Abstract
Wearable tech is leading way to embedded tech, i.e., implants inside the body designed to track and enhance human health and productivity among other things. Researchers have used Technology Acceptance Model (TAM) extensively to explain the factors influencing adoption of almost all technological innovations to date. Embedded tech, often referred to as biohacking, presents a unique set of factors that call for yet another revision of the model. Using diffusion of innovations, self-efficacy, and social exchange theory, a revision to the technology acceptance model is proposed with additional factors such as age and gender, embedded technology self-efficacy, perceived risk and privacy concerns to explain the adoption of embedded technologies within the human body. Data was collected through an online survey (N = 1063) using a Qualtrics panel and results suggest that age, gender, perceived usefulness, perceived ease of use, embedded technology self-efficacy, risk and privacy concerns all impact the adoption of embedded tech. Implications for the implant industry, policy makers, and researchers interested in such tech are drawn.
Keywords: Biomedia, Biohacking, TAM, Embedded tech, Information science, Information systems management, Information technology, Mass media, Information management, Technology adoption
Biomedia; Biohacking; TAM; Embedded tech; Information science; Information systems management; Information technology; Mass media; Information management; Technology adoption
1. Introduction
The oldest wearable tech is the watch, which was worn by human beings to tell time. Modern wearable tech includes smartwatches, fitness-tracking bands like Fitbit, Runtastic etc., smart glasses like google glass, and head-mounted displays. Embeddable implants are the next logical evolution of wearable tech. Embedded technology within the human body, also called biohacking i.e., biology + hacking, refers to all kinds of implants in and interventions to the human body to enhance performance and health (Norton, 2016). While it might sound like science fiction or an episode of the popular Netflix show Black Mirror, there are several embedded technologies (or biohacks) currently being developed or are already available in the market—electronic tattoos or biostamps, password pills, memory chips, magnetic implants, and guiding/GPS systems embedded in the human body are some of the examples (Monks, 2014). Humans now have the means to manage our biology using medical, nutritional, physical and electronic techniques. The idea behind biohacking is that what we put into our bodies has a big impact on how we feel so if we want better “outputs” from our bodies (like reduced stress, better memory and focus, superior performance and productivity), we need to alter and provide better “inputs” to our bodies (Illulife, 2016).
Many see biohacking as a natural progression and extension of modern innovations like wearable technologies. Wearable tech is typically used to keep track of health and fitness among other things, a phenomenon commonly referred to as Quantified Self (Wolf, 2009). In addition, most wearables have a display that advertisers can use to target users with ads. However, the real value of wearables to companies that create such tech is the availability of abundant personal data that enables advertisers to customize messages and target users with exactly what they need and when they need it (Saxena, 2016). As wearable tech becomes increasingly popular and morphs to embedded tech, the nature and complexity of the information and data now available to implant manufacturers makes a much more sophisticated, personalized, and contextualized advertising possible leading to increased risk and privacy concerns among users. For example, wearable tech Fitbit is leading the way to biostamp, a thinner electronic mesh that stretches and moves with the skin and monitors several important body functions as temperature, hydration and stress (Adrian, 2016). Also referred to as electronic tattoos, biostamps can be used to monitor individuals wirelessly, collect information from their skin in a continuous fashion as they go about their daily lives. This information could be automatically sent to their smartphone or the cloud in a similar way the Fitbit does (Adrian, 2016). This takes the Quantified Self Movement to an entirely new level and creates all sorts of concerns for potential users. Tech manufacturers can use such highly personalized data to send contextual promotional messages to users. For instance, a message to hydrate with a specific drink after a 6-mile run can be send to the user's phone as a push notification along with his or her stats on body temperature and hydration status.
Embedded technologies are not some dystopian future but are, in fact, already part of our current lives with our increased reliance on contact lens, hearing aids, smartphones, pacemakers, bionic knees and other embedded implants (Ricker, 2016). Technology already exists to implant RFID chips in individuals that can serve as entry keys to apartments, tap and go payment systems, public transportation cards, and cards that carry medical and personal info like passwords, blood type, allergy and DNR info. In fact, Three Square Market is the first American company to implant their employees with microchips that let them enter the building, log into their computers and even buy snacks, all with a wave of their hands (Francis and Jarvis, 2017). The list of innovations in this area is endless with bionic eyes, which are telescopic lens with capability to zoom in and out with blinks and night vision capability (Engelking, 2015), brain control interfaces (BCI) to control drones and tweet using EEG (Szondy, 2013), designer babies with gene editing and 3D printed organ transplants (Murgia, 2016).
As biohacking and embedded technologies become more easily accessible, it is important to understand the factors that influence their adoption by average consumers. While researchers have studied the adoption of wearable technologies such as the smartwatch (Chuah et al., 2016), embedded technologies present a unique set of factors like a greater level of risk to the users and increased privacy concerns among other things that warrants a separate examination of the factors of their adoption despite being similar to wearable tech. In addition, Technology Acceptance Model (TAM), which is most commonly used to explain the adoption of new technologies can also be extended/modified to include the unique set of factors that come with embedded implant technologies within the human body. In the following section, using the framework of diffusion of innovations, self-efficacy, social exchange theory, and the theory of planned behavior, a revised technology acceptance model for the adoption of embedded technologies within the human body is proposed.
2. Literature review
2.1. Embedded implants as emerging tech
Before reviewing the literature on the various factors that influence the adoption of new technologies in general, we need to examine the various ways in which embedded implants are similar to and different from existing technologies, particularly wearable tech. Embedded implants are similar to wearable tech in that they are both designed to facilitate real-time tracking of individual functions in the areas of fitness and health. In that sense, some of the factors that influence the adoption of wearable tech as identified in Chuah et al. (2016), perceived ease of use and perceived use, should also influence the adoption of embedded tech. The visibility factor that was found to be significant in predicting the adopting of wearable tech (Chuah et al., 2016) should not apply to embedded tech as by definition most or all embedded tech are implants inside a human body and, therefore, not visible to others. Another difference is that the perceived ease of use can be further investigated in the case of embedded tech as the self-efficacy of using such technologies given that these technologies are new and somewhat more complex to use than mobile phones or smartwatches. Next, although not examined by Chuah et al. (2016) in their study of wearable tech adoption, age and gender, might also play a prominent role in the adoption of wearable tech as young men are predominantly more likely to be early adopters of technology than other demographics (Bagozzi et al., 1989; Czaja et al., 2006). These individual-level differences can be expected to be more prominent in the adoption of embedded tech.
Embedded tech is also different from wearable tech in that there is a certain amount of risk associated with the adoption and use of implants. Unlike wearables, embedded tech involves a deeper interaction with the human body be it through surgery or through implants such as RFID chips underneath the skin. The risk factor is far greater in embedded tech than in previous iterations of technology, which differentiates the adoption process of embedded tech from other technologies such as wearable tech and smartphones. Second, embedded tech has the capability and potential to collect more personal biodata than wearable tech making privacy concerns more critical. For instance, an individual can choose to remove a smartwatch at any point but once an embedded implant is placed inside a human body, the ability to temporarily leave it at home so one's location is not tracked is difficult, if not impossible.
