google Scholar]
- Spagat M., Mack A., Cooper T. & Kreutz J. Estimating War Deaths: An Area of Contestation. J. Confl. Resolut. 53, 934–950 (2009). [Google Scholar]
- Richardson L. F. Statistics of Deadly Quarrels (Boxwood Press, London, 1960). [Google Scholar]
- Riddihough G. et al. Human conflict. Science 336, 819 (2012). [DOI] [PubMed] [Google Scholar]
- Asal V. & Rethemeyer R. K. The nature of the beast: Organizational structures and the lethality of terrorist attacks. J. Polit. 70, 437–449 (2008). [Google Scholar]
- Johnson N. F. et al. Bias in Epidemiological Studies of Conflict Mortality. J. Peace Res. 45, 653–659 (2008). [Google Scholar]
- Bohorquez J. C. et al. Common ecology quantifies human insurgency. Nature 462, 911–914 (2009). [DOI] [PubMed] [Google Scholar]
- Clauset A., Young M. & Gleditsch K. S. On the frequency of severe terrorist events. J. Confl. Resolut. 51, 58–87 (2007). [Google Scholar]
- Clauset A. & Gleditsch K. The Developmental Dynamics of Terrorist Organizations. PLoS One 7, e48633 (2012). [DOI] [PMC free article] [PubMed] [Google Scholar]
- Johnson N. F. et al. Pattern in escalations in insurgent and terrorist activity. Science 333, 81–84 (2011). [DOI] [PubMed] [Google Scholar]
- Horgan J. et al. From Bomb to Bomb-maker: A Social Network Analysis of the Socio-Psychological and Cultural Dynamics of the IED Process - Final Report. Arlington, Virginia: Office of Naval Research Code 30. Available at http://www.icst.psu.edu/ResearchProject/B2B.shtml (Date of access: 03-24-2013). [Google Scholar]
- Kilcullen D. The Accidental Guerrilla: Fighting Small Wars in the Midst of a Big One. (Oxford University Press, London, 2009). [Google Scholar]
- Gill P., Horgan J. & Deckert P. Tracing the motivations and antecedent behaviors of lone-actor terrorism: http://www.icst.psu.edu/docs/3.ExecSum/ICST.LoneActor.ExecSumm.pdf (Date of access: 07-25-2013). [DOI] [PMC free article] [PubMed]
- Kenney M. et al. Organisational adaptation in an activist network: Social networks, leadership, and change in al-Muhajiroun. Appl. Ergon. 44, 739e747 (2013). [DOI] [PubMed] [Google Scholar]
- Exposing One of China's Cyber Espionage Units, Mandiant (2013). Available at http://intelreport.mandiant.com/Mandiant_APT1_Report.pdf (Date of access: 3-19-2013).
- Beddington J. Foresight: The Future of Computer Trading in Financial Markets (2012) Final Project Report. The Government Office for Science, London: http://www.bis.gov.uk/foresight/our-work/projects/published-projects/computer-trading (Date of access: 07-24-2013).
- Song C., Qu Z., Blumm N. & Barabasi A. L. Limits of Predictability in Human Mobility. Science 327, 1018–1021 (2010). [DOI] [PubMed] [Google Scholar]
- Wuchty S., Jones B. F. & Uzzi B. The increasing dominance of teams in production of knowledge. Science 18, 1036–9 (2007). [DOI] [PubMed] [Google Scholar]
- Gonzalez M. C., Hidalgo C. A. & Barabasi A. L. Understanding individual human mobility patterns. Nature 453, 779–782 (2008). [DOI] [PubMed] [Google Scholar]
- Palla G., Barabasi A. L. & Vicsek T. Quantifying social group evolution. Nature 446, 664–667 (2007). [DOI] [PubMed] [Google Scholar]
- Preis T., Schneider J. J. & Stanley H. E. Switching processes in financial markets. Proc. Natl. Acad. Sci. U.S.A. 108, 7674–7678 (2011). [DOI] [PMC free article] [PubMed] [Google Scholar]
- Gabaix X., Gopikrishnan P., Plerou V. & Stanley H. E. Institutional investors and stock market volatility. Quart. J. Econ. 461, 461–504 (2006). [Google Scholar]
- Malmgren R. D., Stouffer D. B., Campanharo A. S. & Amaral L. A. On universality in human correspondence activity. Science 325, 1696–700 (2009). [DOI] [PubMed] [Google Scholar]
- Axtell R. What Economic Agents do: How Cognition and Interaction Lead to Emergence and Complexity. Rev. Austr. Econ. 20, 105–122 (2007). [Google Scholar]
- Johnson N. F. et al. From old wars to new wars and global terrorism. arxiv.org/abs/physics/0506213. (2005).
- Keegan B. et al. Dark Gold: Statistical Properties of Clandestine Networks in Massively Multiplayer Online Games. Proc. 2nd Int. Conf. on Social Computing, IEEE Computer Society, (2010). ISBN 978-0-7695-4211-9. p. 201–208.
- Fleming L. et al. The Emergence of Organizations and Markets (Princeton University Press, Princeton, 2012). [Google Scholar]
- Newman M. E. J. Power laws, Pareto distributions and Zipf's law. Contemp. Phys. 46, 323–351 (2005). [Google Scholar]
- Xie Y. et al. Finite-size effect in the Eguiluz and Zimmermann model of herd formation and information transmission. Phys. Rev. E 65, 046130 (2002). [DOI] [PubMed] [Google Scholar]
- Zhao Z. et al. Effect of social group dynamics on contagion. Phys. Rev. E 81, 056107 (2010). [DOI] [PubMed] [Google Scholar]
- Clauset A., Shalizi C. & Newman M. Power-Law Distributions in Empirical Data. SIAM Rev. 51, 661–703 (2009). [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
Supplementary Information