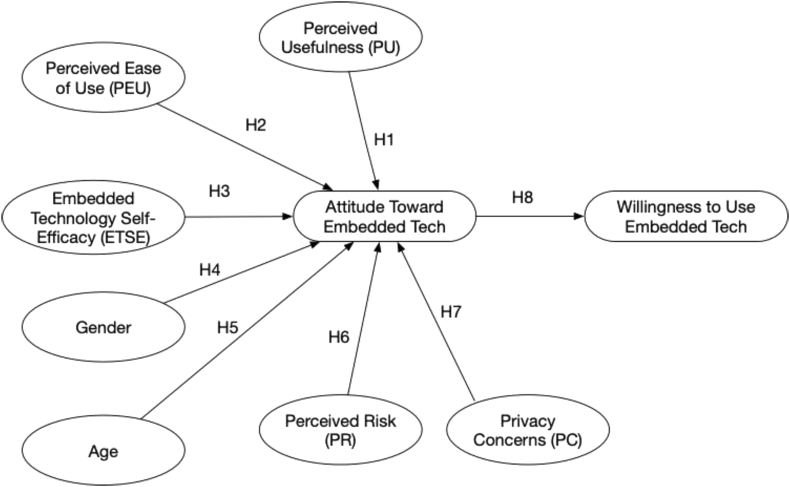
Given these similarities and differences that embedded tech present from other past technologies, a simple application of TAM might not fully explain their adoption as it might for mobile phones or smartwatches. To better understand the factors that influence the adoption of embedded tech, we need to examine a group of communication and social psychology theories to propose and test a revised technology acceptance model. In the following section, we review a set of such theories that take into consideration the four chief ways in which embedded tech are different, i.e., (1) individual-level differences in terms of age and gender, (2) the role of risk involved, (3) the role of embedded tech self-efficacy, and (4) the privacy concerns that are associated with always-on always-collecting-data aspects of embedded tech. Taken together, these set of theories provide the theoretical framework to propose a modified TAM for the adoption of embedded technologies as depicted in Figure 1.
Figure 1.
Proposed model for adoption of embedded tech.
2.2. Factors driving adoption and use of embedded technologies
One of the most widely applied and cited theory of technology adoption is the Technology Acceptance Model (TAM). Technology Acceptance Model (TAM) posits that people use technology if it is easy to use and it offers many benefits (Davis, 1989; Davis et al., 1989). These two factors, perceived ease of use (PEU) and perceived usefulness (PU) explain why we adopt different types of technologies, like Information Systems, to improve our quality of life (Legris et al., 2003). King and He (2006) in meta-analysis of 88 published studies of TAM as applied in various fields found the model to be a robust and valid one with potential for wider applicability. Although the model has been extensively modified and extended to include a number of additional factors, some of which will be reviewed and added to our own model in the following sections, the two factors from the original model—PEU and PU—remain to date one of the strongest predictors of most technologies in use today.
In the case of embedded technologies, too, these two factors can be expected to play a significant role. For an individual to get embedded implants, he or she would need to (a) see some usefulness in such implants and (b) be very comfortable using or operating such technology. As remarked in the introduction, embedded tech can be used to closely monitor several bodily functions (diet, sleep and exercise) to enhance performance and productivity. Unlike technologies that people need to spend copious amount of time learning how to use (e.g. learning how to code in a new language), embedded technologies while complex might not involve a large time investment. And the perceived usefulness in terms of increased productivity, efficiency, and quality of life should also increase their adoption rates. Consider the case of Utah-based salesman, Rich Lee, who got sound transmitting magnets implanted into his ears because he wanted to be able to develop echolocation to support his failing eyesight (Arthur, 2013). After losing considerable amount of vision in his right eye, his doctors told him there was a possibility of something similar happening to his left eye as well, eventually making him legally blind. Rich took the decision to get the magnets implanted into his ears hoping to connect them later to an ultrasonic rangefinder which will allow him to echolocate and be able to survive in case he loses vision completely. This illustrates a case with a high level of perceived usefulness and a relatively high ease of use, both of which have probably increased the adoption of such implants within the human body.
Over the past few decades, creators of embedded technologies have focused a lot of their attention on not only designing new and interesting tools, but also on making these tools more acceptable, user-friendly and easy to use, which should increase their rate of adoption with more people open to experimenting with such technologies. For instance, when a company recently decided to offer microchip implants to their employees, more than 50 percent of employees voluntarily decided to allow their company to embed the FDA-approved microchip implants in their hands. The ability to perform certain routine activities with ease—such as entering company premises, getting food from the company cafeteria and using work computer with the just a wave of their hand—is one of the main reason employees were eager to try these microchip implants (Mohr, 2017). In addition to the potential uses of embedded tech (like improved job performance, efficiency, increased satisfaction and quality of life), today's collaborative, open-source culture is also making it easier for individuals to learn how to use new technologies. For example, DIYbio is a Boston-based network that was created in 2008 with the purpose of offering laymen the chance to dabble in biology (Delfanti, 2012). Their endeavor to provide people with the tools they need to experiment in the field of biology has given rise to ‘garage biologists’ and DIY biohackers who are not only comfortable operating bio implants but are getting those implants themselves (Bloom, 2009).
Based on the above discussion, embedded technologies offer a unique set of useful functions and are designed to be relatively easy to use, both of which should predict their popularity and adoption among users.
H1:
Perceived usefulness of embedded technologies will positively impact individuals' adoption of such technologies.
H2:
Perceived ease of use of embedded technologies will positively impact individuals' adoption of such technologies.
Over the years, TAM has been extended in numerous ways to fit the technology being examined as each new technology presents a disparate set of challenges and opportunities for adoption. Similarly, the role of individual-level factors in technology adoption has also been extensively studied (Agarwal and Prasad, 1999; Burton-Jones and Hubona, 2005; Hong et al., 2002). One such individual-level factor is an individual's level of prior experience with the said technology, often referred to as self-efficacy. While the Perceived Ease of Use (PEU) of a technology relates to the technology itself and its various features that make adoption and use easier or difficult, an individual's own beliefs of how capable they are of using embedded technologies based on their own experiences should also potentially influence their adoption of such technologies. This concept of an “individual's sense of personal [ability] to produce and to regulate events in their lives” is called self-efficacy (Bandura, 1982, p. 122). Self-efficacy, which plays a pivotal role in influencing our approach to different types of tasks, is often associated with the adoption and use of technologies such as computers and the internet (e.g., Eastin and LaRose (2000) internet self-efficacy). It is not just a matter of knowing what to do but rather “it involves a generative capability in which component cognitive, social and behavioral skills must be organized into integrated courses of action to serve innumerable purposes” (Bandura, 1982, p. 122). In other words, it is one's ability or confidence in how well one can execute a certain course of actions required to deal with and/or accomplish certain goals (Bandura, 1982).
Luarn and Lin (2005) investigated the role of perceived self-efficacy on behavioral intention to use mobile banking and found that it had a significant positive impact on behavioral intentions. Sánchez and Hueros (2010) extended TAM to include technical support and perceived self-efficacy and found both to have a positive effect on the use of an online teaching platform called Moodle. Similarly, individuals' adoption and use of embedded technology should be dependent on their perceptions and beliefs of how well they think they are capable of using such technologies to accomplish their objectives associated with them. This is different from the perceived ease of use (PEU) which is based on the technology itself and its features rather than individual's abilities. Drawing from Bandura (1982) general concept of self-efficacy and Eastin and LaRose (2000) extension of it to internet in terms of internet self-efficacy, we used the items in both scales to adapt to embedded technology. We call this the embedded tech self-efficacy (ETSE) and define it as an individual's judgements on his or her ability to execute the functions necessary to operate and deal with embedded technologies to achieve a set of objectives or goals. Based on research on self-efficacy and internet self-efficacy, embedded technology self-efficacy (ETSE) should also have a strong influence on how individuals adopt and use such technologies. Resisting new technologies or experiencing anxiety while using them are traits often displayed by people who question their technical self-efficacy or in other words, their ability to constructively use tech tools to achieve certain goals in their lives. For instance, Iivari (1995) found that people who considered computers to be too complicated rarely felt motivated to learn them, as they assumed that they would not be able to use them well enough to achieve their goals.
Also important is how we understand the concept of ability itself. Some people consider ability to be fluid, dependent on experience and malleable. These people welcome challenges that help them learn and are not afraid to make mistakes. Failure is looked at as a stepping stone to further learning. Others are convinced that ability is inherent and not much can be done to change it. As a result of this belief, they prefer not to engage in activities in which they could potentially perform badly and, consequently, give up on opportunities to learn from their failures (Bandura, 1993). Irrespective of whether abilities are fluid or not, individuals' beliefs in their own abilities to be able to execute and operate embedded implants in their bodies without concern or anxiety should positively impact their ultimate adoption and use of such technologies. Therefore,
H3:
Individuals' level of embedded technology self-efficacy (ETSE) will positively influence their adoption of embedded technologies.
Among the various individual-level factors that are frequently used in the extension of TAM, age and gender feature prominently in several studies (Tarhini et al., 2014; Lu et al., 2003; Wang et al., 2009). In extending the unified theory of acceptance and use of technology (UTAUT) to a consumer context, Venkatesh et al. (2012) hypothesized and found evidence that age, gender, and experience all moderate the effects of constructs such as hedonic motivation, price value and habit on both behavioral intentions and actual use of technology. While several studies using TAM and UTAUT have found evidence for the role and influence of age and gender in technology acceptance, another theory that also supports these individual-level difference in technology acceptance is the diffusion of innovation. Diffusion of Innovation theory developed by E. M. Rogers explains “the process in which an innovation is communicated through certain channels over time among the members of a social system” (Rogers, 2003 p. 5). Rogers (2003) divided people into five adopter categories: innovators, early adopters, early majority, late majority and laggards. Innovators are enterprising, allow themselves to fail and learn from their failure to continue creating new and interesting ideas and products. Early adopters are people who may not create, but they are certainly aware of the advantages of adopting technology before others do. People who fall into the early majority category adopt technologies after observing their pros and cons. Late majority adopt technology long after it has been used by others and laggards are those who don't display much interest in upgrading themselves from a technological point of view (Rogers, 2003).
Within the diffusion of innovations (and technology) certain individual-level differences exist. For example, in their longitudinal study on gender differences in the field of technology adoption, researchers Venkatesh et al. (2003) found that there are different underlying factors that motivate men and women to actually use technology. They found that women place more emphasis on the process followed to achieve a target as compared to men, who focus more on the outcome (Venkatesh et al., 2003). Perceived behavioral control and subjective norm, i.e. societal pressure to or not to display certain behaviors, also played a major role in women's inclination to adopt new technologies. As a result of their outcome-oriented approach and willingness to take risks to achieve their goals (Morrongiello and Rennie, 1998), we find that men tend to be early adopters of technology more so than women. Consistent early exposure to new technologies, in turn, spurs on men's technical prowess, making them more comfortable with technology as compared to women. In his 1995 study on gender differences in self-efficacy and attitudes towards computers, Busch found that males were more likely to get early exposure to computers, computer games and programming as compared to their female counterparts (Busch, 1995).
Research also points to gender differences in risk-taking ability that stems from the way boys and girls are raised to think of failure. Morrongiello and Rennie (1998) note that boys are more inclined than girls to take risks as boys put failure down to bad luck more often, and do not take it personally, as opposed to girls who tend to internalize failures and approach risks more cautiously. Similar research has confirmed that women are inclined to not behave as competitively as their male counterparts and tend to put very little on the line to meet their objectives (Lindquist and Save-Soderbergh, 2011). This serves as a basis to explain why more males tend to venture into and succeed in the area of technology which expects one to assume a certain amount of risk, openness to failure and an ability to learn from it.
Similarly, a person's age has also been said to determine the amount of tech tools he or she uses and how easily they will take to embedded technology in the future. Younger men and women are exposed to the web, internet and computers at an earlier age compared to the older generations. As a result, older and middle-aged adults experience lower levels of comfort and more anxiety when handling technology (Czaja et al., 2006). It has been found that attitude toward tech and adoption behavior are closely tied to how useful learning new technology is perceived to be. Younger employees place much more emphasis on extrinsic rewards such as promotions and bonuses, and because learning new technology is critical in this day and age to advance one's career, they are more likely to have an attitude of wanting to increase their interaction with the technology around them which might help them achieve their job-related goals (Czaja et al., 2006).
Even from TAM and self-efficacy perspective, prior experience with technology enables individuals to develop a more positive or negative attitude and perception of self-efficacy toward technology. Since the younger generation has had more exposure to technology as compared to their older counterparts, adoption of embedded technology in their everyday lives should be higher. As a result, we propose:
H4:
Age will negatively influence individuals' adoption of embedded technologies.
H5:
Gender will predict individuals' adoption of embedded technologies such that males are more likely to adopt such tech than females.
In addition to factors relating to technology itself (PU and PEU) and the individual-level factors (ETSE, Age and Gender), embedded technologies involve at least two other factors that are somewhat more salient to these types of tech than traditional ones like laptop or mobile phone adoption. The risk involved in getting and using embedded technologies within the human body and the potential compromises to individual privacy are much more salient with these technologies than with most technologies to date. Implanting chips into one's body is a risky affair in itself but the dangers of them interacting with human bodies and/or creating future complications is much more critical than the potential harmful radiation a cellphone might generate. The other key aspect of embedded tech is that these implants are not as easy to get rid of as leaving one's cell phone at home. Since they are implants within the human body, it does take a certain level of expertise and risk to remove them. Similarly, the always-on nature of embedded tech also potentially heightens the privacy concerns of individuals carrying these implants.
Despite these negative factors, individuals might still opt to use such technologies and Social Exchange Theory (SET) could be used as a framework to explain why individuals might be willing to take the risk and/or give up their personal data and privacy in exchange for the benefits of technologies. It is widely known that human beings operate within a mutually accepted set of norms to function productively. This forms the basis for SET, which posits that our interactions are based on the understanding that giving something someone wants or needs will get us something that we want or need (Cropanzano and Mitchell, 2005). For instance, in the area of social networking sites, an interesting social exchange has been occurring where people willingly share their personal information and watch ads or sponsored content in return for free access to these platforms. Being a member allows them to maintain relationships with other people or make new connections and for that, they pay with their time and privacy. This sort of exchange is a given and almost the norm as evidenced by the billions of people on Facebook and Twitter. And historically, media have been somewhat free to public because of advertising. With the advent of internet, it could be argued that people are also paying for these services with their personal and private data.
Privacy concerns play an important role in deciding how much personal information people divulge on these sites. In a study conducted to measure the relationship between amount of social interaction on social media sites and level of privacy offered, it was noticed that there was a very strong direct relationship between the magnitude of information people willingly shared and how much they trusted the social media site and its members not to misuse that information (Dwyer et al., 2007). If this reasoning is to be applied to embedded technologies, it goes without saying that companies that offer privacy protection and have stern policies in place that prohibit misuse of users' personal information will draw the largest number of voluntary users who will share their information in exchange for the benefits offered by embedded implants.
While there is no research that directly examines the effects of risk and privacy on embedded tech adoption, researchers have investigated the role of both in other contexts. For example, Pavlou (2003) has studied the impact of both risk and aspects of privacy associated with electronic commerce and its acceptance. Findings strongly support the hypothesis that consumer intentions to transact online are negatively affected by individuals' levels of perceived risk (Pavlou, 2003). In another study, Im et al. (2008) found that perceived risk, technology type, and gender were significant moderating variables in users' technology adoption. The role of perceived risk has been shown to be significant in the adoption of online shopping (Li and Huang, 2009; Wu and Ke, 2015) and in the adoption of internet banking across the globe (Kesharwani and Singh Bisht, 2012; Martins et al., 2014). Similarly, individuals' concern for information privacy directly influences their opt-in intentions of adoption of electronic health records (Angst and Agarwal, 2009). Based on these findings, we hypothesize:
H6:
The level of perceived risk associated with embedded technologies will negatively influence individuals' adoption of such technologies.
H7:
The level of privacy concerns associated with embedded technologies will negatively influence individuals' adoption of such technologies.
Lastly, Ajzen (1988) Theory of Planned Behavior (TPB) has been used to explain intention and behavior in many social circumstances. Allport (1935) suggests that attitude is not an overt behavior but rather a disposition that influences that behavior. TPB establishes a link between attitudes and behavior in that people's mindset (positive or negative) about certain behaviors is an important predictor of how well they will take to those behaviors (in this case adoption of embedded technologies). A person's attitude toward a technology influences the amount they allow themselves to be exposed to it, and the relationship between attitude and behavior is such that attitude toward an action influences a person's intention to perform that action, which in turn influences their actual action or behavior (Ajzen and Fishbein, 1977, 1980). This link has been shown in several studies such as with social media adoption in Gangadharbatla (2008) who provides empirical evidence for attitude toward social networking sites ultimately influencing individuals' willingness to join and use such sites. Therefore, the more favorable the attitude toward embedded tech, the higher the chances that individuals will adopt and play with embedded technologies.
H8:
Individuals' attitudes toward embedded tech will predict their adoption of such technologies
3. Method
In order to test the hypotheses, an online survey was designed, and participants were recruited through Qualtrics. The sample make-up was set up with a rough 50-50 gender split and with age and ethnicity to mirror U.S. national census at the cost of $4 per complete (N = 1167). The survey was also created in Qualtrics with the first page serving as an informed consent form along with a description of the study. Respondents were told that the purpose of the study was to better understand individuals' opinions on specific technologies and that the entire survey should take no more than 10-15 min. They were also informed that their participation is voluntary, and that no identifying information was being collected. Participants were sent a link to the survey and upon clicking yes to the informed consent were taken to the first page of actual survey questions. Participants were provided a brief description and definition of embedded technologies with examples (electronic chips, magnets, password pills, electronic tattoos, and other things individuals can implant directly in their bodies to increase productivity and monitor health and nutrition among other things). Following a brief description, respondents were asked to rate their views on such technologies in a series of Likert scale questions. These Likert scale items included items frequently used in TAM scales and additional items that are related to our study that measured the risk and privacy concerns associated with embedded tech such as “Embedded technologies can be useful,” “Embedded technologies can be risky,” “Embedded technologies can be dangerous,” and “People will lose privacy with embedded technologies.” The next set of questions measured respondents' self-efficacy with embedded tech (Embedded Tech Self-efficacy) if they were to implant them in their bodies. These Likert scale items were five statements modified from Eastin and LaRose (2000) Internet self-efficacy scale. Following this, individuals' attitudes toward embedded tech and intentions to use such technologies were measured using time-tested 5-point Likert scales adapted from Bruner et al. (2001) and MacKenzie and Spreng (1992). The survey concluded with questions that gathered the demographic information of the respondents. All scales used were 5-point Likert scales and tested for reliability using Cronbach's alpha.
4. Analysis and results
Starting with the initial set of total completes, several data cleaning methods and techniques were employed to eliminate participants who straight-lined and/or completed the survey in a duration less than one-third the median time it took all respondents to complete the survey. In addition, respondents who provided subpar answers, such as nonsense words in the open entry text question at the end, were also eliminated from the sample. In all, a total of N = 1063 quality completes were obtained after eliminating speeders, straight-liners and other sources of corrupt data.
The breakdown of sample was 523 males (49.2%) and 540 females (50.8%) with 53% identifying as White, 24% African American, 9% Hispanic, 8% Asian, 1% Native American and 5% in the other category. The median age was 43 with a range of 18–86 years and 11% belonging to 18-24, 23% to 25-34, 18% to 35-44, 16% to 45-54, 16% to 55-64 and 16% over 65 years old. This roughly reflects the U.S. census population breakdown by age. Finally, 25% of the sample reported having a 4-year college degree and 66% no college degree. Again, a statistic that roughly represents the national percentages in the United States.
All scales used in the survey were tested for reliability using Cronbach's alpha except PU (Mean = 3.24) and PEU (Mean = 2.96), which were measured as single Likert items. Table 1 below lists the scales means, variance, and reliability measures.
Table 1.
Mean, variance, and Cronbach's alpha coefficients.
| Scale | Mean | Variance | α |
|---|---|---|---|
| Attitude toward Embedded Tech (3 items) | 2.51 | .001 | .88 |
| Willingness to get Embedded Tech/Implants (3 items) | 2.11 | .04 | .75 |
| Embedded Tech Self-Efficacy (4 items) | 2.87 | .004 | .93 |
| Perceived Risk (2 items) | 3.82 | .03 | .80 |
| Privacy Concerns (2 items) | 3.75 | .03 | .79 |
To test hypotheses 1, 2, 3, 5, 6 and 7, two series of linear regressions with individuals' attitudes toward embedded tech and willingness to get embedded implants as the dependent variables and (a) perceived use of embedded tech, (b) perceived ease of use of embedded tech, (c) embedded tech self-efficacy, (d) age, (e) perceived risk, and (f) privacy concerns as the six independent variables was conducted. Hypothesis 4 involved gender predicting adoption and gender being dichotomous was not included in the regression. Individuals' likelihood of adoption was thought to be a product of both their attitudes toward the tech and their behavioral intentions. Hence, two sets of regressions were performed with the same set of predictors. Tables 2 and 3 below summarize the R-square values, collinearity statistics, and coefficient estimates for predictors for both regressions.
Table 2.
Regression analysis.
| Unstandardized Estimates |
Standard Error |
Standardized Estimates |
t | Collinearity Statistics |
||
|---|---|---|---|---|---|---|
| B | SE | ß | Tol | VIF | ||
| Intercept | 1.2 | .14 | .31 | 8.6∗ | ||
| Perceived Usefulness (PU) | .31 | .02 | .09 | 13.1∗ | .77 | 1.2 |
| Perceived Ease of Use (PEU) | .08 | .03 | .09 | 2.9∗ | .40 | 2.4 |
| Embedded Technology Self-Efficacy (ETSE) | .39 | .03 | .38 | 11.2∗ | .38 | 2.6 |
| Age | -.006 | .001 | -.092 | -4.3∗ | .97 | 1.0 |
| Perceived Risk (PR) | -.146 | .033 | -.133 | -4.4∗ | .49 | 2.0 |
| Privacy Concerns (PC) | -.076 | .032 | -.071 | -2.3∗ | .49 | 2.0 |
| R2 | .533 | |||||
| Adjusted R2 | .530 | |||||
∗p < .001.
Notes: Dependent variable is attitude; predictors are Perceived Usefulness (PU), Perceived Ease of Use (PEU), Embedded Technology Self-Efficacy (ETSE), Age, Perceived Risk (PR), and Privacy Concerns (PC).
Table 3.
Regression analysis.
| Unstandardized Estimates |
Standard Error |
Standardized Estimates |
t | Collinearity Statistics |
||
|---|---|---|---|---|---|---|
| B | SE | ß | Tol | VIF | ||
| Intercept | 2.5 | .15 | 16.8∗ | |||
| Perceived Usefulness (PU) | .16 | .02 | .18 | 6.7∗ | .77 | 1.2 |
| Perceived Ease of Use (PEU) | .05 | .03 | .06 | 1.7 | .40 | 2.4 |
| Embedded Technology Self-Efficacy (ETSE) | .26 | .03 | .28 | 7.2∗ | .37 | 2.6 |
| Age | -.008 | .002 | -.13 | -5.3∗ | .97 | 1.0 |
| Perceived Risk (PR) | -.211 | .034 | -.20 | -6.1∗ | .49 | 2.0 |
| Privacy Concerns (PC) | -.188 | .033 | -.19 | -5.6∗ | .49 | 2.0 |
| R2 | .40 | |||||
| Adjusted R2 | .39 | |||||
∗p < .001.
Notes: Dependent variable is willingness to get implants (ET); predictors are Perceived Usefulness (PU), Perceived Ease of Use (PEU), Embedded Technology Self-Efficacy (ETSE), Age, Perceived Risk (PR), and Privacy Concerns (PC).
As can be seen in the tables, all predictors were statistically significant at p < 0.001 level for both dependent variables—attitudes and intentions—except perceived ease of use for one dependent variable, willingness. The model had an R-Square of .53 for attitudes and .40 for intentions, meaning, the model predicted 50% of variance in attitudes and 40% of variance in intentions. Age, perceived risk and privacy concerns all had negative impact on the dependent variables while PU, PEU and ETSE all had positive impact on adoption. Of these, PEU was statistically significant for attitudes but it was approaching significance (p = .08) for willingness to get implants. This could be because of the single-item measures used for both PU and PEU, which is one of the limitations of the current study. However, both PU and PEU are so widely tested and shown to impact technological adoption that we can expect their impact to be similar on the adoption of embedded technologies as well. Age had a negative influence meaning younger respondents were more likely to adopt embedded technologies more so than older respondents. To interpret the unstandardized values; each coefficient represents the amount of change in the attitudes (or intentions) toward embedded tech, given a raw score unit change in predictors. For example, attitude toward embedded tech becomes more favorable by .31 with a unit change in individuals' perceived usefulness of such technologies on a scale of 1–5. Similarly, for age, the attitudes become unfavorable by .006 for every unit change in respondents' ages. In addition, the multicollinearity statistics show that the predictors (independent variables) are not highly correlated with each other. This is indicated by the high tolerance values and low Variance Inflation Factor (VIF) values. Tolerance values less than .20 and VIF greater than 5 are generally considered evidence of multicollinearity.
It can be concluded that individuals' adoption of embedded tech is positively impacted by their perceived usefulness (H1), their perceived ease of use (H2) and their level of embedded technology self-efficacy (H3), and negatively impacted by their age (H5), their level of perceived risk associated with embedded tech (H6) and their level of privacy concern (H7). Therefore, the regression analyses support for all six hypotheses.
Hypothesis 4 predicts that gender will be a significant predictor of adoption of embedded technologies. Gender differences in adoption of embedded tech are expected as previous research shows that men, especially younger men, are more likely to be early adopters of new technologies (Chau and Hui, 1998). So, for H4 to be supported there should be gender differences in both attitudes towards embedded tech and willingness to get implants such that males should have a statistically significant higher mean than females. As a means of explanation for this, as noted in the literature review, there should also be gender differences in perceived usefulness, perceived ease of use of implants, and embedded tech self-efficacy, which in turn theoretically explain why there are gender differences in the adoption. To test this, an independent samples t-test with gender as the grouping variable and the following as test variables: perceived usefulness of implants, perceived ease of use, embedded tech self-efficacy, attitudes toward embedded tech, and willingness to get implants, was conducted. Table 4 below presents the results of the t-test.
Table 4.
T-Test with gender as grouping variable.
| Gender | N | Mean∗ | Std. Deviation | Std. Error Mean | |
|---|---|---|---|---|---|
| Perceived Usefulness of Embedded Tech (PU) | Male | 523 | 3.43 | 1.11 | .04 |
| Female | 540 | 3.08 | 1.19 | .05 | |
| Perceived Ease of Use of embedded tech (PEU) | Male | 523 | 3.11 | 1.22 | .05 |
| Female | 540 | 2.81 | 1.25 | .05 | |
| Embedded Tech Self Efficacy (ETSE) | Male | 523 | 3.05 | 1.06 | .04 |
| Female | 540 | 2.71 | 1.11 | .04 | |
| Attitude toward Embedded Tech | Male | 523 | 2.73 | 1.12 | .04 |
| Female | 540 | 2.37 | 1.12 | .04 | |
| Willingness to get Embedded Tech | Male | 523 | 2.29 | 1.07 | .04 |
| Female | 540 | 2.03 | 1.00 | .04 |
∗All mean differences are significant at p < .001.
All mean differences between males and females were statistically significant at p < 0.001 level. There were significant differences in the reported attitudes toward embedded tech for male (M = 2.69, SD = 1.1) and female (M = 2.33, SD = 1.1) groups; t (1002) = 5.25, p < .001 and in individuals' willingness to get implants for male (M = 2.24, SD = 1.08) and female (M = 1.99, SD = .99) groups; t(1002) = 3.85, p < .001. This provides empirical evidence for gender differences in adoption and, therefore, H4 is supported. Not only does our data support H4 but also provides support for the explanations frequently used in technology acceptance literature. The gender differences in adoption can be explained by gender differences in perceived level of usefulness and ease of use of such technologies, and their level of embedded technology self-efficacy. In all cases, men are more likely to (a) perceive embedded technologies are more usefulness and (b) easier to use and (c) have higher levels of embedded self-efficacy, which all lead to in turn more favorable attitudes toward them and be more willing to try them out. Therefore, H4 is supported.
Hypothesis 8 predicts that individuals' attitudes toward embedded tech will predict their adoption of such technologies as conceptualized by their willingness to get implants. For testing this hypothesis, a linear regression with willingness to use embedded tech as the dependent variable and attitudes toward embedded tech as the independent variable was conducted. A significant regression equation was found (F (1, 1002) = 956.40, p < .001, with an R-square of .488. The unstandardized coefficient for the independent variable (attitude toward embedded tech) was .65 at p < .001. These results indicate that respondents' predicted willingness to try embedded tech or to get implants was equal to .479 (intercept) + .653 ∗ (attitude toward embedded tech) points when both attitudes and intentions were measures on a scale of 1–5. In other words, willingness increased 1.132 for each point increase on attitude scale. Therefore, H8 is supported. Table 5 below summarizes the findings for all eight hypotheses.
Table 5.
Summary of findings.
| Hypotheses | Attitude towards embedded implants | Willingness to get implants |
|---|---|---|
| H1 (PU) | Supported | Supported |
| H2 (PEU) | Supported | Not Supported |
| H3 (ETSE) | Supported | Supported |
| H4 (Gender) | Supported | Supported |
| H5 (Age) | Supported | Supported |
| H6 (Risk) | Supported | Supported |
| H7 (Privacy) | Supported | Supported |
| H8 (attitude-intention) | Supported | |
5. Conclusion
Embedded implants might seem like some distant sci-fi vision of the future, but the reality is that many of them are already available in the market (RFID implants, biostamps etc.). The scenarios depicted in dystopian shows like Netflix's Black Mirror are much closer to reality than we would care to admit. In addition to the various embedded tech examples provided in the introduction—bio stamps, RFID chips in employees, password pills, magnetic implants, bionic eyes, and gene modifications—neuroscientists at MIT recently planted false memories in the brains of mice and demonstrated that the neurological traces of these memories are identical in nature to those of actual/authentic memories (Ramirez et al., 2013). If we are able to successfully alter the memories in mice, one could argue that technologically we are not that far away from the day when human memory can be altered or enhanced through successful implants. Notwithstanding the philosophical, ethical and legal implications, it is fascinating that we as humans are that close to achieving the technical know-how of altering the God-given state and nature of things. For this reason alone, it becomes imperative that we dedicate some energy and time to better understand the factors that will influence the adoption and use of embedded technologies.
The results of our study show that the factors that influence the adoption of embedded technologies include perceived usefulness of such technologies, perceived ease of use, individual's level of embedded technology self-efficacy, gender, age, risk and privacy concerns associated with such technologies. More precisely, the more individuals see the usefulness of these technologies and the more they perceive their ease of use, the more likely they are to adopt and use such tech. In addition, males and younger consumers are more likely to have favorable attitudes toward embedded tech and are more willing to get embedded implants than females and older consumers. Likewise, individuals with high levels of embedded technology self-efficacy are also more likely to adopt these technologies. And lastly, the two hurdles to embedded tech adoption are risk and privacy concerns associated with such technologies, both of which have a negative impact on attitudes and willingness to get implants. In all cases, consumers' favorable attitudes toward embedded tech is positively linked to their likelihood of getting bio implants.
The current study being exploratory in nature has numerous limitations. These include collecting data via an online survey, which could be argued to have skewed the sample towards a more tech-savvy population although the sample very closely represents the makeup of U.S. population in terms of age, gender, income, education and race. Another limitation is the measure of both perceived use (PU) and perceived ease of use (PEU), both of which were featured on the survey as single-item measures. While this somewhat limits the reliability of these measures, both PU and PEU have extensively been linked to technology acceptance so they were not the primary focus of the current study. The study used a measure of behavioral intentions rather than actual adoption and use. Although several studies show that intentions are a very good indicator of actual behavior, they are just indicators rather than the actual behavior itself. Next, the low reliability index for the scale “willingness to get embedded implants” (alpha = .75) might also limit the overall reliability of the study. Lastly, given the exploratory nature of our study, a rather simplified set of statistical methods (i.e., regression analyses and t-tests) were employed in the current study. Given the development in the field of statistical methods since the first introduction of TAM, a more suitable approach would be the use of structural equation modeling (SEM). Despite these limitations, given the new and emerging nature of embedded tech and the lack of research in understanding their adoption, our study serves as a first step toward furthering our knowledge of such technologies. Future studies should employ a more thorough and exhaustive list of antecedents to adoption and employ more sophisticated statistical methods like SEM to investigate both the antecedents and consequences of embedded tech adoption and use.
6. Implications
Our study presents numerous theoretical and practical implications. First, our results provide for yet another way to extend the technology acceptance model. TAM has been revised extensively in the past but the unique set of characteristics of embedded technologies presents yet another opportunity to modify this model. While, admittedly, a minor one, the study's main theoretical contribution comes from such a modification to the original model. More specifically, the addition of perceived risk and privacy concerns to the model takes us closer to an all-encompassing model to explain technology adoption. Taken together, the factors in our model explain 50% of the variance in attitudes and behavioral intentions, i.e., providing almost half of the explanation for why people adopt and use embedded tech. Our study also combines several known and widely applied theories like diffusion of innovations, self-efficacy, theory of planned behavior and social exchange theory to TAM in the context of embedded technologies. Additionally, our study also provides empirical evidence for individual-level differences (age and gender) in these widely cited theories.
From an industry standpoint, embedded tech presents numerous opportunities for advertisers and marketers. First, the vast amount of highly personal data available with such technologies presents advertisers with the opportunity to use “contextual” advertising. Zhang and Katona (2012 p.1) define contextual advertising as “the display of relevant ads based on the content that consumers view, exploiting the potential that consumers' content preferences are indicative of their product preferences.” For example, our finding that younger males are more likely to adopt embedded technologies has interesting implications for advertisers, particularly digital or interactive media planners. Young males also have a high level of embedded tech self-efficacy and are more willing to get embedded implants. Using this finding, brands like Nike could partner with a start-up that manufactures Fitbit like biostamps (FDA approved of course!) that can be embedded in consumers' bodies with every purchase of Nike “SkinFit” shoes for free. Of course, privacy, risk, and ethical issues would be of utmost concern, especially with respect to the highly personalized nature of the data that will be available to both the chip manufacturers and the advertisers that sponsor such tech.
The second set of practical implications of our findings are for embedded implant manufacturers and brands working with such companies. For instance, the key to successful adoption of embedded tech—as is the case with any tech—lies in its ultimate usefulness and ease of use. As manufacturers are able to show end-consumers the various uses and usefulness of embedded tech, the more the chances of individuals agreeing to adopt these technologies. Along the same lines, from a diffusion of innovations perspective, innovators and early adopters of embedded tech tend to be younger folks and males with high levels of self-efficacy. Our study provides empirical evidence for that. So, if chip manufacturers are trying to market to these innovators and early adopters, appealing to younger males with high tech self-efficacy might be the most efficient way to gain the initial momentum. Finally, as manufacturers and brands work toward making embedded implants mainstream, our findings indicate that they should pay special attention to two huge hurdles for adoption—risk and privacy concerns associated with such technologies. As technology improves and it becomes safer to get implants, the dangers and risk associated with them should subside. However, consumer concerns relating to privacy and control of personal data are huge and the industry as a whole should work toward creating and implementing some best practices that would help gain consumer trust and make the adoption of embedded tech more seamless.
Author contribution statement
Harsha Gangadharbatla: Conceived and designed the experiments; Performed the experiments; Analyzed and interpreted the data; Contributed reagents, materials, analysis tools or data; Wrote the paper.
Funding statement
This research did not receive any specific grant from funding agencies in the public, commercial, or not-for-profit sectors.
Competing interest statement
The authors declare no conflict of interest.
Additional information
No additional information is available for this paper.
Footnotes
This study was approved by the Human Subjects Institutional Review Board (IRB) of the University of Colorado (#17-0063).
References
- Adrian . 2016. Biohacking: A New Type of Body modification. Ripley’s Believe it or Not.http://www.ripleys.com/weird-news/biohacking/ February 18. Retrieved online December 29, 2017 from. [Google Scholar]
- Agarwal R., Prasad J. Are individual differences germane to the acceptance of new information technologies? Decis. Sci. J. 1999;30(2):361–391. [Google Scholar]
- Ajzen I. Open University Press; Milton Keynes, England: 1988. Attitudes, Personality, and Behavior. [Google Scholar]
- Ajzen I., Fishbein M. Attitude-behavior relations: a theoretical analysis and review of empirical research. Psychol. Bull. 1977;84(5):888. [Google Scholar]
- Ajzen I., Fishbein M. Prentice-Hall, Inc; Englewood Cliffs, NJ: 1980. Understanding Attitudes and Predicting Social Behavior. [Google Scholar]
- Allport G.W. In: “Attitudes,” in Handbook of Social Psychology. Murchison C., editor. Clark University Press; Worcester, MA: 1935. pp. 798–844. [Google Scholar]
- Angst C.M., Agarwal R. Adoption of electronic health records in the presence of privacy concerns: the elaboration likelihood model and individual persuasion. MIS Q. 2009;33(2):339–370. [Google Scholar]
- Arthur C. The Guardian- Technology; 2013. Music to Your Ears? Try a Headphones Implant like Rich Lee.https://www.theguardian.com/technology/2013/jul/04/headphones-implanted-ear-grinder-rich-lee July 4. Retrieved online December 29, 2017 from: [Google Scholar]
- Bagozzi R.P., David F.D., Warshaw P.R. User acceptance of computer technology: a comparison of two theoretical models. Manag. Sci. 1989;35(8):982–1003. [Google Scholar]
- Bandura Albert. Self-efficacy mechanism in human agency. Am. Psychol. 1982;37(2):122–147. [Google Scholar]
- Bandura A. Perceived self-efficacy in cognitive development and functioning. Educ. Psychol. 1993;28(2):117–148. [Google Scholar]
- Bloom J. The Guardian- Technology; 2009. The Geneticist in the Garage.http://www.synbiosafe.eu/uploads/pdf/09_03_Guardian_geneticist_in_the_garage.pdf March 19. Retrieved online December 29, 2017 from: [Google Scholar]
- Bruner G.C., II, James K.E., Hensel P.J. Vol. III. American Marketing Association; Chicago: 2001. Marketing Scales Handbook. [Google Scholar]
- Burton-Jones A., Hubona G.S. Individual differences and usage behavior: revisiting a technology acceptance model assumption. ACM SIGMIS Data Base DATABASE Adv. Inf. Syst. 2005;36(2):58–77. [Google Scholar]
- Busch T. Gender differences in self-efficacy and attitudes toward computers. J. Educ. Comput. Res. 1995;12:147–158. [Google Scholar]
- Chau P.Y.K., Hui K.L. Identifying early adopters of new it products: a case of Windows 95. Inf. Manag. 1998;33(5):225–230. [Google Scholar]
- Chuah S.H.W., Rauschnabel P.A., Krey N., Nguyen B., Ramayah T., Lade S. Wearable technologies: the role of usefulness and visibility in smartwatch adoption. Comput. Hum. Behav. 2016;65:276–284. [Google Scholar]
- Cropanzano R., Mitchell M.S. Social exchange theory: an interdisciplinary review. J. Manag. 2005;31(6):874–900. [Google Scholar]
- Czaja S.J., Charness N., Fisk A.D. Factors predicting the use of technology: findings from the center for research and education on aging and technology enhancement (CREATE) Psychol. Aging. 2006;21(2):333–352. doi: 10.1037/0882-7974.21.2.333. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Davis F.D. Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Q. 1989;13(3):319–340. [Google Scholar]
- Davis F.D., Bagozzi R.P., Warshaw P.R. User acceptance of computer technology: a comparison of two theoretical models. Manag. Sci. 1989;35(8):982–1003. [Google Scholar]
- Delfanti A. Innsbruck University Press; Innsbruck: 2012. Tweaking Genes in Your Garage: Biohacking between Activism and Entrepreneurship; pp. 163–176. [Google Scholar]
- Dwyer C., Hiltz S., Passerini K. AMCIS 2007 Proceedings. 2007. Trust and privacy concern within social networking sites: a comparison of Facebook and MySpace; p. 339. [Google Scholar]
- Eastin M.S., LaRose R. Internet self-efficacy and the psychology of the digital divide. J. Computer-Mediated Commun. 2000;6(1) [Google Scholar]
- Engelking C. Discover Magazine; 2015. Zoom Contact Lens Magnifies Objects at the Wink of an Eye.http://blogs.discovermagazine.com/d-brief/2015/02/17/zoom-contact-lens/#.Wkhs2VQ-euU Retrieved on December 30, 2017 from: [Google Scholar]
- Francis E., Jarvis R. ABC News; 2017. Tech Company Workers Agree to Have Microchips Implanted in Their Hands.http://abcnews.go.com/Technology/tech-company-workers-agree-microchips-implanted-hands/story?id=48818529 July 24. Retrieved online December 29, 2017 from. [Google Scholar]
- Gangadharbatla H. Facebook me: collective self-esteem, need to belong, and internet self-efficacy as predictors of the iGeneration’s attitudes toward social networking sites. J. Interact. Advert. 2008;8(2):5–15. [Google Scholar]
- Hong W., Thong J.Y., Wong W.M., Tam K.Y. Determinants of user acceptance of digital libraries: an empirical examination of individual differences and system characteristics. J. Manag. Inf. Syst. 2002;18(3):97–124. [Google Scholar]
- Iivari J. The effects of self-efficacy on computer usage. OMEGA Int. J. Manag. Sci. 1995;23(6):587–605. [Google Scholar]
- Illulife . 2016. TransHumanism & Biohacking - Everything You Should Know about Transcending the Limits of the Human Body, Illulife.https://www.illulife.com/6-things-know-biohacking-transcending-limits-human-body/#ixzz52nIjAhIt August 27. Retrieved online December 29, 2017 from. [Google Scholar]
- Im I., Kim Y., Han H.J. The effects of perceived risk and technology type on users’ acceptance of technologies. Inf. Manag. 2008;45(1):1–9. [Google Scholar]
- Kesharwani A., Singh Bisht S. The impact of trust and perceived risk on internet banking adoption in India: an extension of technology acceptance model. Int. J. Bank Market. 2012;30(4):303–322. [Google Scholar]
- King W.R., He J. A meta-analysis of the technology acceptance model. Inf. Manag. 2006;43(6):740–755. [Google Scholar]
- Legris P. Why do people use information technology? A critical review of the technology acceptance model. Inf. Manag. 2003;40:191–204. [Google Scholar]
- Li Y.H., Huang J.W. Applying theory of perceived risk and technology acceptance model in the online shopping channel. World Acad. Sci. Eng. Technol. 2009;53(1):919–925. [Google Scholar]
- Lindquist G.S., Save-Soderbergh J. Girls will be girls - especially among boys: competitive behavior in the daily double on Jeopardy. Econ. Lett. 2011;112(2):158–160. [Google Scholar]
- Lu J., Yu C.S., Liu C., Yao J.E. Technology acceptance model for wireless Internet. Internet Res. 2003;13(3):206–222. [Google Scholar]
- Luarn P., Lin H.H. Toward an understanding of the behavioral intention to use mobile banking. Comput. Hum. Behav. 2005;21(6):873–891. [Google Scholar]
- MacKenzie S., Spreng R.A. How does motivation moderate the impact of central and peripheral processing on brand attitudes and intentions? J. Consum. Res. 1992;18:519–529. (March) [Google Scholar]
- Martins C., Oliveira T., Popovič A. Understanding the Internet banking adoption: a unified theory of acceptance and use of technology and perceived risk application. Int. J. Inf. Manag. 2014;34(1):1–13. [Google Scholar]
- Mohr C.N. Learning English; 2017. US Company Is Putting Microchips in its Employees.https://learningenglish.voanews.com/a/microchip-employees-us-company/3967947.html August 2. Retrieved online December 29, 2017 from: [Google Scholar]
- Monks K. CNN; 2014. Forget Wearable Tech, Embeddable Implants Are Already Here.http://www.cnn.com/2014/04/08/tech/forget-wearable-tech-embeddable-implants/ April 9. Retrieved online December 13, 2016 from. [Google Scholar]
- Morrongiello B.A., Rennie H. Why do boys engage in more risk taking than girls? The role of attributions, beliefs, and risk appraisals. J. Pediatr. Psychol. 1998;23(1):33–44. doi: 10.1093/jpepsy/23.1.33. [DOI] [PubMed] [Google Scholar]
- Murgia M. The Telegraph; 2016. Toddler Gets World First Adult Kidney Transplant Using 3D Printing.http://www.telegraph.co.uk/technology/2016/01/26/toddler-gets-world-first-adult-kidney-transplant-using-3d-printi/ Retrieved online December 30, 2017 from. [Google Scholar]
- Norton S. 2016. The Beginners’ Guide to Biohacking. iNews, November 19.https://inews.co.uk/essentials/lifestyle/wellbeing/beginners-guide-biohacking/ Retrieved online December 13, 2016 from. [Google Scholar]
- Pavlou P.A. Consumer acceptance of electronic commerce: integrating trust and risk with the technology acceptance model. Int. J. Electron. Commer. 2003;7(3):101–134. [Google Scholar]
- Ramirez S., Liu X., Lin P.A., Suh J., Pignatelli M., Redondo R.L.…Tonegawa S. Creating a false memory in the hippocampus. Science. 2013;341(6144):387–391. doi: 10.1126/science.1239073. [DOI] [PubMed] [Google Scholar]
- Ricker Thomas. 2016. Elon Musk: We Are Already Cyborgs, the Verge.https://www.theverge.com/2016/6/2/11837854/neural-lace-cyborgs-elon-musk June 2. Retrieved online December 29, 2017 from. [Google Scholar]
- Rogers E.M. fifth ed. Free Press; New York: 2003. Diffusion of Innovations. [Google Scholar]
- Sánchez R.A., Hueros A.D. Motivational factors that influence the acceptance of Moodle using TAM. Comput. Hum. Behav. 2010;26(6):1632–1640. [Google Scholar]
- Saxena M. 2016. Why Advertisers Need to Take Wearables Market More Seriously.https://www.entrepreneur.com/article/275167 Entrepreneur India, May 4. Retrieved online November 17, 2018 from. [Google Scholar]
- Szondy D. 2013. Mind-controlled Quadcopter Flies Using Imaginary Fists. New Atlas (Gizmag)https://newatlas.com/university-minnesota-mind-control-uav/27798/ Retrieved online from: [Google Scholar]
- Tarhini A., Hone K., Liu X. Measuring the moderating effect of gender and age on e-learning acceptance in England: a structural equation modeling approach for an extended technology acceptance model. J. Educ. Comput. Res. 2014;51(2):163–184. [Google Scholar]
- Venkatesh V., Morris M.G., Davis G.B., Davis F.D. User acceptance of information technology: toward a unified view. MIS Q. 2003;27(3):425–478. [Google Scholar]
- Venkatesh V., Thong J.Y., Xu X. Consumer acceptance and use of information technology: extending the unified theory of acceptance and use of technology. MIS Q. 2012;36(1):157–178. [Google Scholar]
- Wang Y.S., Wu M.C., Wang H.Y. Investigating the determinants and age and gender differences in the acceptance of mobile learning. Br. J. Educ. Technol. 2009;40(1):92–118. [Google Scholar]
- Wolf Gary. Conde Nast Digital; 2009. Know Thyself: Tracking Every Facet of Life, from Sleep to Mood to Pain, 24/7/365.Wired.comhttps://www.wired.com/2009/06/lbnp-knowthyself/ Retrieved online November 14, 2018 from. [Google Scholar]
- Wu W.Y., Ke C.C. An online shopping behavior model integrating personality traits, perceived risk, and technology acceptance. Soc. Behav. Pers. Int. J. 2015;43(1):85–97. [Google Scholar]
- Zhang K., Katona Z. Contextual advertising. Market. Sci. 2012;31(6):980–994. [Google Scholar]